From my experience at Microsoft Detection and Response Team (DART), I know that ransomware operators almost always target high-privileged identities. Once attackers gain control, they use those identities to spread ransomware; for example, through Group Policy or PsExec. Ransomware attacks are usually loud and destructive, aiming to cause maximum impact in the shortest time possible. That’s why it’s important not just to recover identity systems after an attack, but also to ensure that the environment can be trusted again to prevent follow-on attacks.
Incident response (IR) has traditionally focused on threat hunting and forensic analysis to understand how an attack happened, identifying compromised accounts and machines, analyzing malware, and tracing the attacker’s activities. However, when identity systems like Active Directory (AD) and Entra ID are compromised, standard investigation isn’t enough. To reduce the risk of attackers regaining access, containment, identity-specific forensics, and secure recovery become just as critical. This is where Identity Forensics & Incident Response (IFIR) stands apart.
What is IFIR?
IFIR prioritizes the resilience of identity systems by reducing the attack surface and eliminating security threats before, during, and after an attack. Our approach includes hunting down AD backdoors and misconfigurations that attackers can exploit to break in or re-enter a target environment: ACL-based persistence, SID history injection, malware in SYSVOL, Kerberos delegation abuse, Group Policy manipulation, ADCS and PKI-related backdoors, and many more.
In the age of ransomware, incident response roles are expanding. Matt Zorich, an IR professional, tweeted about how traditional Digital Forensics & Incident Response (DFIR) now includes containment and recovery, highlighting that these steps are just as important as the investigation itself (Figure 1). This shift is becoming more common in the industry. Incident responders aren’t just expected to determine what happened, but also to assist with containment and recovery.
With attackers going after identity systems like Active Directory and Entra ID, investigation alone isn’t enough. Organizations need a way to restore their identity environment with confidence, and that’s exactly where Semperis comes in.
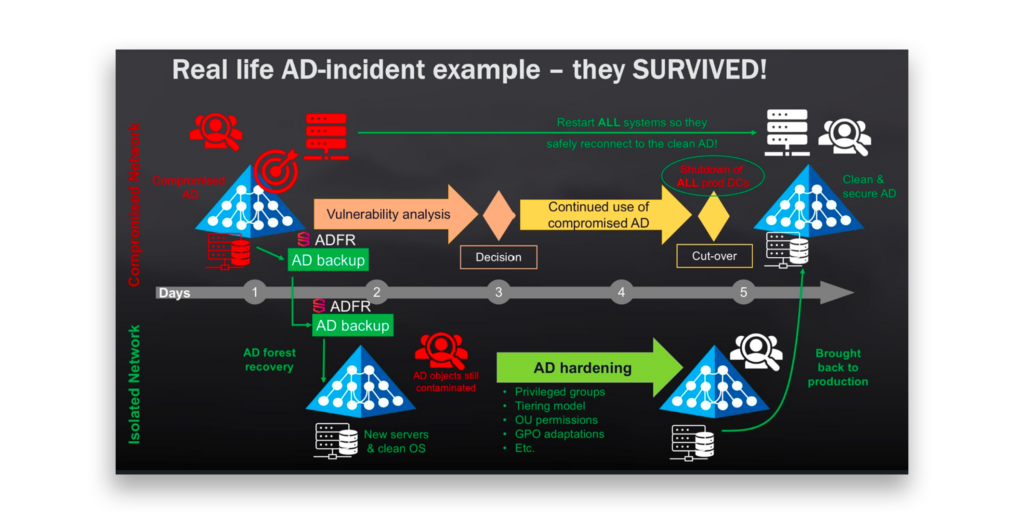
Getting domain controllers (DCs) back online after an attack is only part of the equation. The real challenge is ensuring that identity systems remain secure and resilient to avoid follow-on attacks. Our IFIR team specializes not just in containment and recovery but also in cleansing the environment of any breadcrumbs left by attackers and proactively identifying weak configurations in AD—strengthening defenses and reducing the risk of future identity-based attacks (Figure 2).
Many organizations operate in a hybrid identity model, in which on-premises AD is closely integrated with cloud-based identity providers (IdPs) like Entra ID. This setup enables seamless authentication and access to SaaS applications such as Office 365, Salesforce, and Zoom, but it also expands the attack surface. A compromise in AD doesn’t just affect on-prem systems; it can directly impact cloud security as well, making IFIR capabilities critical to deploy as early as possible.
