In hybrid identity environments, attackers that manage to breach either the on-premises Active Directory or cloud-based Entra ID typically attempt to expand their reach throughout your identity environment. If your identity infrastructure includes Entra ID, make sure you understand how to detect and defend against Entra Connect compromise.
What is Entra Connect compromise?
A Microsoft Entra Connect compromise happens when attackers target the Microsoft Entra Connect server. This server uses an ADSync account to synchronize identities between on-premises Active Directory and Entra ID in the cloud. This account has special permissions to manage the sync process, and if attackers gain control of the Entra Connect server, they can use the ADSync account to access the cloud environment. They might also perform a DCSync attack because of the permissions the account has within Active Directory.
Both password hash synchronization (PHS) and pass-through authentication (PTA) can be exploited to steal more credentials. For example, attackers can use AADInternals to extract credentials and obtain the plaintext password of the ADSync account, which grants access to both the on-premises Active Directory and Entra ID environments (Figure 1).
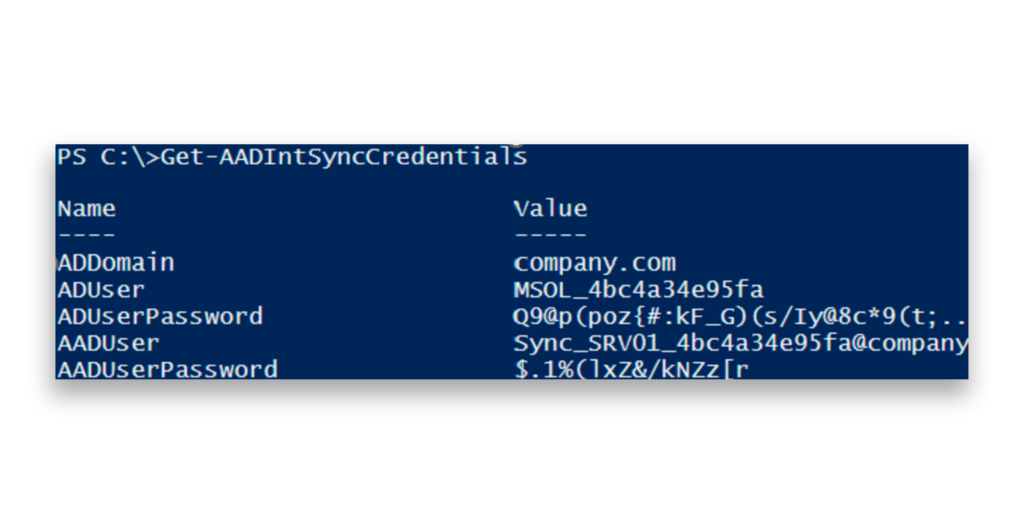
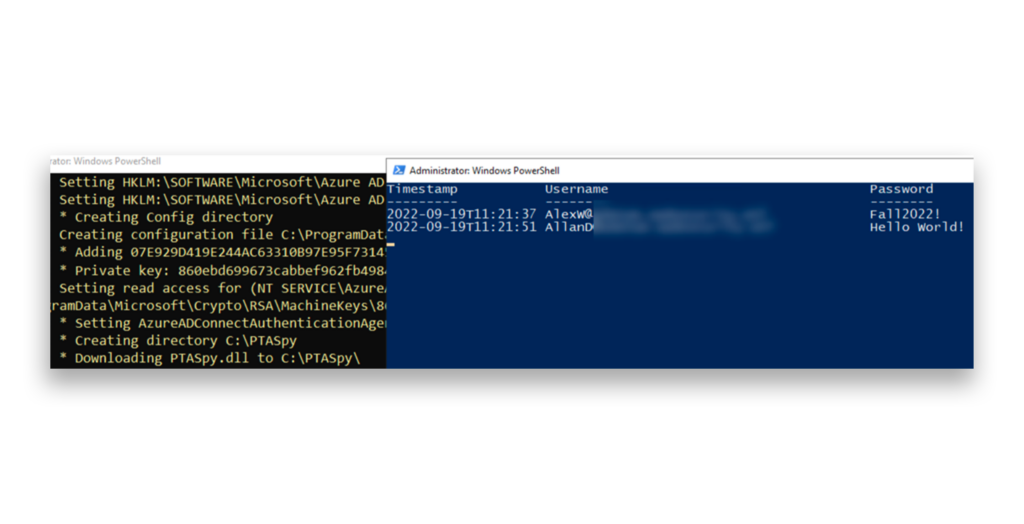
Figure 2 shows an example showing how AADInternals can exploit pass-through authentication by compromising the PTA agent, extracting its certificate, and setting up a malicious agent. This enables attackers to intercept and log credentials during authentication.
