Tracking Group Policy changes can be tricky, especially in large environments with numerous Group Policy Objects (GPOs) linked to different organizational units (OUs). Yet GPO change auditing is a vital part of effective cybersecurity. Without proper visibility, critical changes—whether due to accidental misconfigurations or malicious activity—can easily slip under the radar. In this blog post, we’ll show how Directory Services Protector (DSP) simplifies GPO change auditing so that you can protect Active Directory—and your business.
What are GPOs?
Group Policy Objects (GPOs) are a key feature in Active Directory environments. GPOs control a wide range of settings, including but not limited to security policies and password requirements.
GPOs enable administrators to manage and enforce configurations across multiple users and computers within an organization. By applying GPOs to Active Directory containers such as sites, domains, and OUs, you can easily deploy consistent policies across specific groups of users or devices without needing to manually configure each one.
Why should you audit GPO changes?
Because GPOs control critical security and operational settings, any unauthorized or unintended changes can have far-reaching consequences. That’s why it’s so important to have visibility into exactly what changed, when the change was made, and who made the change.
A single change to the right—or should we say, wrong—GPO can weaken your security controls and create gaps for attackers to exploit. Spotting such changes quickly, as well as receiving insights into who made the change and when, enables you to close those gaps and protect critical assets.
GPO change auditing with Semperis DSP
To illustrate the importance of GPO change auditing and how DSP provides this capability, let’s walk through a few examples.
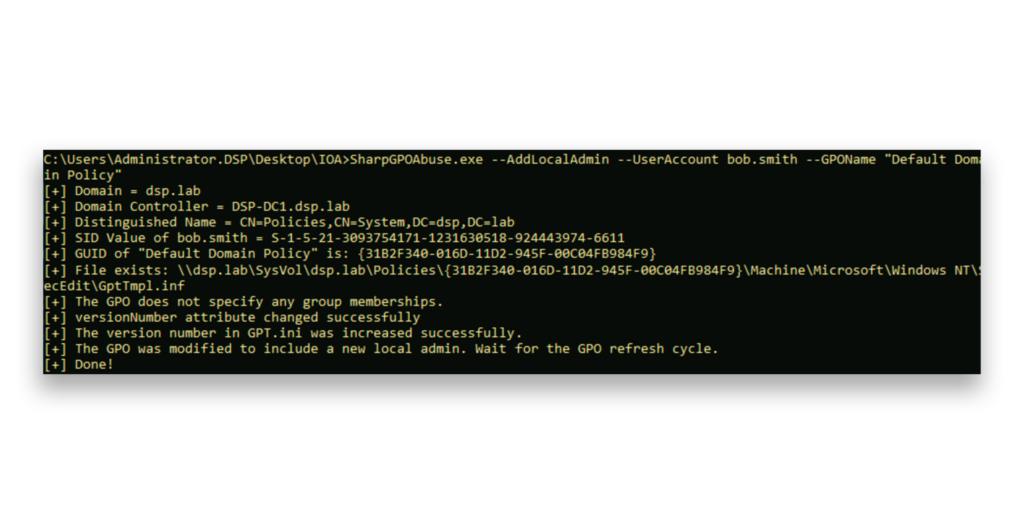
SharpGPOAbuse is a tool that enables attackers with edit rights over a GPO to weaponize Group Policy for privilege escalation or use it to execute malware. In this example, an attacker has used SharpGPOAbuse to modify the Default Domain Policy GPO by adding an account to the local Administrators group (Figure 1). By default, the Default Domain Policy is linked to the Domain Naming Context (e.g., the root object), making it a critical GPO with Tier 0 access.
