A recent report from the cybersecurity agencies in the Five Eyes alliance, including CISA and the NSA, urges organizations to strengthen the security of their Microsoft Active Directory (AD) deployments—a prime target for cyber attackers. The report describes dozens of attack techniques that attackers use to breach AD, including Kerberoasting. Read on to learn more about Kerberoasting, how it works, which threat actors are known to have used this technique, and how can you defend your identity infrastructure from Kerberoasting attacks and enhance your AD security posture.
What is Kerberoasting?
In a Kerberoasting attack, a threat actor with a valid domain account requests Kerberos service tickets for accounts with a Service Principal Name (SPN) registered in Active Directory. All the service tickets are encrypted with the service account’s password hash. The attacker extracts the encrypted tickets and cracks them offline to obtain the service account’s plaintext password, often targeting high-privilege accounts. This attack requires no elevated privileges but can lead to privilege escalation.
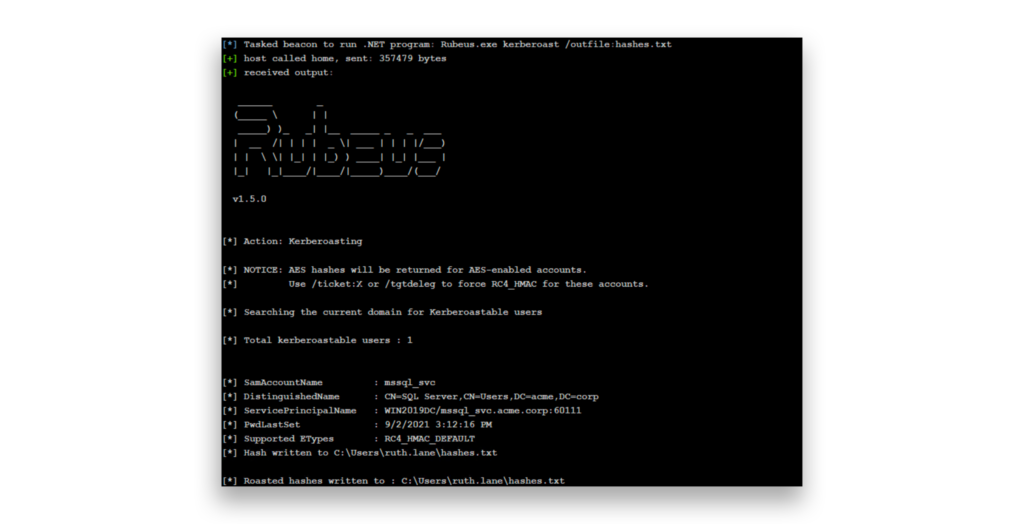
How can you defend your environment against Kerberoasting?
Defenders can use the free Purple Knight tool—mentioned specifically in the Five Eyes report—to identify high-privilege accounts with a registered SPN and assess whether the SPN is necessary. If not, they can determine whether the SPN can be safely removed, as the server associated with it might have already been decommissioned.
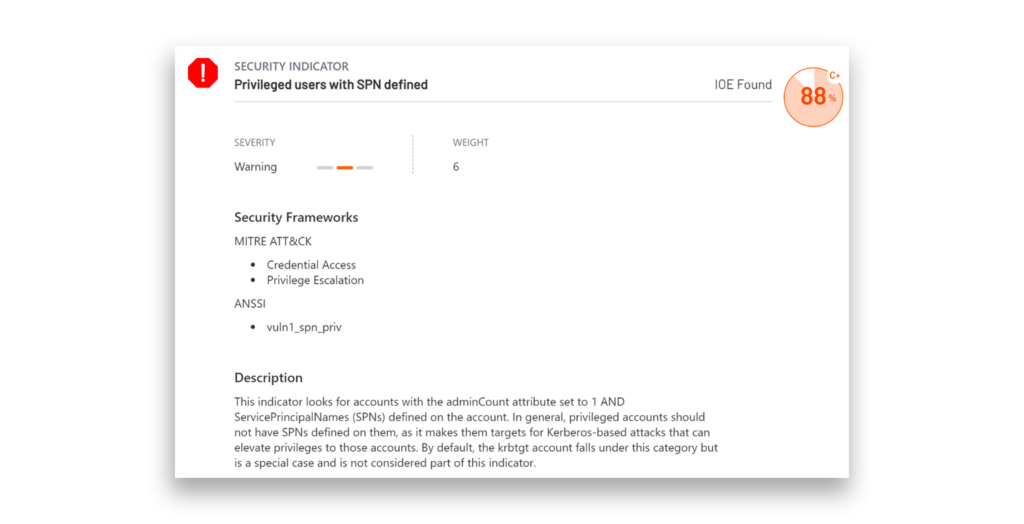
Based on the results, it appears that one account is associated with an SPN. The next step is to verify whether this account is still actively used. To make this determination, examine the SPN, which includes a server name.