How to defend against Entra Connect compromise
To protect the Entra Connect server, apply the following key recommendations:
- Minimize the number of members in the local Administrators group of the Entra Connect server.
- Treat the Entra Connect server as a Tier 0 asset, giving it the highest level of protection.
- Ensure that Entra Connect is kept up to date with the latest security patches.
- Deploy an endpoint detection and response (EDR) solution on your Entra Connect server.
- Set up an additional conditional access policy to restrict the use of the On-Premises Directory Synchronization Account, which is excluded from MFA policies. Configure the policy so that this account can be accessed only from IP addresses tied to your Entra Connect servers.
Creating a conditional access policy to restrict the Directory Synchronization Account might look like the following:
- Assignments
- Users or workload identities: Select the Directory Synchronization Account (Sync_*).
- Cloud apps: Target All cloud apps or limit it to necessary ones.
- Conditions
- Locations: Specify trusted IP addresses associated with your Entra Connect servers. You can check the Sign-In logs from the last 30 to 90 days to identify the IP addresses linked to your Entra Connect server.
- Access controls
- Grant: Ensure that access is allowed only from the specified locations.
- Exclude MFA: The Directory Synchronization Account is excluded from MFA by default.
This policy limits the account’s use to trusted IPs, preventing unauthorized access from other locations.
Microsoft has announced that it will be reducing the permissions for the Directory Synchronization Accounts role, which is used in both Microsoft Entra Connect Sync and Cloud Sync. This is great news for defenders because it reduces the attack surface in Entra ID.
The Directory Synchronization Account now has only the microsoft.directory/onPremisesSynchronization/standard/read permission, which limits what it can do in Entra ID.1 However, the Entra Connect server remains a Tier 0 asset because the account still holds significant permissions in the on-premises Active Directory. Therefore, it is still a critical system to secure.
How to detect Entra Connect compromise
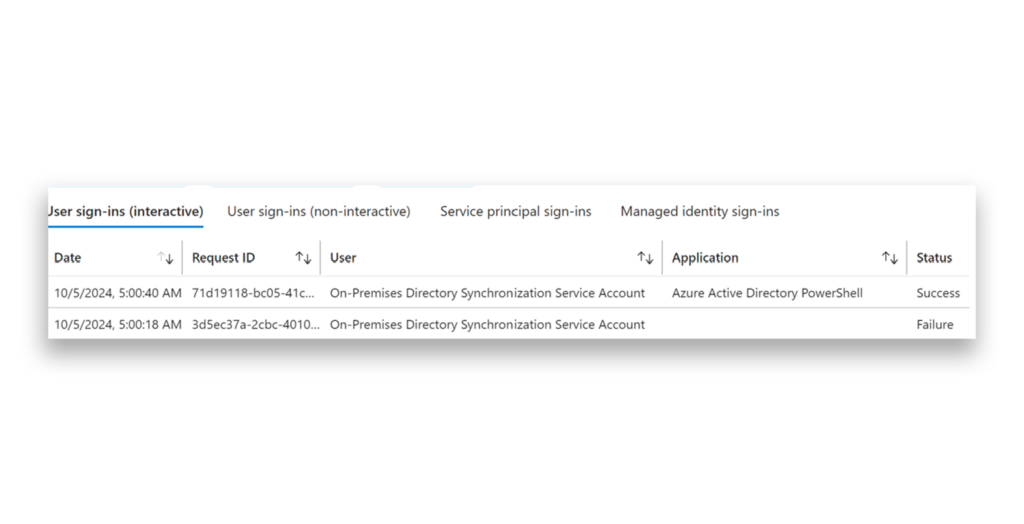
Set up a Log Analytics rule in Entra ID to trigger an alert whenever the Sync_* account, also known as the On-Premises Directory Synchronization account, authenticates to any application other than Microsoft Azure Active Directory Connect. This step helps to ensure that you can monitor and detect any unauthorized or suspicious activity, as the account should typically be used only with this application. For example, Figure 3 shows this account authenticating to Entra ID PowerShell, which should immediately sound alarm bells.
