A Golden Ticket attack occurs when an attacker forges a Kerberos Ticket Granting Ticket (TGT) to gain full control over an Active Directory environment. By compromising the KRBTGT account, which signs all Kerberos tickets, the attacker can create fake tickets for any user and gain access to any resource within the domain.
What is a Golden Ticket attack?
A Golden Ticket attack begins with an attacker gaining access to the domain’s KRGTGT account. This account is used by the Key Distribution Center (KDC) to encrypt and sign all TGTs. The attacker then extracts the account’s NTLM hash, using it to forge a Kerberos TGT with any desired group membership or lifetime. Using this Golden Ticket, the attacker can then request Ticket Granting Service (TGS) tickets for any services in the domain.
To forge a Golden Ticket, the attacker needs several key pieces of information: the username to impersonate (e.g., Administrator), the domain name, the domain SID (a unique identifier for the domain), and (as previously mentioned) the KRBTGT account’s password hash. With this information, the attacker can quickly generate a forged TGT and gain unrestricted access to domain resources as the impersonated user (Figure 1).
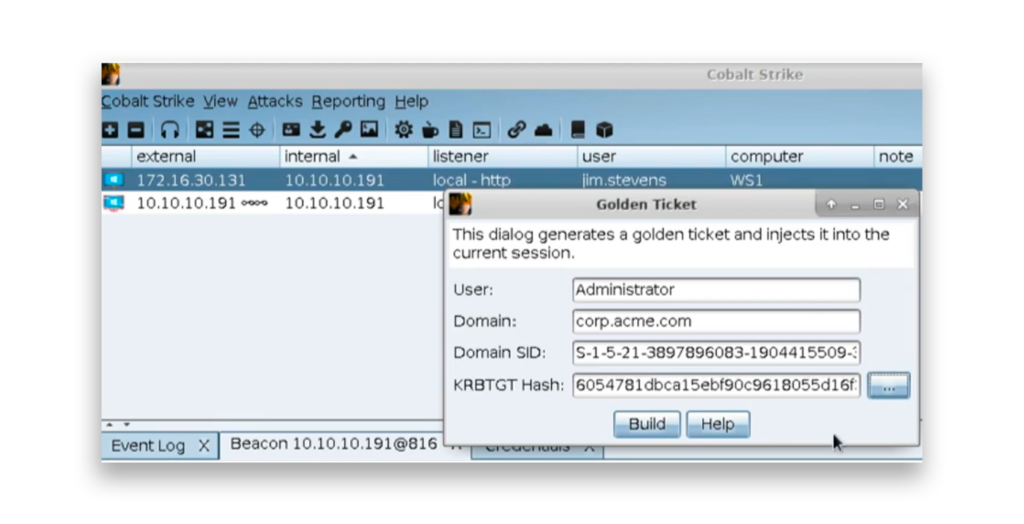
After forging the Golden Ticket, the attacker can inject it into the current session. For example, the attacker can impersonate the Administrator account (Figure 2).
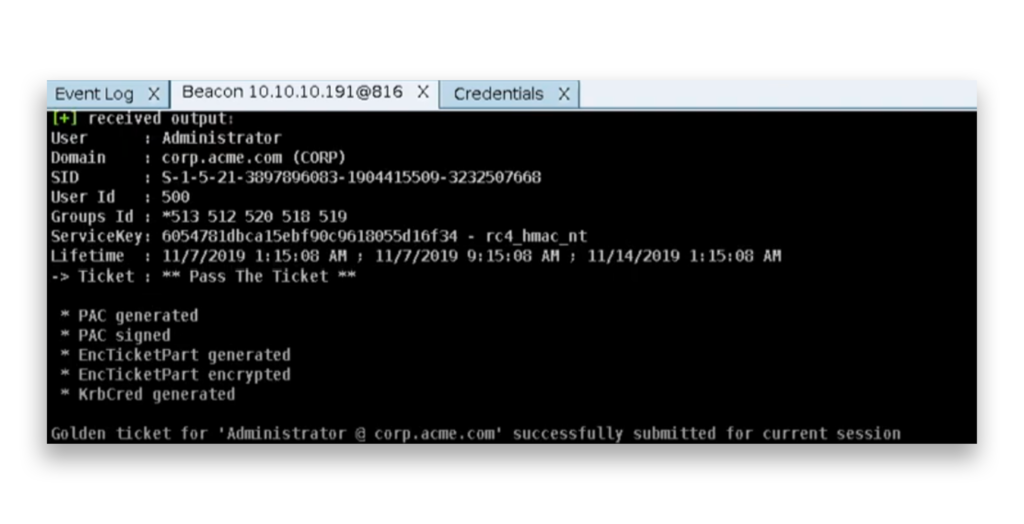
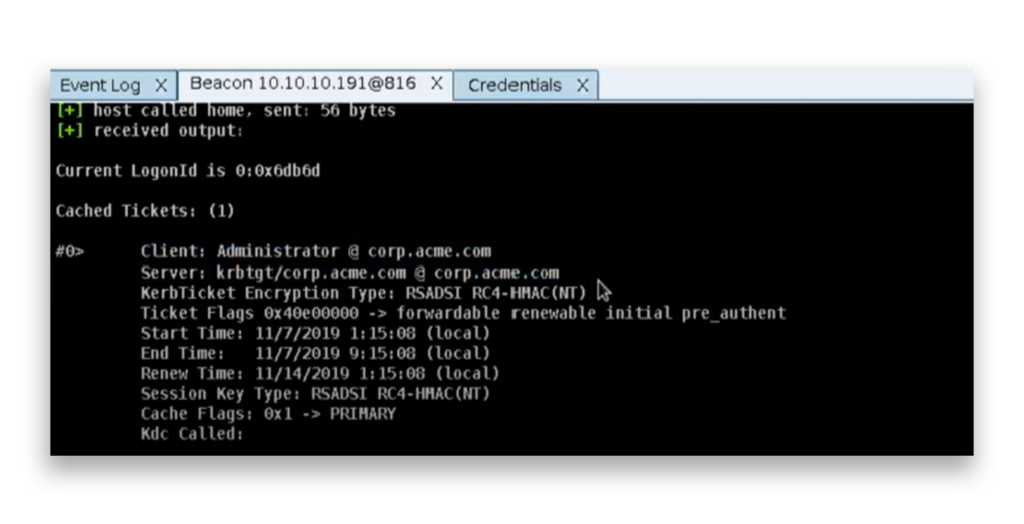
Figure 3 shows a cached Kerberos TGT for the Administrator account in the corp.acme.com domain. The Golden Ticket is now stored in the session cache, enabling the attacker to authenticate as the Administrator and access domain resources.
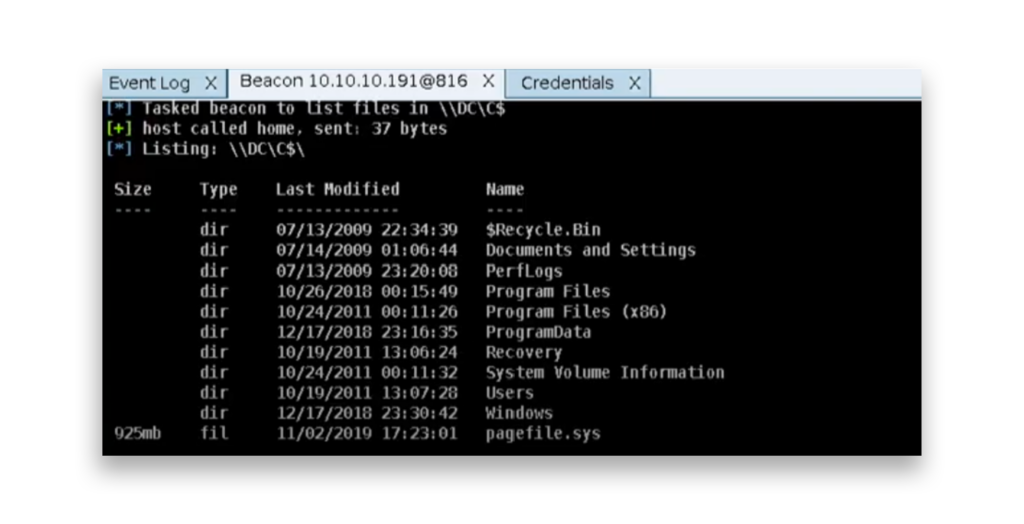
The attacker can now use the Administrator account to access the file share on a domain controller (DC) (Figure 4).
How can you defend against Golden Ticket attacks?
It’s important to follow best practices, such as implementing a tiered administration model and reducing the number of privileged accounts, to limit exposure to Golden Ticket attacks.
