Cybersecurity agencies from the Five Eyes alliance, including CISA and the NSA, are urging organizations to strengthen security around Microsoft Active Directory (AD), a prime target for cyberattackers. The alliance’s recent report highlights more than a dozen tactics that threat actors use to exploit AD. Among these common techniques is the DCSync attack.
What is a DCSync attack?
A DCSync attack is an attack technique that is typically used to steal credentials from an AD database. The attacker impersonates a domain controller (DC) to request password hashes from a target DC, using the Directory Replication Services (DRS) Remote Protocol. The attack can be used to effectively “pull” password hashes from the DC, without needing to run code on the DC itself. This type of attack is adept at bypassing traditional auditing and detection methods.
Note that the attacker must first gain access to an account with high-level permissions, such as Domain Admin or an account with the ability to replicate data from the DC. This action requires the following permissions on the Domain Naming Context:
- Replicate Directory Changes
- Replicate Directory Changes All
Once the attacker has the necessary privileges, they send a request to a DC, asking it to replicate user credentials. This process mimics legitimate replication traffic, which DCs use to synchronize data across the network.
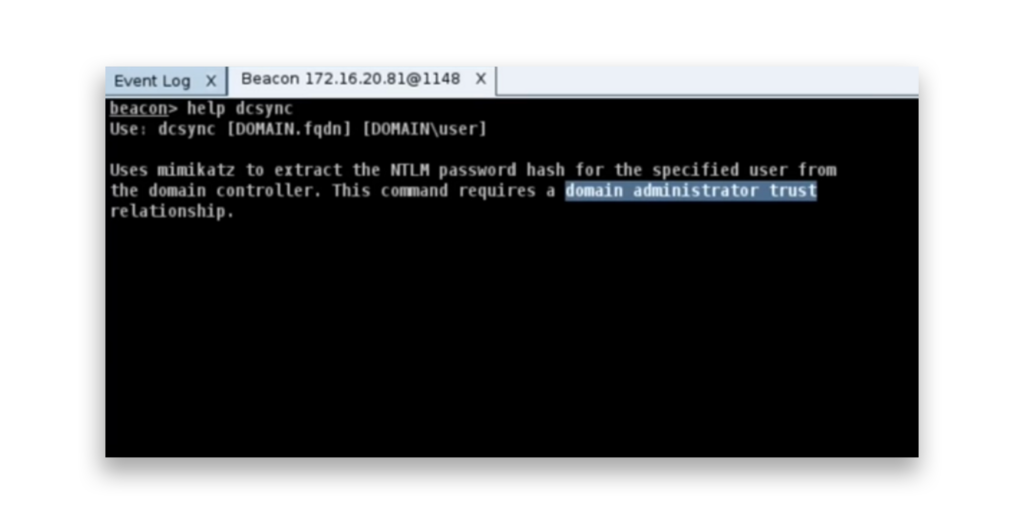
This image shows the help command output for DCSync in Cobalt Strike, explaining how to use mimikatz to extract NT password hashes for specified users from a domain controller. The command requires domain administrator privileges to function.
