[Editor’s note: This article is a guest post by TAG CEO and founder Ed Amoroso.]
Cybersecurity practitioners working for federal agencies in the United States know that they must learn to decode various acronyms such as FedRAMP, FISMA, RMF, and on and on. They must do so because the standards and frameworks these acronyms represent are intended to guide the decision-making by public sector teams tasked with protecting data, systems, and networks from cyber threats.
At the sector level, things get more specific. Defense departments must deal with their own local set of acronyms, such as CMMC. Health care agencies must deal with acronyms such as HIPAA. And financial agencies must deal with acronyms such as GLBA. Certainly, these frameworks will apply generally to both public and private sector organizations, but no one would dispute the complexity involved.
The challenge we’ve seen in our research and advisory work at TAG is that with so many different standards and frameworks, there is an inevitable overlapping of guidelines, mandates, requirements, and best practices. This creates an environment where agencies must navigate not only technical requirements but also compliance reporting, governance expectations, and risk assessments, each with its own timelines and enforcement mechanisms.
As if this was not enough, the dynamic nature of cyber threats, such as supply chain attacks and vulnerabilities in critical infrastructure, have prompted additional legislative and executive actions, such as Executive Order 14028 on Improving the Nation’s Cybersecurity, which mandates government-wide initiatives like Zero Trust adoption and enhanced software supply chain security, often audited by bodies like the Government Accountability Office (GAO).
Navigating federal cyber compliance
Given this regulatory compliance challenge, the question most often asked of TAG analysts by public sector agency teams at both the federal and local levels is this: What is the best way to develop an effective cybersecurity program that will minimize the friction of dealing with so many disparate frameworks and standards? Our answer is rooted in three key cybersecurity strategy components that we view as best for public sector teams.
First, we strongly suggest developing a commitment to automation. Modern regulatory obligations can only be met through a formal discipline of Governance, Risk, and Compliance (GRC). The good news is that excellent commercial platforms are available for government teams, and they can be introduced to any type of existing compliance program, even ones performed manually, without too much trouble.
Second, we recommend a risk-based approach to all security decisions. This implies having a good understanding of the real security issues that are directly relevant to that agency. Perhaps the best example of this involves Microsoft Active Directory (AD), which we view at TAG as being perhaps the most essential aspect of any cyber risk program. Every offensive team will target AD, so federal programs must address this type of baseline, practical risk.
Third, we recommend that all public sector agencies use the Cybersecurity Framework (CSF) from the National Institute of Standards and Technology (NIST). It is built on a comprehensive set of requirements in NIST Special Publication (SP) 800-53 (rev 5) and it offers an excellent roadmap for public sector teams to improve their security in a stepwise manner. Best of all, NIST CSF maps nicely to the plethora of acronyms listed previously.
In the remaining sections, we focus on NIST CSF, now in version 2.0, and we make the case that it is an excellent choice on which to base a cyber compliance program. We often reference the framework as offering “blanket coverage,” because virtually every security requirement we’ve encountered in the variety of acronyms is addressed to some degree in NIST. This makes it a good baseline choice—including for private and non-U.S. security teams.
What is NIST CSF 2.0?
NIST CSF 2.0, released in August 2023, builds on the original 2014 version (CSF 1.0) to help organizations manage and reduce cybersecurity risks. The original framework comprised five core functions—Identify, Protect, Detect, Respond, and Recover—that provide a lifecycle approach to cybersecurity. Many cybersecurity programs were organized around these functions, although our coaching is that this might not be the best approach.
These NIST CSF functions are broken into categories and more detailed subcategories, which are mapped to informational references like NIST Special Publications and ISO standards. CSF 2.0 retains the flexibility and accessibility of its predecessor, enabling organizations of all sizes and industries to tailor its implementation to their specific risk environments, resources, and business objectives.
A significant enhancement in CSF 2.0 is its increased focus on governance as a new category under the “Identify” function, addressing the importance of leadership, cybersecurity strategy, and organizational policies in managing cyber risks. Another key addition is the expansion of guidance for managing supply chain risks, reflecting the growing importance of third-party risk management in cybersecurity.
NIST CSF 2.0 also incorporates updates to align with modernized NIST standards, such as updates to cryptographic controls and expanded considerations for emerging technologies like cloud, artificial intelligence, and operational technology. These changes make the framework more relevant to the current threat landscape and the diverse technology environments organizations now face.
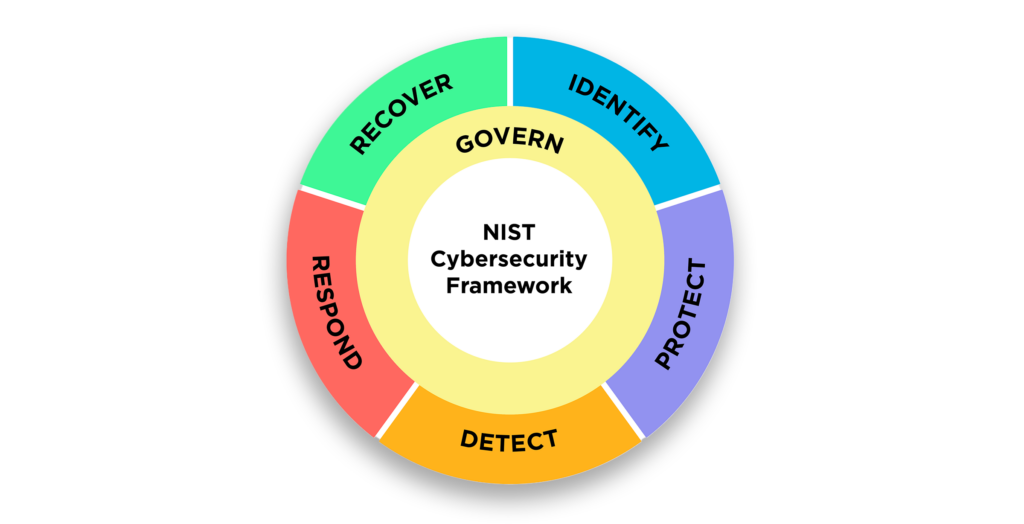
Compared to CSF 1.0, version 2.0 takes a more global perspective by improving its applicability to international standards and frameworks, including across the public sector, promoting greater interoperability. It also places greater emphasis on implementation guidance, offering improved resources, such as profiles and implementation examples, to help organizations operationalize the framework effectively.
