[Editor’s note: This article is a guest post by TAG CEO and founder Ed Amoroso.]
Any observer of public sector cybersecurity will recognize the serious challenges in information technology (IT) protections for U.S. public sector agencies over the past few decades. Major incidents, such as the 2015 data breach at the US Office of Personnel Management (OPM), as well as nation-state breaches of major agencies, such as the U.S. State Department, illustrate the continuing challenge for public sector officials.
How does Active Directory affect public sector cybersecurity?
It should be no surprise that public sector agencies are susceptible to the same cybersecurity vulnerabilities as every other sector. Being part of the public sector appears to offer no great advantage in terms of threat avoidance or cyber protection. To that end, it is reasonable to assume that one of the most common and intense public sector cybersecurity vulnerabilities involves weaknesses in Microsoft Active Directory (AD).
AD is the basis for identity management and access control within most public sector agencies.
- The integrity of AD is vital to ensuring that only authorized personnel can access sensitive government information, critical systems, and classified resources.
- A breach in AD security can compromise national security, expose citizen data, and disrupt essential public services.
- Public sector agencies face strict compliance and regulatory mandates that require AD security protocols.
- The complexity of government IT ecosystems and the rise of hybrid work environments further heighten the need for advanced AD security measures.
Public sector organizations must, therefore, prioritize AD protection to prevent unauthorized access, ensure compliance, and maintain operational continuity in the face of evolving cyber threats.
Learn more about hardening Active Directory
What is AD attack detection?
Achieving a sufficient level of AD security depends on a wide range of functions, controls, and services. In turn, these depend not only on good security capabilities, but also on proper day-to-day administration. That said, our observation is that the most intensely difficult aspect of AD security for the public sector involves the detection and mitigation of attacks before, during, and after their initiation on a live target.
AD attack detection involves identifying malicious activities targeting AD systems. Such activities include:
- Unauthorized logins
- Privilege escalations
- Modifications to directory structures
Effective AD attack detection relies on continuous monitoring, the use of artificial intelligence, and behavioral analytics to flag suspicious activities. These capabilities enable rapid detection of anomalies, such as an unusual increase in access privileges or changes to group policies.
Given the critical role of AD in managing access to government systems, real-time attack detection is essential for minimizing the impact of cyberattacks. Early detection significantly enhances incident response efforts, minimizing the risk of major breaches. By proactively identifying threats, public sector agencies can:
- Reduce dwell time
- Limit attacker movements within networks
- Take immediate action to protect sensitive data and services
Current identity-related threats to public sector cybersecurity
As suggested above, public sector agencies are targets because of the value of their resources. Ransomware attacks are among the most prevalent threats, often leveraging vulnerabilities in AD to spread across government systems and disrupt services.
These attacks frequently aim to paralyze infrastructure or extort agencies for large sums in exchange for decrypting essential data. Nation-state actors targeting AD credentials for espionage is also a serious concern.
Additionally, many public sector IT environments are legacy systems, which often contain unpatched vulnerabilities and misconfigurations that attackers exploit. The shift to remote work has further complicated security efforts, widening the attack surface and exposing AD to potential breaches. These evolving threats underscore the urgent need for robust AD security in public sector agencies.
More generally, the public sector cybersecurity problem points to overall weaknesses in the identity and access management (IAM) ecosystems put in place to manage user identities and to integrate with AD. This challenge should be no surprise to practitioners since IAM represents one of the most difficult aspects of modern enterprise security. Public sector security is no different.
Federal mandates for public sector cybersecurity
Various federal mandates in the United States do exist to enforce public sector cybersecurity measures, especially within IAM and related systems such as directory services. One of the primary legislative frameworks is the Federal Information Security Modernization Act (FISMA), which requires federal agencies to protect information systems and user data, including identity management.
Under FISMA, agencies must implement safeguards such as multifactor authentication (MFA) and user access controls to ensure secure access to government resources. In addition, Executive Order 14028 (Improving the Nation’s Cybersecurity) has driven the adoption of Zero Trust Architecture (ZTA), mandating that agencies shift from perimeter-based security to a more identity-centric approach that assumes every access request is untrusted until verified.
