Welcome to AD Security 101, a series that covers the basics of Active Directory (AD) security. This week, we look at primary group IDs and how unnecessary changes to them can complicate account management. Attackers can also exploit primary group IDs to introduce security risks, including privilege escalation, and to cloak their membership in a privileged group, hiding their presence and activities in the network and evading security monitoring.
What are primary group IDs?
In AD, every user account is associated with a primary group ID, which determines the user’s default group membership. The primary group ID in AD is a relic of Portable Operating System Interface (POSIX) standard compliance, which was designed to enable cross-platform compatibility among different operating systems.
The primary group ID defines the default group membership for a user account. By default, when a user account is created in AD, it becomes a member of the Domain Users group, which becomes the user’s primary group. This process is automatic and helps streamline access control and resource management within the AD environment.
In modern Windows environments, the primary group ID doesn’t play as substantial a role as it once did. Group membership and permission management strategies have evolved in Windows AD, which now offers more granular and flexible mechanisms for access control. The primary group ID becomes essential when Services for Macintosh or POSIX-compliant applications are involved. These applications rely on POSIX standards, where the primary group ID is used for file and directory ownership and permissions management. Unless using these services, there is no need to change the primary group from Domain Users.
Risks associated with primary group IDs
An attacker who can modify a user’s primary group ID can effectively alter their perceived role and privileges within the network. For instance, if an attacker changes a compromised standard user’s primary group ID to that of the Domain Admins group, they can gain administrative access rights within the AD environment. This can potentially give the attacker extensive control over the network. They can then modify system configurations, manipulate user account privileges, access sensitive data, and more—all while appearing as a regular user.
This cloaking tactic can also enable attackers to evade detection by security tools. By altering the primary group ID, attackers can circumnavigate typical access control mechanisms, effectively disguising their malicious activities as routine actions performed by regular users. This tactic makes their activities less likely to be flagged as suspicious, providing them more time to compromise the network.
Even more troubling, this increased timeframe can enable the attacker to perform a variety of malicious actions, such as data exfiltration, system sabotage, or planting additional backdoors for future access. These actions can continue undetected until such time as the unusual behavior is discovered and correctly interpreted.
How do cyberattackers exploit primary group IDs?
There are multiple ways in which an attacker can modify a user’s primary group ID in AD. These methods generally require certain levels of privilege or access, so such modifications typically indicate some security breakdown.
- Compromised credentials: If an attacker obtains the login information for an account with sufficient privileges, such as a domain administrator or an account operator, they can use these credentials to log in to the AD system and change a user’s primary group ID. Such compromise can be achieved through a brute force attack, phishing, or another form of social engineering.
- AD vulnerabilities: Attackers can exploit vulnerabilities in the AD system or in the network as a whole. For example, an attacker can exploit unpatched software vulnerabilities to gain elevated privileges, which they can then use to alter a user’s primary group ID.
- Privilege escalation: Attackers can gain initial access to the network by using a lower-privilege account, then exploit a vulnerability or misconfiguration to increase the account’s privileges.
How can you detect abuse of primary group IDs?
These attack vectors underline the necessity of maintaining good cybersecurity hygiene:
- Regularly patch and update software.
- Monitor for and promptly respond to suspicious activities.
- Enforce the principle of least privilege.
- Educate users about potential social engineering tactics.
To mitigate the risks associated with primary group IDs, consider using a multi-tiered approach to AD security with a focus on proactive auditing and real-time monitoring.
Proactive auditing in AD means a regular analysis of AD logs to detect anomalies. In this context, any unexpected changes in user primary group IDs could point to unauthorized or malicious attempts to alter a user’s privileges or mask their true group membership.
A typical red flag might be seeing a standard user becoming part of an administrative group, indicating a potential security breach. Proactive auditing allows IT professionals to identify such inconsistencies early, preventing them from escalating into major issues. Tools such as Purple Knight can help by automating the monitoring of changes in the AD environment and providing insights that might otherwise be overlooked in a manual review. Figure 1 shows a report finding an indicator of exposure (IOE) related to primary group IDs.
