Lightweight Directory Access Protocol (LDAP) reconnaissance is an approach that enables attackers to discover valuable details about an organization, such as user accounts, groups, computers, and privileges. Learn how to detect LDAP reconnaissance and how cyberattackers can use this method as part of an attempt to compromise your environment.
What is LDAP?
Since the early 1990s, LDAP has been the industry standard protocol for directory information service access and management over IP networks. LDAP sessions follow a request-and-response pattern in which a client system sends a request to an LDAP server and receives a response in return. Applications use LDAP to communicate with Active Directory.
What is LDAP reconnaissance?
LDAP reconnaissance is a technique attackers use to gather information from an organization’s Active Directory by querying the directory through LDAP (Figure 1). With this information, they can spot weak points or high-privilege accounts to target for further attacks, such as privilege escalation or lateral movement within the network.
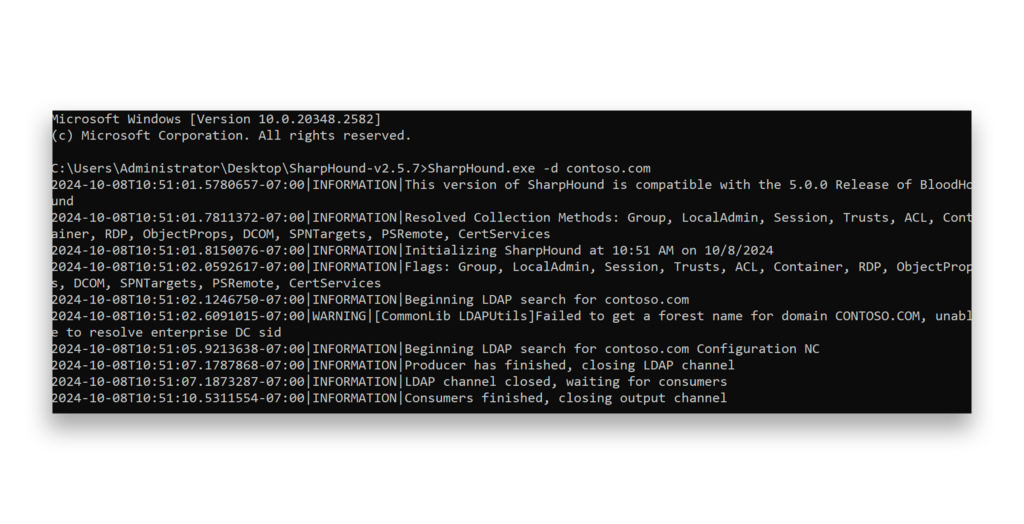
How can you detect LDAP reconnaissance?
Detection is the best defense when dealing with LDAP reconnaissance. An EDR solution that uses the Microsoft-Windows-LDAP-Client ETW Provider can detect suspicious LDAP queries (Figure 2). Another approach would be to implement network monitoring that analyzes LDAP traffic.
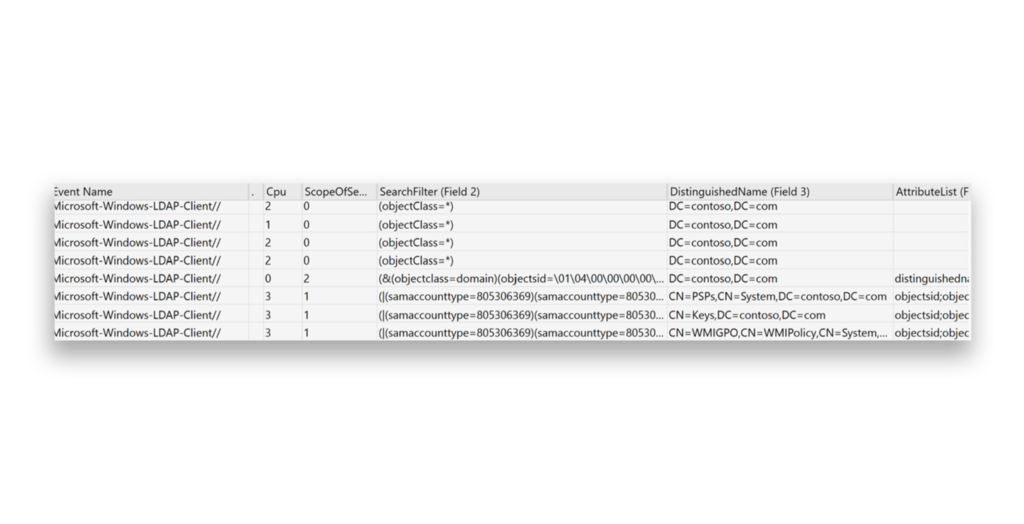
Threat actor profiles
The following threat actors are known to have used LDAP queries for reconnaissance:
- Black Basta (MITRE ATT&CK Software S1070)1
- BlackByte Ransomware2
- BlackCat (MITRE ATT&CK Software S1068)3
- BlackSuit4
- Goblin Panda aka Earth Zhulong5
- LockBit6
- Storm-05017
- Storm-15678
LDAP reconnaissance tools
The following tools, most of which are available on github.com, can be used to perform LDAP reconnaissance:
- Active Directory Explorer
- AdFind
- adrecon/ADRecon
- BloodHoundAD/SharpHound
- PowerShellMafia/PowerSploit
- Threat overview
ATT&CK Tactic: Discovery
On September 26, 2024, Microsoft reported that STORM-0501 used ADRecon.ps1, an Active Directory reconnaissance script, in ransomware attacks. This PowerShell script helped the group gather crucial domain information, such as users, groups, and permissions.9
On August 26, 2024, The DFIR Report highlighted that the BlackSuit ransomware gang used SharpHound for LDAP reconnaissance during attacks. By utilizing SharpHound, BlackSuit mapped out Active Directory environments.10
On October 5, 2023, Trend Micro reported that the Akira ransomware gang used SharpHound for LDAP reconnaissance to map out Active Directory environments during attacks.11
On July 6, 2023, Microsoft reported that the BlackByte ransomware gang used tools like AdFind to perform LDAP reconnaissance during attacks. By leveraging AdFind, the gang gathered information about Active Directory, such as user accounts and network structure, enabling the identification of high-value targets and escalation of privileges.12