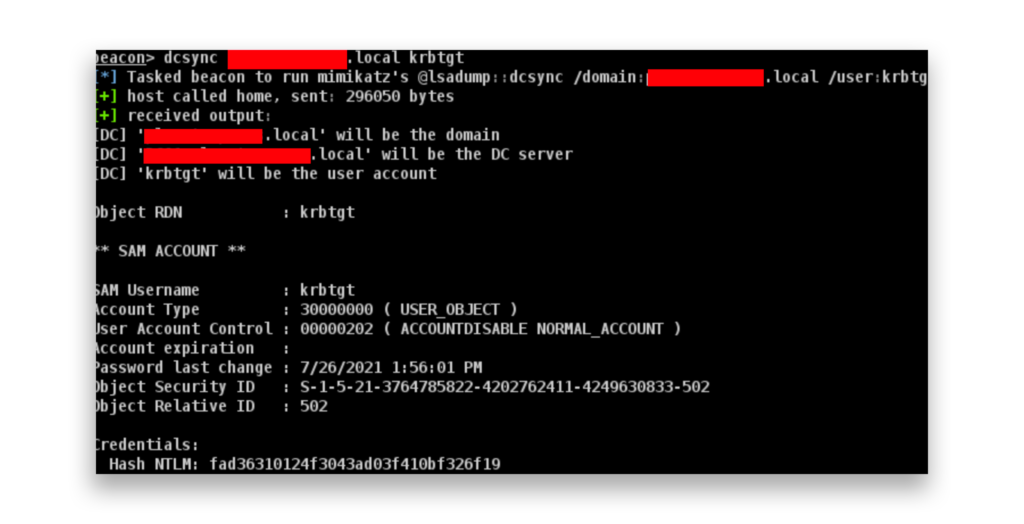
Here is the output of a DCSync command in Cobalt Strike to extract the NT hash of the KRBTGT account from the domain controller.
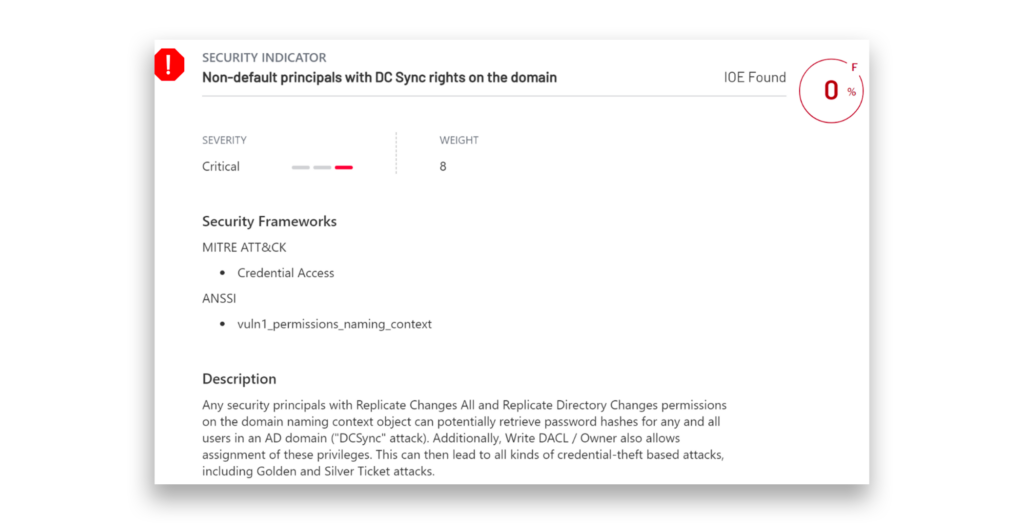
How can you defend your environment from a DCSync attack?
The best place for defenders to start defending their environments against a DCSync attack is to leverage the free tool Purple Knight to identify non-default principals that have DCSync permissions on the Domain Naming Context.