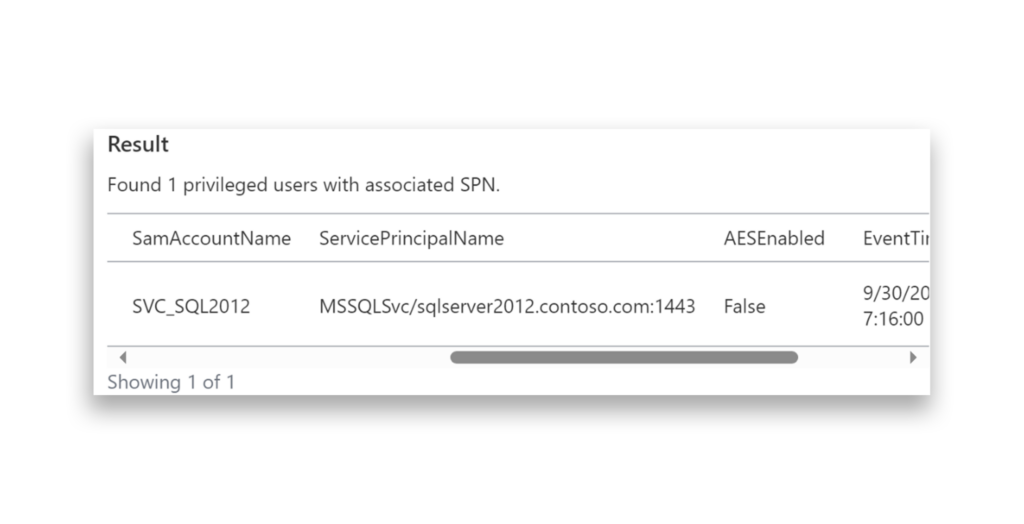
In this example, we ran a script to quickly check the Password Last Set time and the Last Logon Timestamp for the account. We then determined whether the server’s name in the SPN still had an associated computer object in Active Directory and performed an ICMP request to determine whether the server was responsive.
Although further checks might be necessary, this is an effective first step in validating whether the SPN is still in use. In this case, the SPN and computer object both existed, but the server had already been decommissioned.
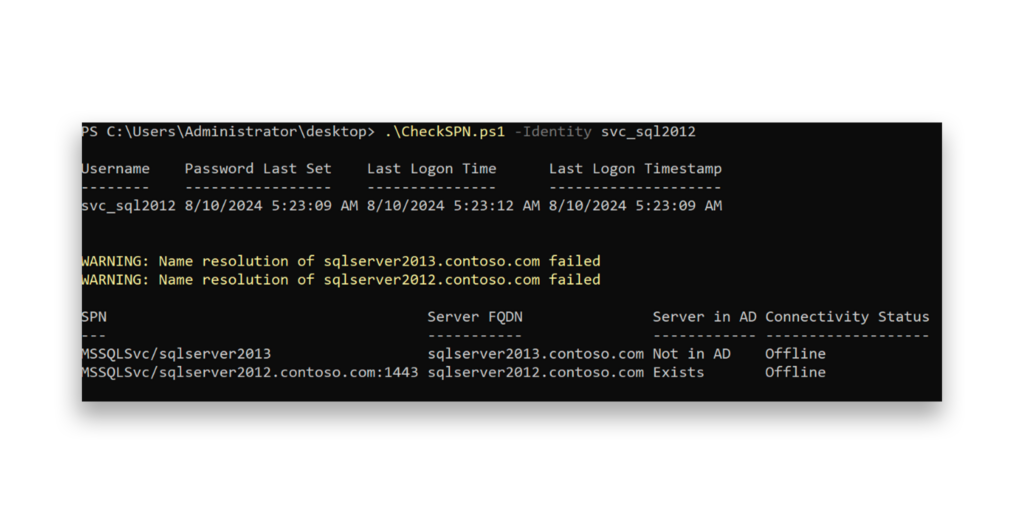
Since the server has been decommissioned, we can remove all the SPNs associated with this account. Additionally, because the account is no longer in use, we recommend that you change the account’s password and disable the account to mitigate the risk of a potential Kerberoasting attack.