On June 2023, LogPoint reported that the LockBit ransomware gang used AdFind for LDAP reconnaissance as part of its attack strategy. By using AdFind, LockBit was able to query Active Directory, collecting data on users, groups, and computers.13
On February 8, 2023, Trend Micro reported that the Earth Zhulong group used SharpHound for LDAP reconnaissance to map Active Directory environments in Southeast Asian firms. After gathering information on users and permissions, the group escalated privileges and spread malware across networks.14
On October 12, 2022, Trend Micro reported that the Black Basta ransomware gang used SharpHound for LDAP reconnaissance through the Brute Ratel C2 framework. They ran SharpHound via Brute Ratel, injecting it into the svchost.exe process to process JSON output files. This allowed them to map out Active Directory, gather data, escalate privileges, and so on.15
On June 13, 2022, Microsoft reported that the BlackCat ransomware gang used the tool AdFind to perform LDAP reconnaissance in its attacks. They leveraged AdFind to query Active Directory, collecting information on users, groups, and computers.16
Semperis snapshot
LDAP reconnaissance remains a relevant attack technique because many organizations rely heavily on Active Directory for managing network resources and permissions. Attackers use LDAP reconnaissance to gather valuable information about network structures, privileged accounts, and potential attack paths. As long as Active Directory is widely used, LDAP reconnaissance will remain a key phase in attacks, which makes it important for defenders to monitor these LDAP queries.
Additional reading
Endnotes
- https://attack.mitre.org/software/S1070/
- https://malpedia.caad.fkie.fraunhofer.de/details/win.blackbyte
- https://attack.mitre.org/software/S1068/
- https://malpedia.caad.fkie.fraunhofer.de/details/win.blacksuit
- https://malpedia.caad.fkie.fraunhofer.de/actor/goblin_panda
- https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-165a
- https://malpedia.caad.fkie.fraunhofer.de/actor/storm-0501
- https://malpedia.caad.fkie.fraunhofer.de/actor/storm-1567
- https://www.microsoft.com/en-us/security/blog/2024/09/26/storm-0501-ransomware-attacks-expanding-to-hybrid-cloud-environments/
- https://thedfirreport.com/2024/08/26/blacksuit-ransomware/
- https://www.trendmicro.com/vinfo/us/security/news/ransomware-spotlight/ransomware-spotlight-akira
- https://www.microsoft.com/en-us/security/blog/2023/07/06/the-five-day-job-a-blackbyte-ransomware-intrusion-case-study/
- https://www.logpoint.com/wp-content/uploads/2023/07/etp-lockbit.pdf
- https://www.trendmicro.com/en_be/research/23/b/earth-zhulong-familiar-patterns-target-southeast-asian-firms.html
- https://www.trendmicro.com/en_be/research/22/j/black-basta-infiltrates-networks-via-qakbot-brute-ratel-and-coba.html
- https://www.microsoft.com/en-us/security/blog/2022/06/13/the-many-lives-of-blackcat-ransomware/