Suppose that:
- Your organization has been compromised by an attacker
- A pen tester has gained Domain Admin privileges
- A system administrator has left the company on bad terms
Each of these scenarios should raise valid concern about the potential for Golden Ticket attacks.
To mitigate a Golden Ticket attack, the most critical step is to reset the KRBTGT account password twice to invalidate any forged tickets. To make this process easier, Microsoft MVP and Semperis Senior Incident Response Lead Jorge de Almeida Pinto has created a PowerShell script, available on github.com, that you can use to safely reset the KRBTGT account. This script contains a variety of options.
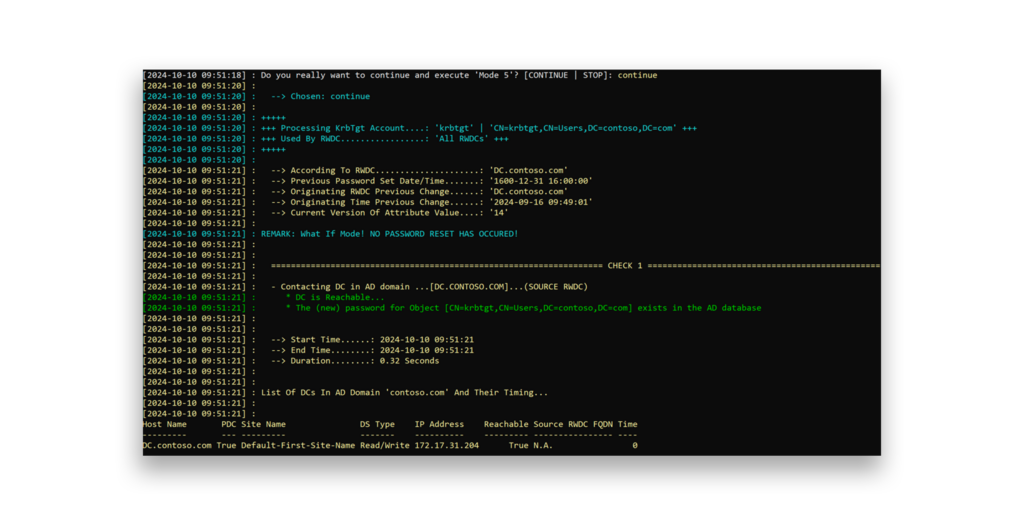
For example, Mode 5 in the script is a simulation mode that works with your real KRBTGT production accounts but does not actually reset the passwords. Instead, it simulates the process to verify access and replication functionality without making any changes. This mode is useful for testing that everything works properly (e.g., checking permissions and replication) without affecting your production environment (Figure 5).
After all tests have passed and everything is green, you can proceed with the first password reset by selecting Mode 6, which resets the KRBTGT account one time (Figure 6).
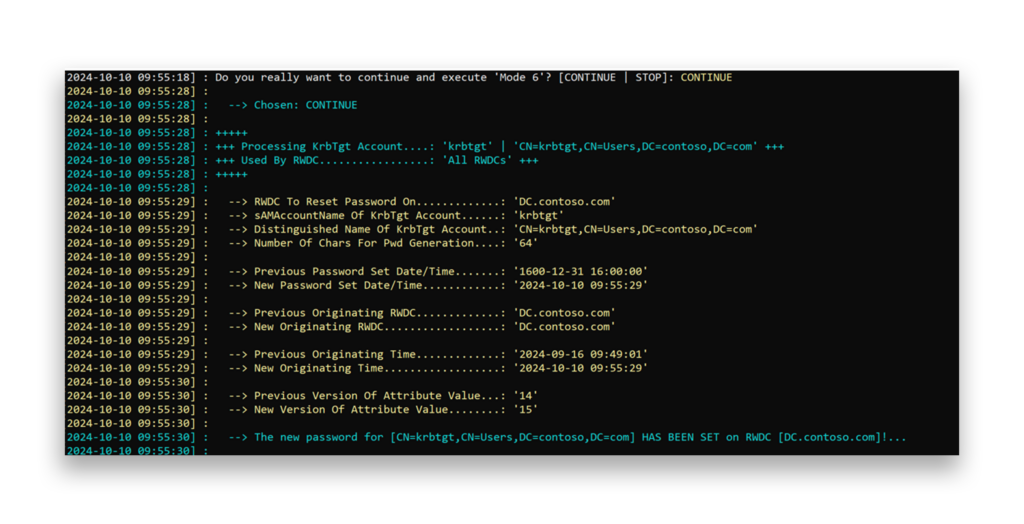
Typically, after the first KRBTGT password reset, you should wait 10 hours (the default Kerberos TGT lifetime). Then, repeat your previous steps to perform the second reset.