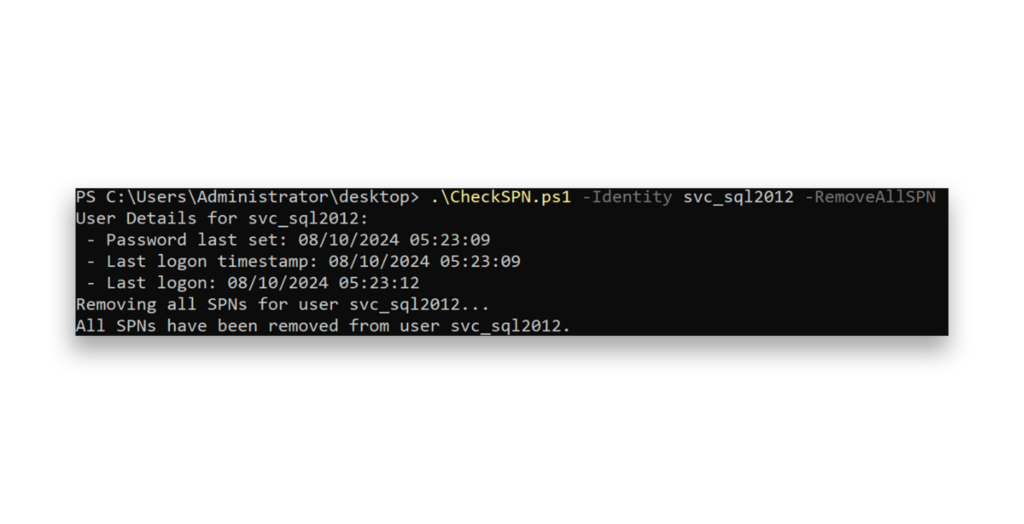
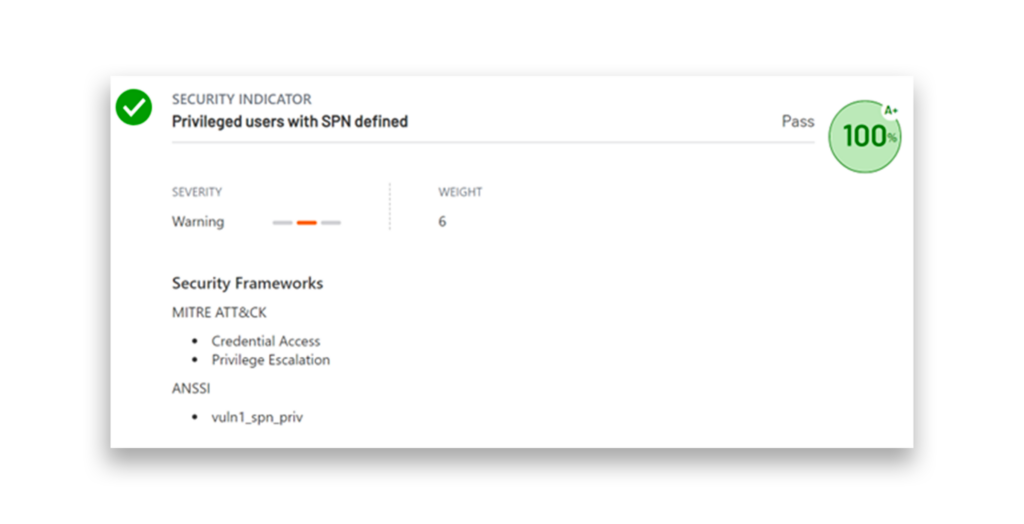
After removing the SPN, we immediately noted an increase in our security score.