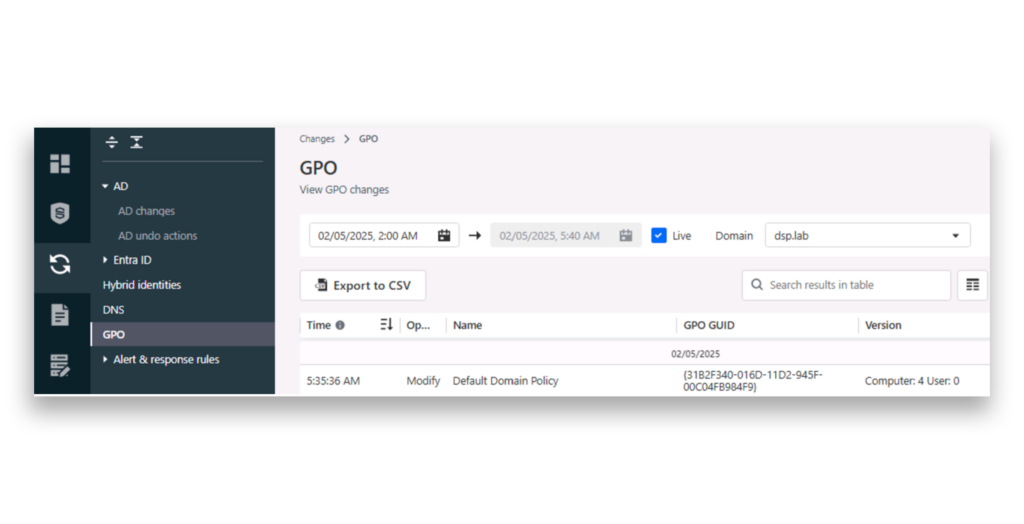
After the GPO is modified, the DSP Changes > GPO page lists an entry reflecting the change (Figure 2).
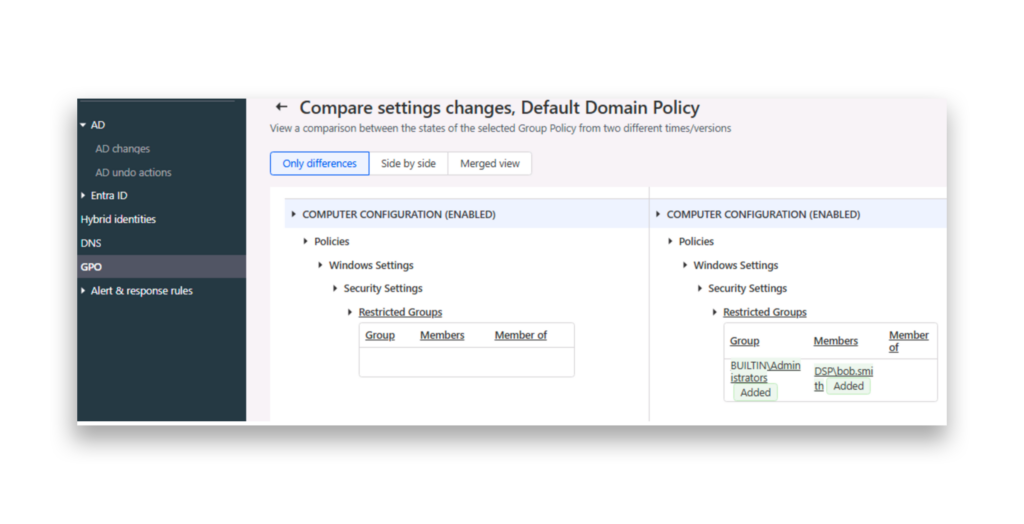
DSP enables you to compare the current GPO version with a previous one so that you can identify the changes that were made (Figure 3).