IFIR doesn’t just focus on AD recovery. Semperis also investigates Entra ID for weaknesses and persistence mechanisms that attackers might use to maintain long-term control over cloud identities. Attackers who gain access to on-prem AD can escalate their foothold into the cloud, which makes hybrid identity security a critical concern (Figure 3).
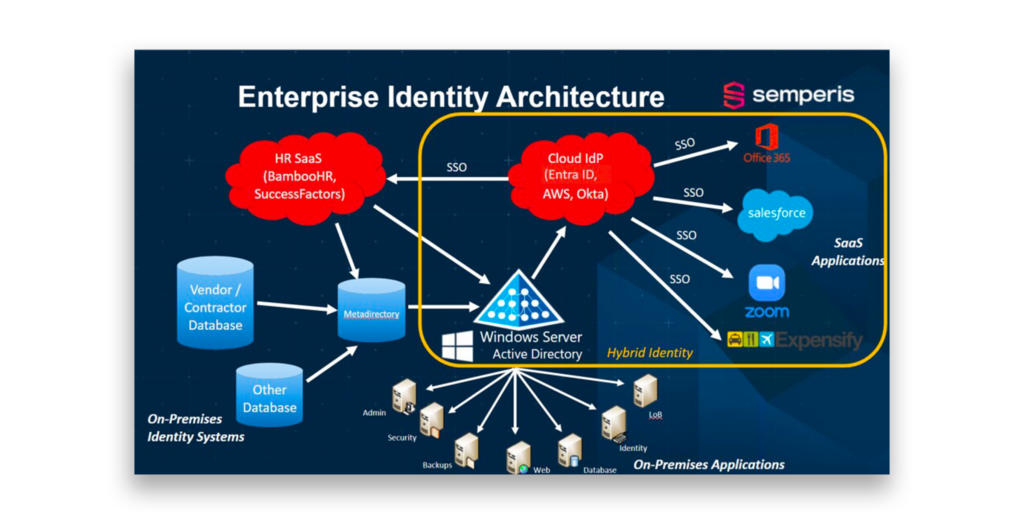
Figure 3 illustrates the complexity of enterprise identity architecture, in which multiple systems such on-prem databases, cloud IdPs, and SaaS applications are interconnected. When attackers compromise AD, they can pivot into cloud environments, escalate privileges, or establish persistence.
Brownfield deployment vs greenfield deployment
A greenfield Active Directory deployment starts fresh, with a brand-new AD environment. In theory, this approach sounds ideal after a major compromise because it removes any lingering threats from the old environment. But in an enterprise setting, greenfield recovery is rarely practical.
A brownfield deployment restores and secures the existing AD environment rather than rebuilding it from scratch. A full greenfield recovery requires migrating users, reconfiguring applications, and ensuring everything integrates properly which is a massive effort that can be costly and disruptive. A brownfield recovery, on the other hand, focuses on remediating threats and strengthening security while keeping business operations running.
Identity Forensics & Incident Response plays a critical role. Restoring AD without thoroughly identifying and addressing misconfigurations, backdoors, and other security gaps can leave organizations vulnerable to reinfection.
Although a greenfield rebuild might be necessary in extreme cases, a brownfield recovery is often the best balance between security, cost, and business continuity. With IFIR, organizations can restore and secure AD while reducing the risk of reintroducing compromise by identifying and eliminating misconfigurations and weaknesses before bringing systems back into production.
Get help from the IFIR experts
During an incident response, organizations often bring in DFIR specialists to investigate what happened. But investigation is only one part of the equation. Recovery and containment are just as important. Restoring operations securely and minimizing the chance of attackers regaining access requires a different skill set.
Semperis’ IFIR team makes the difference. We specialize in Active Directory and Entra ID recovery, ensuring your identity systems are brought back online safely and securely. Whether you need to contain an active threat, remove insecure configurations, develop a disaster recovery plan, or strengthen your overall identity security posture, we’re here to help.
Semperis can also work alongside your preferred DFIR team, providing the specialized identity recovery expertise needed to fully secure your environment.
If your organization is facing an identity-related incident, contact our IFIR team for a secure and reliable recovery.