How can you detect Kerberoasting?
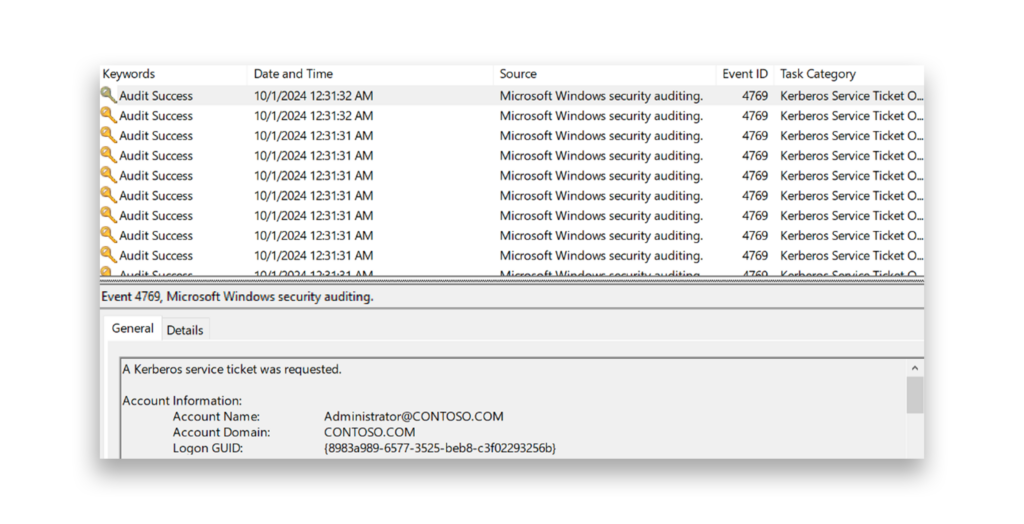
The most effective way to detect Kerberoasting is to monitor for instances where a single account makes a large number of service ticket requests within a short time.
Another method is to repurpose an old, unused service account as a honeytoken. Any Kerberos service ticket requests for that account should trigger an alert.
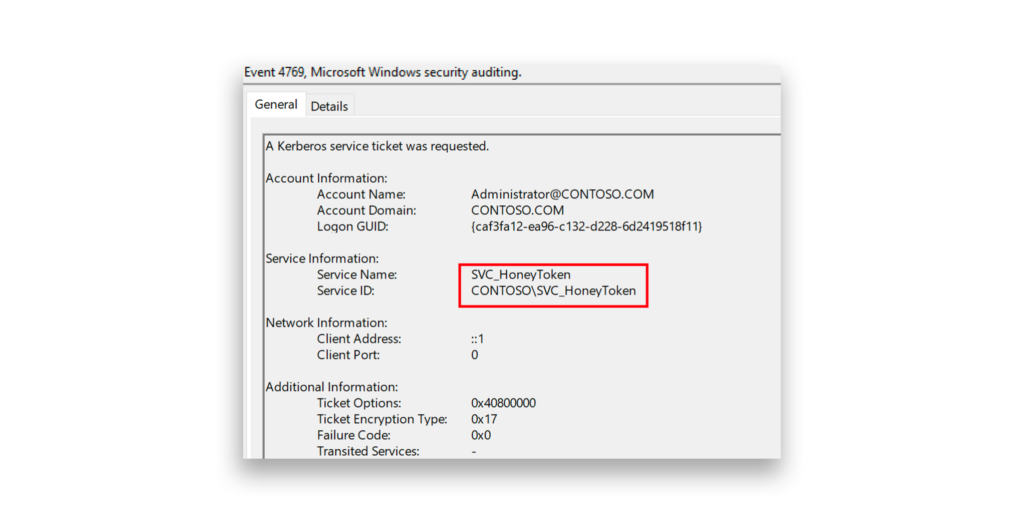
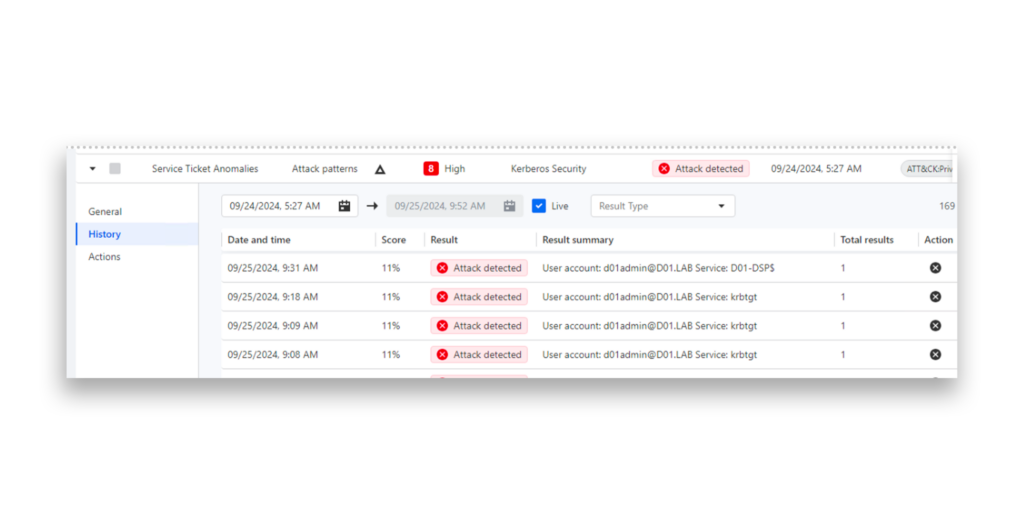
Identity Runtime Protection (IRP), a part of the Semperis Lighting Platform, uses various attack-pattern indicators and anomaly detection to monitor for and detect identity-based attacks. In this example, Lightning IRP has detected a suspicious request for a Kerberos service ticket using weak encryption, a common indicator of Kerberoasting activity.
Threat actor profiles
The following threat actors have been known to use Kerberoasting attacks in the wild.
- Akira aka Storm-1567, GOLD SAHARA, PUNK SPIDER (MITRE ATT&CK Group G1024)1
- APT40 aka Leviathan, MUDCARP, Kryptonite Panda, Gadolinium, BRONZE MOHAWK, TEMP.Jumper, TEMP.Periscope, Gingham Typhoon (MITRE ATT&CK Group G0065)2
- BlackSuit3
- FIN12 aka Wizard Spider, UNC1878, TEMP.MixMaster, Grim Spider, GOLD BLACKBURN, ITG23, Periwinkle Tempest, DEV-0193 (MITRE ATT&CK Group G0102)4
- UNC2165 aka Evil Corp, Indrik Spider, Manatee Tempest, DEV-0243 (MITRE ATT&CK Group G0119)5
- Vanilla Tempest aka DEV-0832, Vice Society6
- Vice Spider7
Kerberoasting tools
The following public tools and scripts, most of which are available on github.com, can be used to perform a Kerberoasting attack and have been observed in use during real-world incidents.