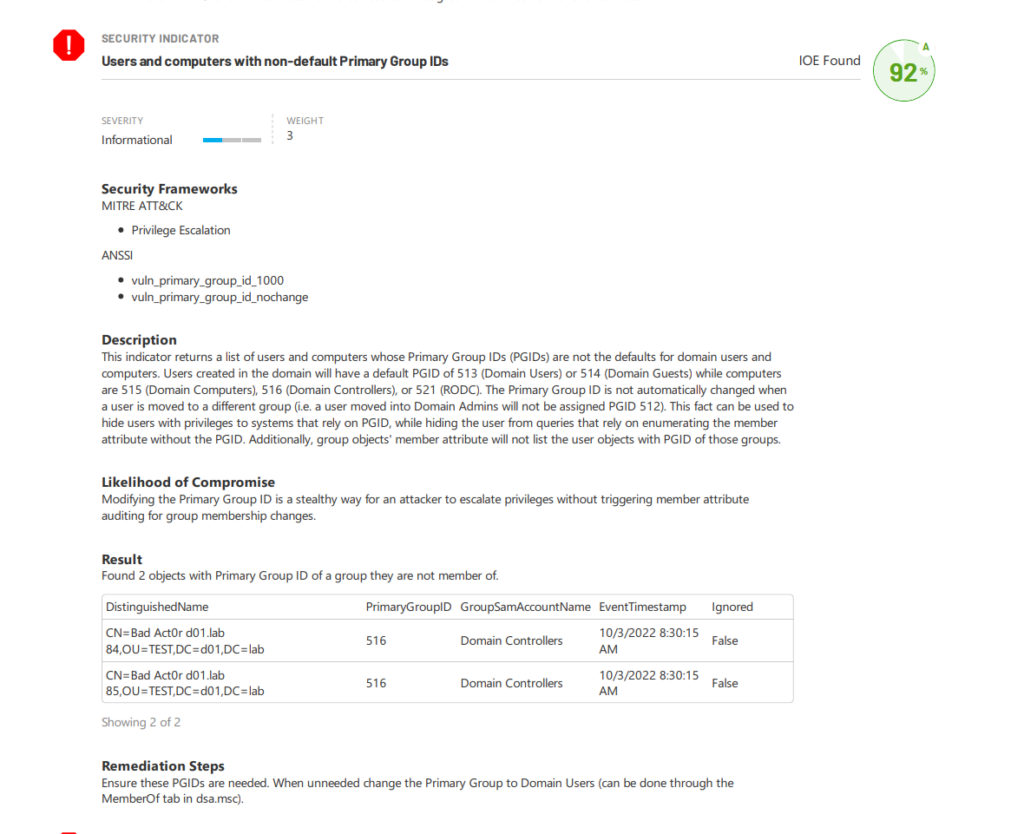
Real-time monitoring requires the use of advanced threat-detection tools that can alert administrators to changes as they occur. These tools continually assess the AD environment, looking for activities such as unexpected alterations in a user’s primary group ID, which could signal a potential security breach or insider threat. Semperis Directory Services Protector (DSP), for example, can perform real-time monitoring of changes in the AD environment, giving administrators the power to react promptly when an anomaly is detected.
Maintain insight into primary group IDs
A deep comprehension of the primary group ID’s role in Active Directory is crucial for both IT managers and cybersecurity professionals. This knowledge equips them with valuable insights into AD’s architecture and operational mechanisms, provides guidance for the effective administration of user accounts, and elucidates the potential security implications inherent in account configurations. With this understanding, they can better safeguard the IT infrastructure and contribute to the organization’s overall cybersecurity resilience.
The use of robust auditing and monitoring tools is also crucial. They can help detect unusual activities, such as changes to a user’s primary group ID, which could indicate a security breach. Through early detection, appropriate countermeasures can be taken before the attacker can cause significant damage.
Learn more about AD security
