- Rollback of malicious changes in Azure AD
- Alerts on IOCs for advanced AD threat detection
- Easy-to-understand reports of overall security posture
- Regulatory compliance reports for GDPR, HIPAA, PCI, and SOX
- Integration with Splunk and Microsoft Sentinel to provide meaningful context to AD security data
- Strengthen AD and Azure AD security with comprehensive threat detection
Securing Active Directory (AD)—the common target in 9 out of 10 cyberattacks—is difficult. Many organizations have legacy AD environments with accumulated misconfigurations that attackers love to exploit. And although 90% of organizations worldwide use AD as their primary identity store, Gartner research shows that only 33% have any sort of AD security system in place. Add Azure Active Directory (Azure AD)—now called Entra ID—into the mix, and the challenges increase.
Related reading
Tracking malicious activity across Azure AD and on-prem AD is notoriously difficult. On-prem and cloud teams are often siloed, complicating the detection of changes across the environment.
Semperis Directory Services Protector (DSP) makes securing your hybrid AD environment easier. Plus, we’ve just released new improvements that help IT and security teams put AD and Azure AD on autopilot—saving precious resources while improving overall AD security.
Let’s dive into the new DSP capabilities that help organizations secure AD and Azure AD from cyberattacks.
1. Rollback of malicious changes in Azure AD
To mitigate an attack on your hybrid AD environment, you need an effective way to undo malicious changes in Azure AD. Semperis DSP offers rollback of unwanted or malicious changes to users, groups, or roles in Azure AD. You can also restore Azure AD objects that are soft-deleted (i.e., deleted but still in the Azure AD recycle bin), giving you the ability to recover lost or deleted data.
2. Alerts on IOCs for advanced AD threat detection
Indicators of compromise (IOCs) in DSP let you know when you’ve been breached so that you can detect threats early and act quickly to stop attackers in their tracks. IOCs also provide crucial data to accurately locate the affected area and reduce downtime.
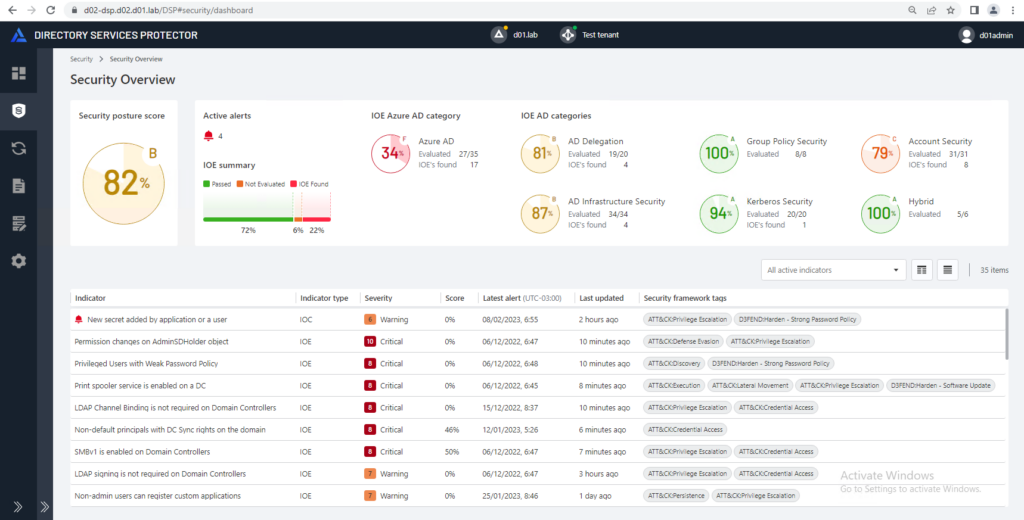
3. Easy-to-understand reports of overall security posture
DSP has a streamlined flow for creating reports. An overall security posture report provides a visual snapshot of key security indicators to share with business leaders. This report includes:
- A security posture score of up to 100%
- A summary of indicator of exposure (IOE) status (found, not evaluated, or passed)
- Individual category scores for Azure AD and on-prem AD categories including account security, Kerberos security, Group Policy, and more
DSP’s security posture scoring method is based on a variety of factors, including:
- Potential consequences if an attacker exploits the vulnerability
- How easy the vulnerability is to exploit
- The overall prevalence of the vulnerability in the environment
Each indicator includes a severity rating (level and number) that reflects the potential impact of the vulnerability on your security posture, availability, and performance. This severity rating is then used in the scoring formula to calculate the overall risk posed by the vulnerability.