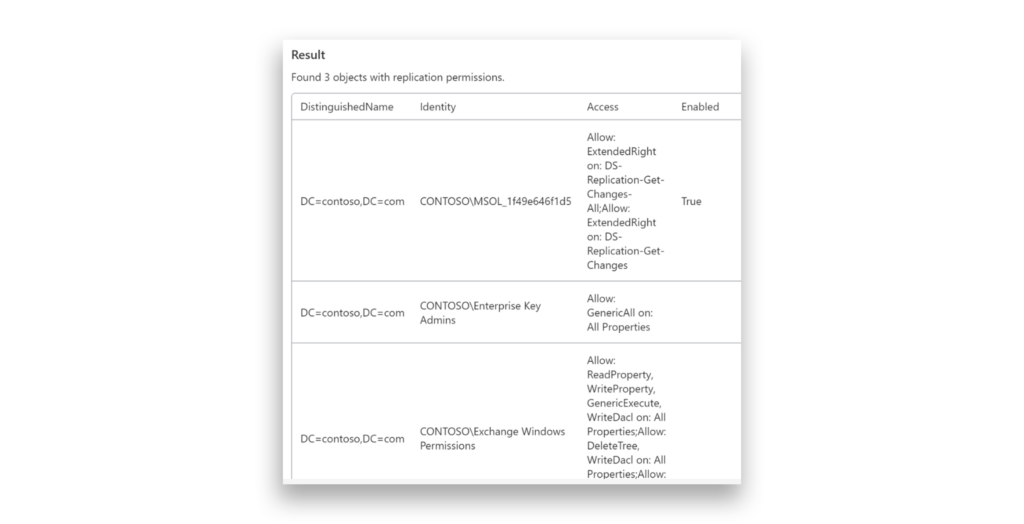
Here’s something we often see in customer environments: Enterprise Key Admins with full control over the Domain Naming Context and Exchange Windows Permissions with the ability to modify permissions on it. This scenario is dangerous, as it can unintentionally lead to granting DCSync permissions—a serious security risk.
Let’s walk through the remediation process, using Enterprise Key Admins as an example.
When running adprep /domainprep on Windows Server 2016, an unintended access control entry (ACE) is added to the security descriptor of the Domain Naming Context for the Enterprise Key Admins group (SID = -527). This ACE incorrectly grants full access to the naming context and all its child objects. The intended ACE should provide only ReadProperty and WriteProperty permissions for the msDS-KeyCredentialLink attribute.
The following figure shows an example of a PowerShell script that addresses the issue by removing Full Control permissions from the Enterprise Key Admins group, ensuring that this group is granted only Read/Write access to the msDS-KeyCredentialLink attribute.
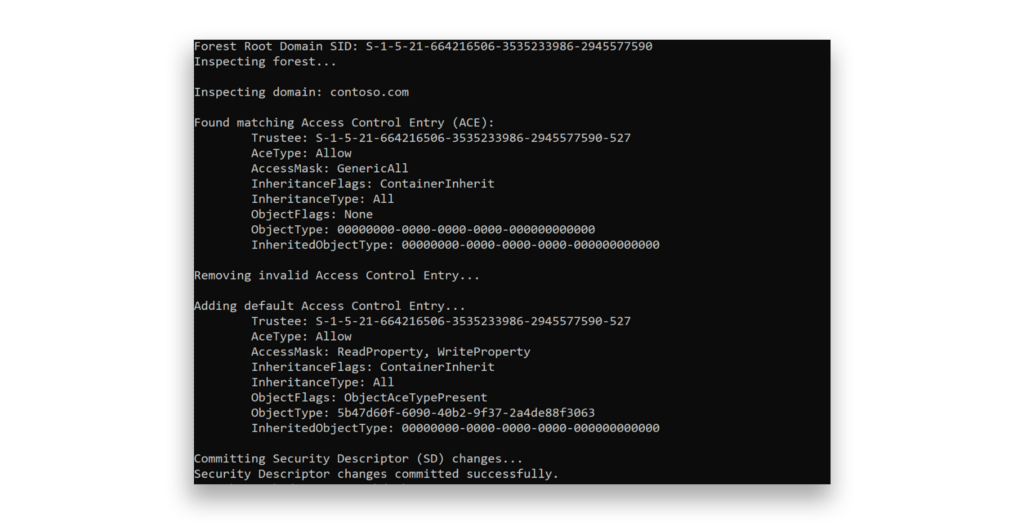
After adjusting the permissions for Enterprise Key Admins, we notice an improvement in our security score for this specific indicator of exposure (IOE).