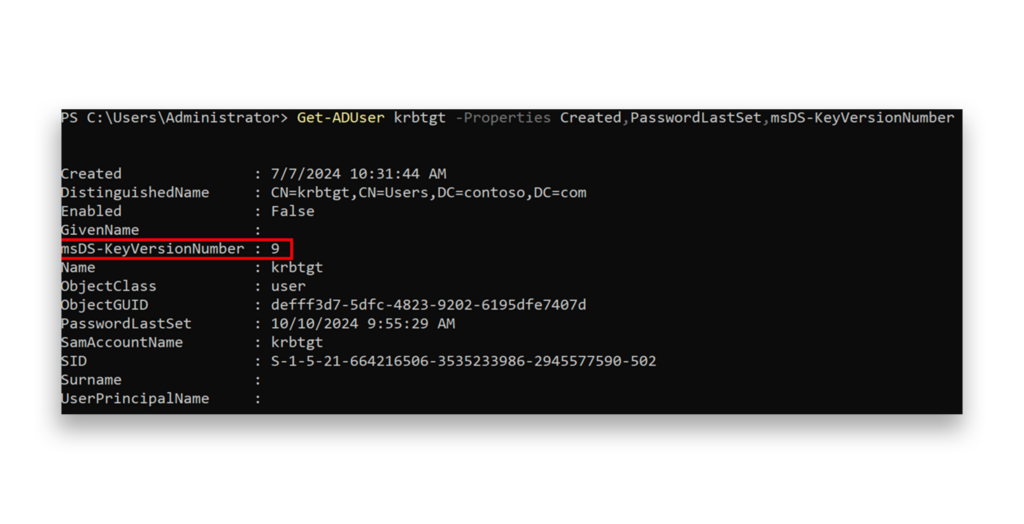
If waiting 10 hours isn’t possible, you can reduce the Kerberos TGT lifetime to, say, 5 hours, and then monitor for any potential impact on your DCs. This approach enables you to proceed faster while still verifying that the environment is functioning properly. Each time the KRBTGT account password is reset, the msDS-KeyVersionNumber attribute of the KRBTGT account should increase by 1 (Figure 7).
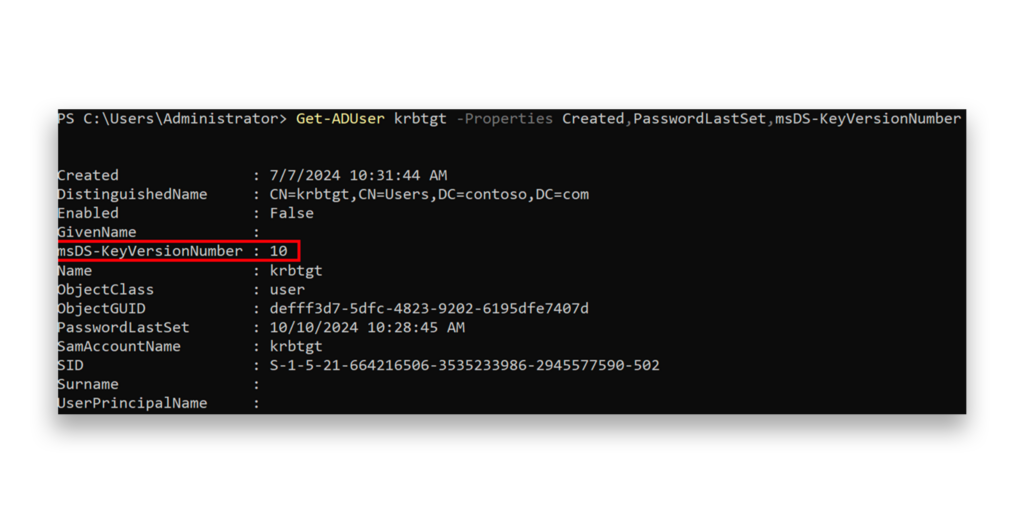
In this example, you can see that after completing the second password reset, the msDS-KeyVersionNumber value has incremented to 10 (Figure 8).