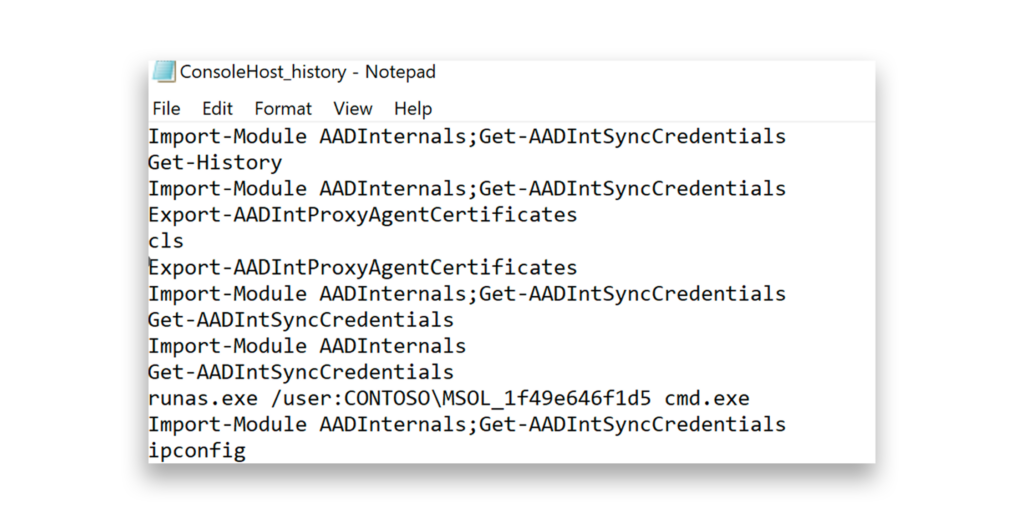
From a forensic angle, PowerShell console history logs or Scriptblock logging can be valuable, especially for tracking tools like AADInternals (Figure 4).
No specific events are tied to pass-through authentication for monitoring. However, a good approach for tracking potential issues is to monitor for any suspicious access to Cryptographic API (CAPI) keys. Monitoring this activity can help catch pass-through authentication certificate exports, which might indicate unauthorized actions or an attempt to exploit the pass-through authentication system as part of Entra Connect compromise. AADInternals has been documented the process that such an attack might use.2
Threat actor profiles
The threat actor Storm-0501 has been known to use Entra Connect compromise in its operations.3
Entra Connect compromise tools
Gerenios/AADInternals, available on github.com, can be used to extract or harvest credentials from the Entra Connect server.
Threat overview
ATT&CK Tactic: Credential Access
On September 26, 2024, Microsoft reported that the Storm-0501 group used Entra ID Connect compromise to obtain the credentials for the on-premises Directory Synchronization Account. With these credentials, the attackers were able to authenticate and get an access token for Microsoft Graph. This enabled them to reset or change Entra ID passwords for any hybrid accounts.4
Semperis snapshot
Despite reducing permissions for the Directory Synchronization Account in Entra ID to read-only, Entra Connect still needs to be treated as a Tier 0 asset. The account retains powerful permissions within the on-premises Active Directory, which remains a critical point of control for hybrid environments. If compromised, attackers can leverage these on-premises permissions to escalate their access, perform lateral movement, and compromise the entire infrastructure.
Endnotes
- https://github.com/MicrosoftDocs/entra-docs/commit/6cef860add24f6741d00bda9133ec7c4be91fd81
- https://aadinternals.com/post/pta/
- https://malpedia.caad.fkie.fraunhofer.de/actor/storm-0501
- https://www.microsoft.com/en-us/security/blog/2024/09/26/storm-0501-ransomware-attacks-expanding-to-hybrid-cloud-environments/