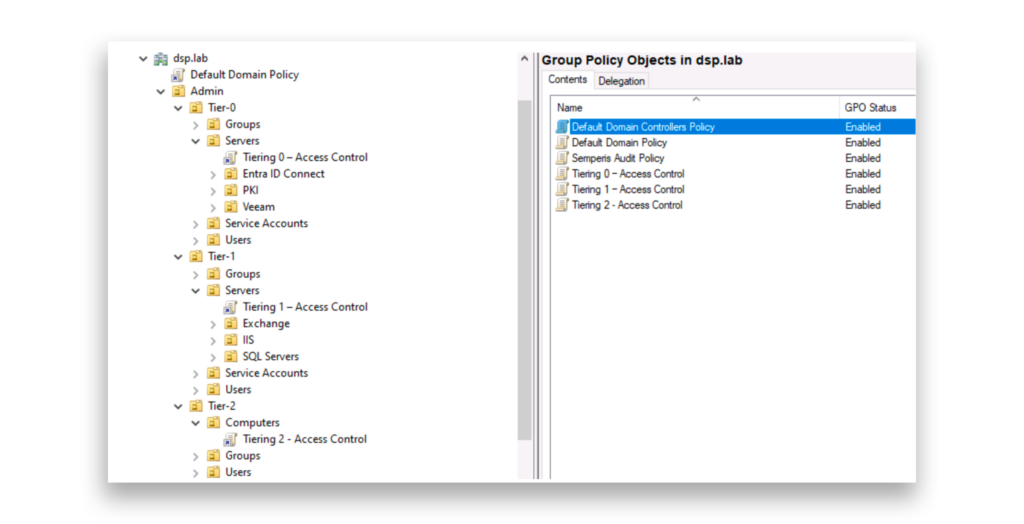
Let’s look at another example. Organizations that have implemented the Microsoft Administrative Tiering Model to reduce the risk of lateral movement and credential exposure on lower-tier systems often use GPOs to enforce restrictions, controlling which users and groups can log on to specific tiers (Figure 4). GPOs in these environments also often contain hardening settings.
In these scenarios, an attacker might attempt to modify the Tier 0 GPO settings, weakening security by removing specific user rights assignments or disabling security features. For example, an attacker might modify the GPO linked to the Tier 0 servers to turn off Microsoft Defender Antivirus and real-time protection (Figure 5).