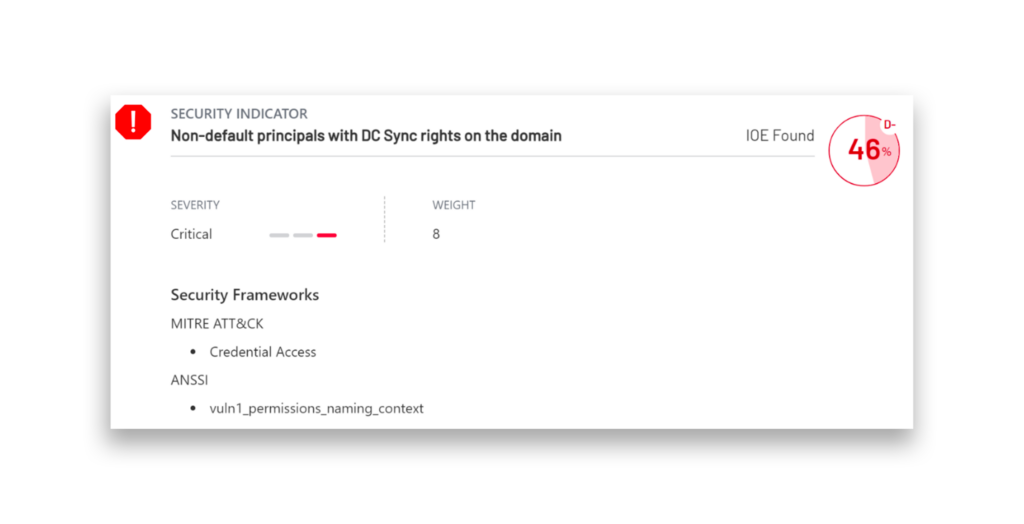
Semperis DSP Intelligence includes a security indicator that continuously detects suspicious accounts in AD that have the special rights required for a DCSync attack. These permissions include Replicating Directory Changes and Replicating Directory Changes All. By default, only certain ACEs, such as Domain Admins, Enterprise Admins, DC computer accounts, and the AAD Connect user have these rights. Monitoring users that unexpectedly have these permissions can help you prevent unauthorized replication of directory data.
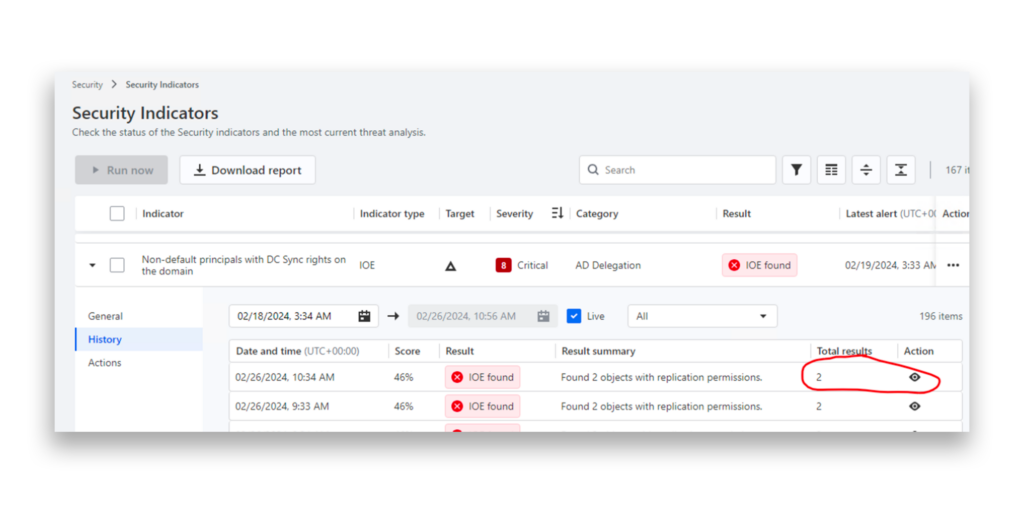
How can you detect a DCSync attack?