- GhostPack/Rubeus
- gentilkiwi/mimikatz
- EmpireProject/Empire
- Sicilian Defense
- ropnop/kerbrute
- GhostPack/SharpRoast (deprecated)
Threat overview
ATT&CK Tactic: Credential Access
On August 26, 2024, The DFIR Report explained how the BlackSuit ransomware gang used Kerberoasting in their attacks. By targeting accounts with SPNs, they were able to request and extract Kerberos service tickets. These tickets were then cracked offline to recover plaintext passwords, potentially giving them access to higher-privilege accounts.8
On July 9, 2024, the Australian Signals Directorate (ASD) published a report about APT40‘s use of Kerberoasting as part of their attack tactics. APT40 leveraged Kerberoasting to request service tickets from accounts with SPNs in Active Directory. They then cracked these tickets offline to recover passwords, allowing them to escalate privileges and move laterally within compromised networks.9
On April 18, 2024, the FBI released a report on Akira ransomware, about the group’s use of Kerberoasting to escalate privileges in targeted environments. Akira actors used Kerberoasting to request Kerberos service tickets for accounts with SPNs in Active Directory. These tickets were then cracked offline to reveal passwords, which allows the attackers to gain higher privileges within the network.10
In August 2023, CrowdStrike published a report on VICE SPIDER, a financially motivated threat group, about their use of Kerberoasting as part of their attacks. VICE SPIDER used tools like Rubeus and SharpRoast to query Active Directory for Service Principal Names (SPNs) and obtain Kerberos service tickets. These tickets were then cracked offline with tools like Hashcat to reveal plaintext passwords. This allowed VICE SPIDER to increase privileges and gain deeper access to compromised networks.11
On October 25, 2022, Microsoft reported that Vanilla Tempest (formerly DEV-0832) used the PowerShell script Invoke-Kerberoast.ps1 to perform Kerberoasting in their ransomware attacks. This allowed them to extract Kerberos service tickets for accounts with SPNs, which were then cracked offline to retrieve plaintext passwords.12
On June 2, 2022, Mandiant published a report about UNC2165‘s shift in tactics. The report highlights that UNC2165, a financially motivated group used Kerberoasting as part of their privilege escalation strategy. They used tools like Mimikatz and Rubeus to obtain Kerberos tickets, which were stored in the %ProgramData% directory. Once they acquired these credentials, they tested them across the network to gain access and ultimately used this elevated access to deploy ransomware, such as HADES and LOCKBIT.13
In October 2021, Mandiant published a report on FIN12, highlighting their use of Kerberoasting to escalate privileges in targeted environments. FIN12 leveraged tools like KERBRUTE, RUBEUS, and Invoke-Kerberoast.ps1 to request Kerberos service tickets for service accounts with SPNs. After collecting these tickets, they cracked them offline to obtain the associated passwords, which gave them broader access to the network.14
Semperis snapshot
Kerberoasting is a popular attack method because it takes advantage of weak passwords in the Kerberos authentication system. Groups like FIN12, VICE SPIDER, APT40, and Akira ransomware operators have used this technique to request service tickets, then crack them offline to get plaintext passwords. Kerberoasting’s widespread use shows just how important it is for organizations to enforce strong password policies, regularly check whether accounts with SPNs are still needed, and watch for unusual Kerberos service ticket requests to defend against these attacks.
Additional resources
- How to Protect Active Directory Against Kerberoasting
- Understanding and Protecting Kerberos
- How to Defend Against SPN Scanning in Active Directory
- Active Directory Hardening Best Practices
- Introducing Lightning Identity Runtime Protection
- Purple Knight
- Lightning IRP: AI-Powered Attack Pattern Detection
Endnotes
- https://attack.mitre.org/groups/G1024/
- https://attack.mitre.org/groups/G0065/
- https://www.sentinelone.com/anthology/blacksuit/
- https://attack.mitre.org/groups/G0102/
- https://attack.mitre.org/groups/G0119/
- https://malpedia.caad.fkie.fraunhofer.de/actor/vanilla_tempest
- https://www.crowdstrike.com/adversaries/vice-spider/
- https://thedfirreport.com/2024/08/26/blacksuit-ransomware/
- https://www.cyber.gov.au/about-us/view-all-content/alerts-and-advisories/apt40-advisory-prc-mss-tradecraft-in-action
- https://www.ic3.gov/Media/News/2024/240418.pdf
- https://asiapacificdefencereporter.com/wp-content/uploads/2023/08/Final-CRWD-2023-Threat-Hunting-Report.pdf
- https://www.microsoft.com/en-us/security/blog/2022/10/25/dev-0832-vice-society-opportunistic-ransomware-campaigns-impacting-us-education-sector/
- https://cloud.google.com/blog/topics/threat-intelligence/unc2165-shifts-to-evade-sanctions/
- https://www.mandiant.com/sites/default/files/2021-10/fin12-group-profile.pdf