Public sector IAM systems are also regulated by mandates like NIST’s Special Publication 800-63 on Digital Identity Guidelines, which establishes best practices for the identity proofing, authentication, and lifecycle management of federal users. These guidelines directly impact the security of public sector identity systems and directory services, including enforcing stringent verification processes and improving identity federation mechanisms.
Thus, although mandates for improved AD are not explicitly present, the broader implications of these policies suggest a push for securing enterprise identity systems. AD plays a crucial role in managing identities and enforcing policies across the public sector, including contractors. As part of the government’s emphasis on Zero Trust, the Cybersecurity and Infrastructure Security Agency (CISA) has released best practices for securing identity and access controls, encouraging agencies and contractors to adopt more robust directory security strategies.
Using Semperis for AD security in the public sector
Some good news is that although IAM will continue to be a complex endeavor (solutions to which are beyond the scope of this paper), we can report that effective options exist for public sector groups, including federal agencies, to reduce the risks associated with their AD deployment. This should be a welcome situation given the major role that AD plays in the overall identity environment for most agencies.
In particular, cybersecurity company Semperis offers a suite of AD security solutions tailored to the needs of public sector organizations, focusing on real-time monitoring, rapid attack detection, and disaster recovery. Their platform detects unauthorized changes to AD, such as privilege escalations or modifications to group policies, and provides automated alerts to security teams, ensuring immediate action can be taken.
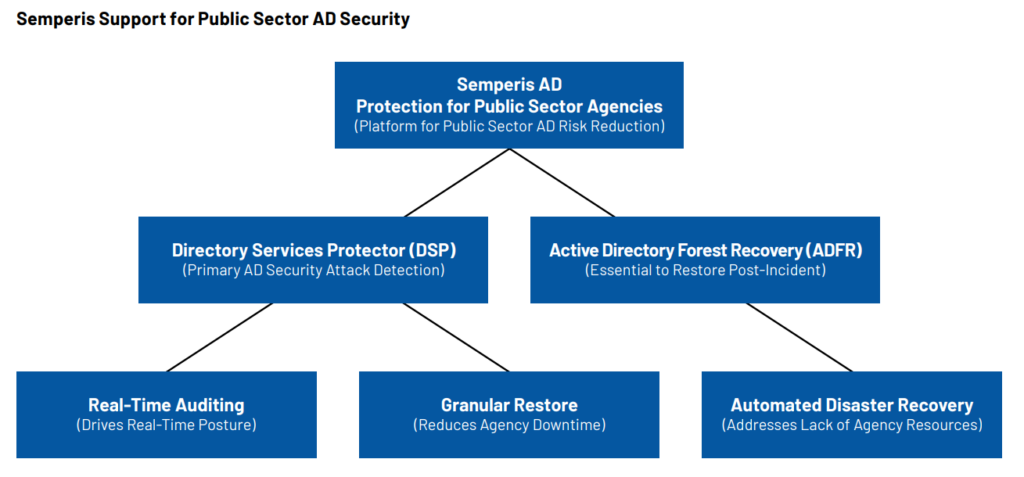
Semperis provides public sector agencies with robust AD recovery tools that minimize downtime and prevent the spread of ransomware. If an AD environment is compromised, Semperis’ automated recovery capabilities enable organizations to restore affected directories to a pre-compromised state quickly. For agencies bound by strict compliance and uptime requirements, rapid response and recovery from AD attacks is essential.
Strengthen public sector cybersecurity with an AD hardening action plan
TAG’s advice is that public sector CISOs should develop a security strategy that emphasizes AD hardening, continuous monitoring, and incident response. A key first step is conducting regular security assessments to identify AD misconfigurations, unpatched vulnerabilities, and areas that could be exploited. Deploying advanced AD security solutions, like the platform from Semperis, can enable agencies to detect attacks in real-time, ensuring rapid response and mitigation. Agencies interested in engaging with Semperis should contact the company directly to identify the best available contract vehicle for proof-of-concept (POC) deployment.
Explore expert strategies for hardening Active Directory
About TAG: Recognized by Fast Company, TAG is a trusted next-generation research and advisory company that utilizes an AI-powered SaaS platform to provide on demand insights, guidance, and recommendations to enterprise teams, government agencies, and commercial vendors in cybersecurity, artificial intelligence, and climate science.