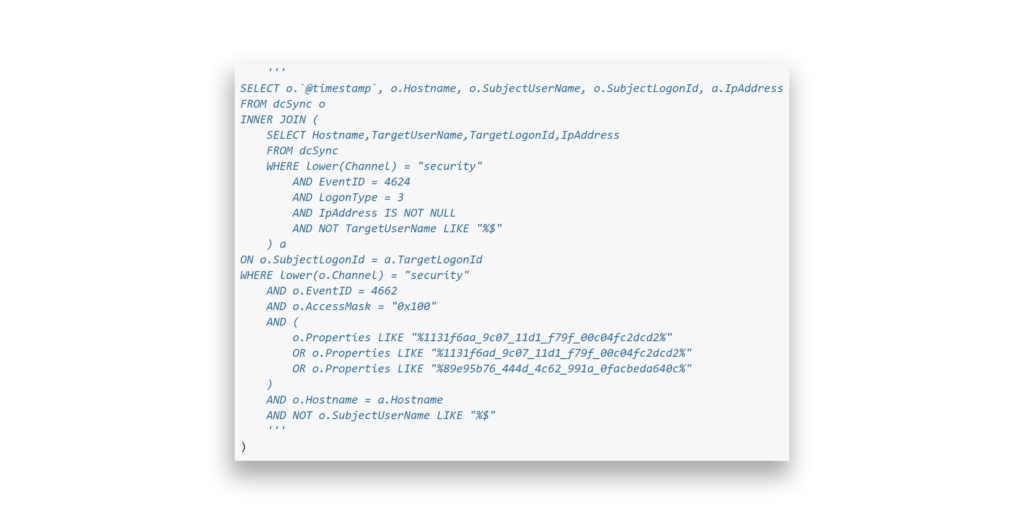
To detect DCSync activity, you can monitor the TargetLogonId from Event 4624 and correlate it with other security events tied to the same logon session. DCSync generates a Network Logon type (3) on the DC. By linking Event 4662 (which tracks directory access) with Event 4624 using the LogonId, defenders can identify the source IP of the DCSync request.
Threat actor profiles
The following threat actors have been known to utilize DCSync attacks in the wild.
- APT20 aka Crawling Taurus, TH3Bug, VIOLIN PANDA1
- Calypso aka Bronze Medley2
- Earth Lusca aka TAG-22, Charcoal Typhoon, CHROMIUM, ControlX (MITRE ATT&CK®Group G1006)3
- LAPSUS$ aka DEV-0537, Strawberry Tempest (MITRE ATT&CK Group G1004)4
- Leviathan aka MUDCARP, Kryptonite Panda, Gadolinium, BRONZE MOHAWK, TEMP.Jumper, APT40, TEMP.Periscope, Gingham Typhoon (MITRE ATT&CK Group G0065)5
- Mustang Panda aka TA416, RedDelta, BRONZE PRESIDENT (MITRE ATT&CK Group G0129)6
- UNC53307
DCSync attack tools
The following public tools, available on github.com, can be used to perform a DCSync attack.