Overall, you need to apply the full range of Active Directory security best practices to defend against a Golden Ticket attack.
How can you detect a Golden Ticket attack?
Regular auditing and monitoring of privileged account activity is essential. Tools like Purple Knight and Forest Druid can help defenders find weak spots and attack paths within Active Directory. Also watch for the following potential indicators of suspicious Golden Ticket activity:
- Ticket lifetime: One common trait of Golden Ticket attacks is an extended ticket lifetime. The default Kerberos ticket lifetime is 10 hours. Kerberos tickets with unusually long lifetimes (e.g., 10 years), can be indicators of attack activity.
- Mismatched SIDs: Look for a Security Identifier (SID) in the TGT that does not match any active SID in the domain. This type of mismatch is especially likely when the ticket was forged in an environment where the attacker doesn’t have complete visibility.
- Repetitive TGT use: If the KRBTGT account password has changed but a TGT issued before the password change is still being presented to get TGSs, an attacker could be at work.
- Abnormal account behavior: Anomalies such as non-administrative accounts suddenly accessing high privileged resources can be an indicator of a Golden Ticket attack.
- Event logs: Windows Event ID 4769 can show a service ticket request. Look for any unusual patterns or irregularities, especially involving high-privilege accounts.
Threat actor profiles
The following threat actors have used Golden Ticket attacks in their operations:
- Antlion1
- Ke3chang aka APT15, Mirage, Vixen Panda, GREF, Playful Dragon, RoyalAPT, NICKEL, Nylon Typhoon (MITRE ATT&CK Group G0004)2
- TA428 aka Panda, ThunderCats3
Golden Ticket attack tools
The following public tools, which are available on github.com, can be used to forge Golden Tickets:
- fortra/impacket
- gentilkiwi/mimikatz
Threat overview
ATT&CK Tactic: Persistence
On August 8, 2022, Kaspersky published a report detailing how a Chinese-speaking APT group, suspected to be TA428, conducted targeted attacks against military-industrial enterprises and public institutions in Eastern Europe and Afghanistan. The attackers exploited vulnerabilities to infiltrate networks and, after gaining Domain Administrator privileges, used a Golden Ticket attack to forge Kerberos TGTs. This enabled the attackers to impersonate any user within the organization and gain unrestricted access to sensitive systems.4
On February 4, 2022, Symantec reported that the Chinese-linked APT group Antlion had been targeting financial institutions in Taiwan over an 18-month campaign from 2020 to 2021. The group used custom backdoors to infiltrate systems and gain long-term access. Among their tactics, the attackers used tools like Mimikatz to dump credentials and perform a Golden Ticket attack, which enabled them to create forged Kerberos tickets and maintain persistent control of the compromised networks.5
On March 10, 2018, NCC Group reported that APT15, a Chinese cyber espionage group, used various backdoors to infiltrate a UK government contractor’s network. The attackers later employed Mimikatz to steal credentials and executed a Golden Ticket attack, which enabled them to create forged Kerberos tickets and hold onto Domain Administrator privileges, thus keeping control of the network and accessing sensitive data long after the initial breach was detected.6
Semperis snapshot
A Golden Ticket attack is a powerful way for attackers to exploit Active Directory by forging Kerberos tickets, which give them broad access to network resources. However, this attack manageable with the right approach. Limiting who has access to highly privileged accounts, using a tiered administration model, and regularly auditing your environment can help you mitigate the risk associated with Golden Ticket attacks.
Additional resources
- How to Defend Against Golden Ticket Attacks
- Golden Ticket Attacks on Active Directory
- How to Defend Against Silver Ticket Attacks
- A Diamond Ticket in the Ruff
- Purple Knight
- Forest Druid
Endnotes
- https://malpedia.caad.fkie.fraunhofer.de/actor/antlion
- https://attack.mitre.org/groups/G0004/
- https://apt.etda.or.th/cgi-bin/showcard.cgi?g=TA428&n=1
- https://www.kaspersky.com/about/press-releases/golden-ticket-for-industrial-espionage-apt-group-takes-over-it-infrastructure
- https://www.security.com/threat-intelligence/china-apt-antlion-taiwan-financial-attacks
- https://www.nccgroup.com/us/research-blog/apt15-is-alive-and-strong-an-analysis-of-royalcli-and-royaldns/