4. Regulatory compliance reports for GDPR, HIPAA, PCI, and SOX
DSP includes templates for dozens of common compliance reports, which you can upload from the Semperis web service or import through the DSP PowerShell module. These reports, tailored to GDPR, HIPAA, PCI, and SOX requirements, provide information about AD configuration and security that is relevant to ensuring regulatory compliance. For example, the report templates for GDPR include lists of all deleted computer accounts in AD and lists of group status changes in the past 30 days.
5. Integration with Splunk and Microsoft Sentinel to provide meaningful context to AD security data
DSP has always detected IOCs that bypass traditional log- or event-based solutions. To do so, DSP uses multiple data sources, including the AD replication stream. DSP then forwards suspicious changes, along with meaningful context, to your security information and event management (SIEM) system. Building on that capability, DSP now brings AD security data into familiar Splunk views. DSP provides predefined dashboards that display AD change data, DSP security indicator data, and DSP notification rule events. You can also use DSP’s predefined alerts as templates for building custom alerts for security orchestration, automation, and response (SOAR) and ticketing systems.
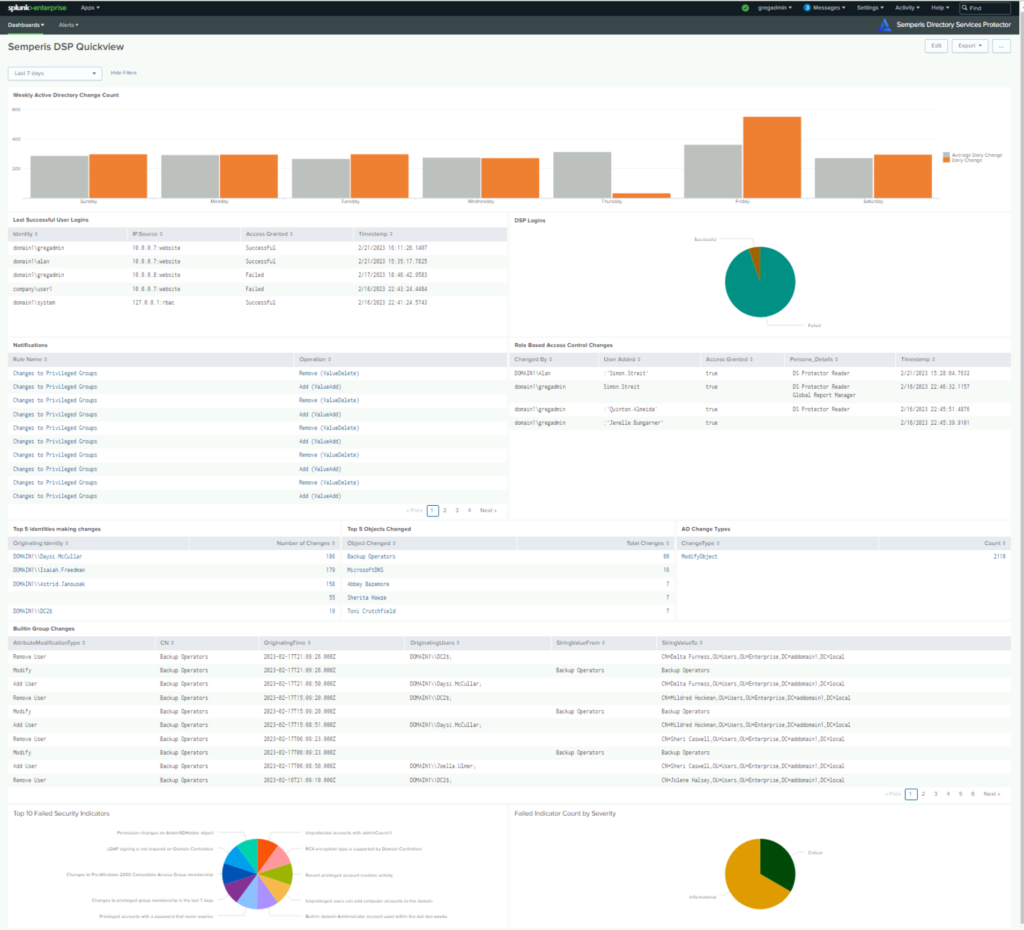
We’ve also expanded DSP’s integration with Microsoft Sentinel, providing new workbooks that let you view DSP information, such as AD change data and DSP notification rule events, within the Microsoft Sentinel interface.
Strengthen AD and Azure AD security with comprehensive threat detection
Attacks against AD and Azure AD won’t end anytime soon. Ransomware-as-a-service (RaaS) groups such as LockBit and Vice Society are relentlessly targeting hybrid AD systems. It’s tough for IT and security teams to stay ahead of emerging threats. But with the new capabilities we’re introducing in DSP—built by a team of AD security experts—we hope to make defending your hybrid AD system against these attacks a little easier.