While CSF 1.0 provided a strong foundation, CSF 2.0 enhances the framework by incorporating lessons learned from nearly a decade of adoption, making it more comprehensive, scalable, and capable of addressing the evolving cybersecurity challenges faced by all types of organizations today. In the section below, let’s dig into how the framework works in the context of federal agency cybersecurity challenges.
Mapping to federal cyber requirements
The first insight that we hope to help federal agency compliance teams understand is that modern GRC platforms from good commercial vendors such as ServiceNow, Metric Stream, and Archer will provide automated support in performing mappings from NIST CSF 2.0 to other frameworks. This is an amazingly helpful function, because it replaces the manual efforts many of us remember doing before such platforms were available.
That said, it does help to review how NIST CSF 2.0 supports most federal agency requirements. Our discussion below must be reviewed notionally, however, because in the U.S. with political elections at the federal and state level, the applicable cyber requirements, mandates, and laws change quickly. Executive Orders, for example, change with the flick of a pen, so readers would be wise to avoid trying to seek microscopic mappings in reports like this.
With its comprehensive approach to risk management, NIST CSF 2.0 aligns with the most critical federal directives and standards, including the Federal Information Security Modernization Act (FISMA), OMB Circular A-130, Executive Order (EO) 14028, and CISA’s Binding Operational Directives (BODs). By integrating these mandates into its framework, CSF 2.0 allows agencies to streamline compliance efforts and strengthen their overall cybersecurity posture.
Alignment with FISMA and NIST SP 800-53
FISMA, as the cornerstone of federal cybersecurity law, requires federal agencies to implement risk-based information security programs. The NIST CSF 2.0 functions referenced above—Identify, Protect, Detect, Respond, and Recover—align directly with FISMA’s emphasis on categorizing risks, implementing controls, and conducting continuous monitoring. Federal agency security teams will benefit from such alignment.
The framework also maps to NIST Special Publication (SP) 800-53, which specifies security and privacy controls that apply directly to federal systems. For instance, the governance enhancements in CSF 2.0 complement SP 800-53’s emphasis on organizational policies, roles, and responsibilities. By using CSF 2.0 as a higher-level framework, federal agencies can ensure their programs are rooted in SP 800-53’s detailed requirements.
Compliance with executive orders and directives
NIST CSF 2.0 also supports compliance with Executive Order 14028, which mandates improvements to federal cybersecurity following high-profile breaches like SolarWinds. EO 14028 emphasizes zero trust architecture, improved threat detection, and secure software development. The framework’s expanded focus on supply chain risk management and emerging technologies aligns with these directives.
For example, CSF 2.0 provides categories and subcategories that address vendor due diligence, continuous monitoring, and secure software lifecycle management. It offers agencies a structured way to implement the requirements of CISA’s Zero Trust Maturity Model and secure the software supply chain as required by EO 14028. (Again, we remind readers that EO mandates can change quickly, especially with Presidential Administration changes.)
Integration with CISA’s Binding Operational Directives
CISA’s Binding Operational Directives (BODs), such as BOD 22-01 on known exploited vulnerabilities, demand timely actions to mitigate specific risks. The CSF 2.0 Detect and Respond functions enable agencies to operationalize these directives through improved incident response planning, proactive cyber threat detection, and vulnerability and exposure management processes.
Furthermore, the framework’s emphasis on continuous improvement aligns well with BODs’ requirements for rapid and measurable action. NIST CSF 2.0’s iterative approach ensures agencies can adjust their strategies in response to evolving CISA directives and threat intelligence. In the coming years, we predict at TAG that significantly increased threats from nation states will demand better continuous threat intelligence management by federal agencies.
Support for privacy and data protection mandates
NIST CSF 2.0’s alignment with privacy frameworks, including NIST Privacy Framework and mandates such as the Privacy Act of 1974 and CUI (Controlled Unclassified Information) guidelines, allows agencies to manage data protection requirements in conjunction with cybersecurity objectives. The updated governance category explicitly addresses the need for policies and controls that balance cybersecurity with privacy, enabling agencies to meet dual compliance requirements.
Action plan
We hope that the case has been made that federal agencies should seriously consider use of NIST CSF 2.0 as the foundational basis for its overall protection program. By mapping to FISMA, EO 14028, CISA directives, and other mandates, NIST CSF 2.0 offers federal agencies a cohesive framework to unify compliance while enhancing their overall security resilience. We hope this guidance has been useful—and we always hope to hear from you.