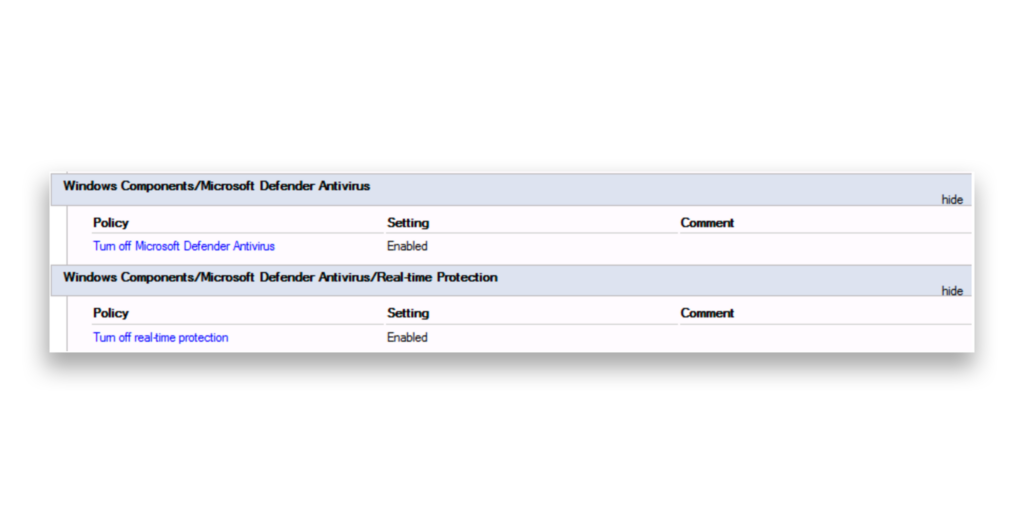
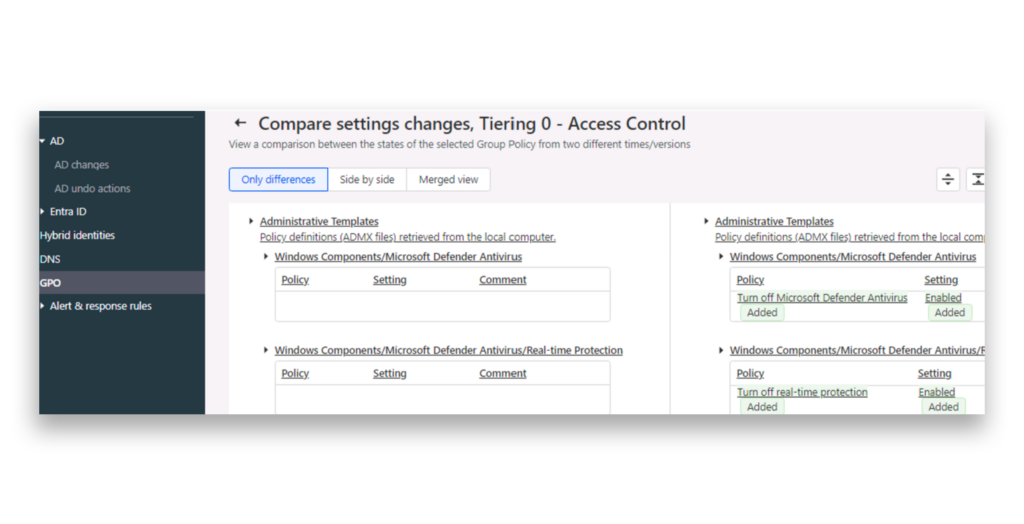
Once again, DSP tracks every GPO change. We can easily see which security features have been turned off (Figure 6).
GPO change alerts and notifications
GPO modifications like the ones in our examples can expose Active Directory and the rest of your environment to additional malicious actions. Fast action is imperative.
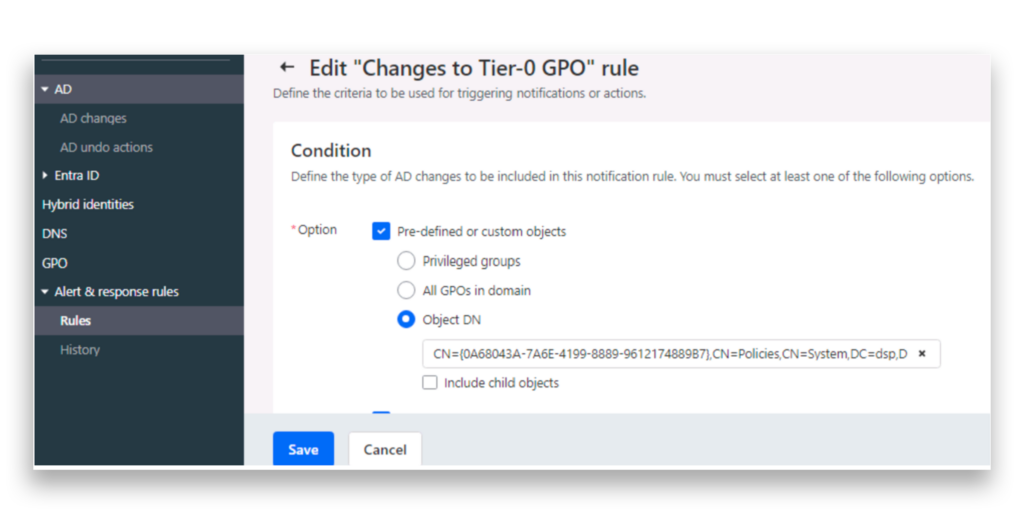
That’s why DSP supports custom notification rules to help you monitor critical GPOs and receive email alerts whenever changes are made (Figure 7). This feature ensures that you stay informed at the first sign of potential Group Policy abuse.