- DSInternals PowerShell Module and Framework
- gentilkiwi/mimikatz
- secretsdump.py
Threat overview
ATT&CK Tactic: Credential Access
On July 9, 2024, a joint report by the Australian Cyber Security Centre and global agencies highlighted APT40 (also known as Leviathan), a Chinese state-sponsored group, for targeting government and private sector networks. The report mentioned that DCSync is part of APT40’s tradecraft, enabling them to impersonate DCs and steal password hashes from Active Directory.8
On April 4, 2024, Google Cloud published a report outlining how the threat actor UNC5330 exploited vulnerabilities CVE-2024-21893 and CVE-2024-21887 in Ivanti Connect Secure to infiltrate a victim’s network. They used an LDAP bind account to exploit a vulnerable Windows Certificate Template, creating a computer object and impersonating a domain administrator. This enabled them to execute a DCSync attack to obtain additional domain credentials for enabling lateral movement.9
On September 22, 2023, Palo Alto Networks’ Unit 42 released a report about the cyberespionage activities of the Stately Taurus group, also known as Mustang Panda, which targeted a Southeast Asian government between 2021 and 2023. The group infiltrated networks, accessing sensitive files and maintaining long-term persistence. A key part of their attack involved performing a DCSync attack, where they impersonated a DC to steal credentials.10
In September 2022, Trend Micro presented at HITCON on Earth Lusca, a Chinese APT group active since 2019. The group has been involved in cyberespionage, targeting sectors like government, media, and education across several countries. As part of their operations, they used DCSync attacks to impersonate DCs and steal password hashes from Active Directory.11
On March 22, 2022, Microsoft released a report on DEV-0537 (also known as LAPSUS$), a cybercriminal group known for data theft and extortion. They breached organizations using stolen credentials and used DCSync attacks to steal additional domain credentials, which enabled them to move laterally through networks and gain control over critical systems.12
On December 19, 2019, Fox-IT released a report about Operation Wocao, which exposed the activities of APT20, a Chinese state-sponsored hacking group. The report revealed that APT20 had been targeting industries like government, energy, and healthcare across multiple countries. One of their key techniques involved using a DCSync attack to steal credentials from Active Directory.13
On September 23, 2019, Avast identified a breach where the attacker used a DCSync (malicious directory replication) attack. Initially, a Microsoft ATA alert about a replication attempt from a VPN IP was dismissed as a false positive. After further review in October 2019, it was revealed that the attacker had compromised credentials, escalated privileges, and obtained Domain Admin rights.14
On July 9, 2019, Positive Technologies reported on the Calypso APT group, which had been targeting government agencies across multiple countries. The report highlighted that DCSync is part of Calypso’s attack methods, enabling them to impersonate DCs and extract password hashes from Active Directory.15
Semperis snapshot
DCSync is a well-known technique used by attackers to pull credentials from the Active Directory database, and reports show that it’s still a relevant threat today. Defenders can leverage tools like Purple Knight and DSP Intelligence to find any non-default accounts that have DCSync permissions on the Domain Naming Context. Note that this attack can be executed only when an attacker has Domain Admin or similar privileges. To reduce the risk, implement a tiered access model to help prevent high-privilege account credentials from being unnecessarily exposed on member servers or workstations.
Additional resources
- AD Security 101: Non-Default Security Principals with DCSync Rights
- 7 Active Directory Misconfigurations to Find and Fix—Now
- NSA Top Ten Cybersecurity Misconfigurations: An Active Directory Perspective
- Purple Knight
- Directory Services Protector
Endnotes
- https://malpedia.caad.fkie.fraunhofer.de/actor/apt20
- https://apt.etda.or.th/cgi-bin/showcard.cgi?g=Calypso
- https://attack.mitre.org/groups/G1006/
- https://attack.mitre.org/groups/G1004/
- https://attack.mitre.org/groups/G0065/
- https://attack.mitre.org/groups/G0129/
- https://malpedia.caad.fkie.fraunhofer.de/actor/unc5330
- https://www.cyber.gov.au/about-us/view-all-content/alerts-and-advisories/apt40-advisory-prc-mss-tradecraft-in-action
- https://cloud.google.com/blog/topics/threat-intelligence/ivanti-post-exploitation-lateral-movement
- https://unit42.paloaltonetworks.com/stately-taurus-attacks-se-asian-government/
- https://hitcon.org/2022/slides/Earth-Lusca-Revealing-a-Worldwide-Cyberespionage-Operation.pdf
- https://www.microsoft.com/en-us/security/blog/2022/03/22/dev-0537-criminal-actor-targeting-organizations-for-data-exfiltration-and-destruction/
- https://www.fox-it.com/media/kadlze5c/201912_report_operation_wocao.pdf
- https://blog.avast.com/ccleaner-fights-off-cyberespionage-attempt-abiss
- https://global.ptsecurity.com/analytics/calypso-apt-2019