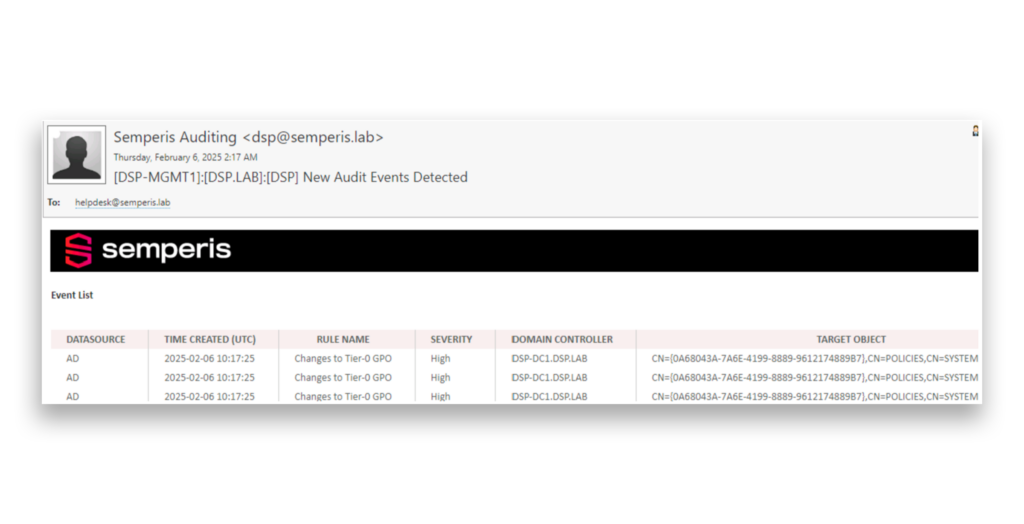
When this GPO is modified, we’ll receive an email notification detailing the account responsible for the change and the specific GPO that was updated (Figure 8).
Restoring GPO settings with DSP
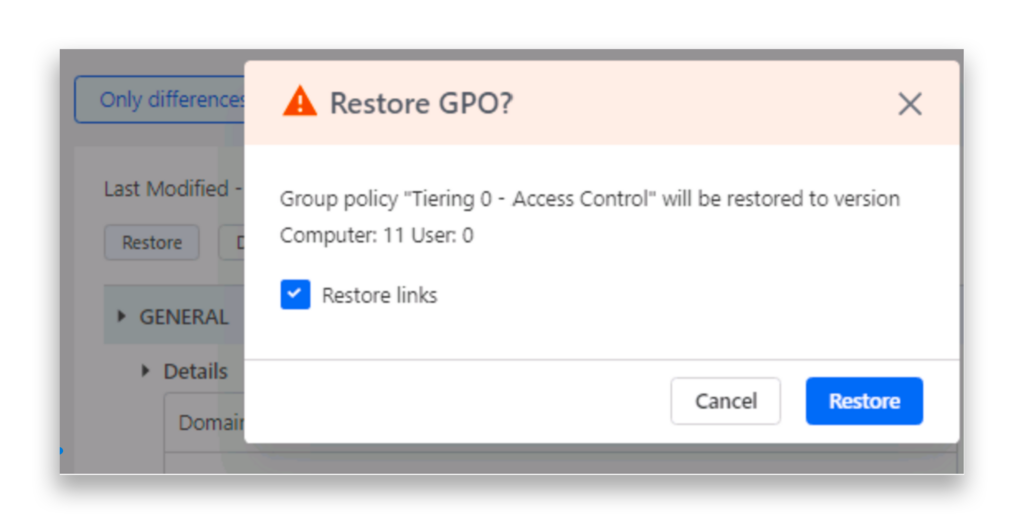
Another key benefit of DSP is the ability to restore GPO settings to a previous version, making it easy to undo suspicious or risky changes (Figure 9). We’ll discuss this undo feature in greater detail in a future post.
Semperis snapshot
Keeping an eye on GPO changes is essential, especially for policies linked to critical servers. A single unauthorized or accidental change can weaken security, disrupt operations, or open the door for attackers. With GPO change auditing in DSP, you can quickly spot, track, and restore previous settings, mitigating Group Policy abuse and ensuring that your environment stays secure and under control.
