Many cyberattacks go undetected until the damage is done, despite organizations’ efforts to prevent them. And many successful identity attacks use the same tried-and-true techniques that have worked for years, such as password spray and brute force attacks. Microsoft estimates that password spray attacks are responsible for more than a third of all account compromises in organizations. In fact, one of the most successful recent password spraying attacks was Midnight Blizzard, which Microsoft discovered in January.
So why are identity-related attacks—even ones that are old news, like password spraying—so hard to prevent? Part of the problem is lack of fundamental identity system security practices, a failure that has been well documented by Microsoft and has been observed by the Semperis Breach Preparedness & Response Services team, too. Continuously scanning the AD and Entra ID environment for vulnerabilities and closing those security gaps can prevent many of the breaches our team has seen.
But even for organizations with the best identity system security practices, some attacks are notoriously hard to detect. The main challenge is separating the signal from the noise. In many cases, organizations’ cybersecurity tools can’t detect advanced attacks—or the attacks are detected but the noise is so high the signal flies under the radar.
Organizations need better ways to uncover prevalent attacks. That’s where Semperis’ new offering—Lightning Identity Runtime Protection—comes in.
AI-powered, expert-built live attack pattern detection
Lightning Identity Runtime Protection takes an innovative approach to detecting the most consistently successful attacks by merging deep experience in machine learning with real-world knowledge about how attacks work in the wild. Led by Semperis Chief Scientist Dr. Igor Baikalov, an expert in building AI and machine learning models specifically in the context of identity security, our threat research team looked at the attack techniques that continually make the headlines and developed ML algorithms that detect these pervasive attacks.
Building on the identity threat prevention, detection, and response capabilities in Directory Services Protector (DSP), Lightning IRP captures and analyzes authentication events to determine whether they are part of an attack pattern or might signal anomalous behavior. The anomaly score uses logon and access activity data to highlight the likelihood of an attack, focusing on high-priority threats:
- Password spray: Monitor logon attempts to detect patterns that indicate a password spray attack
- Brute force: Monitor repeated and rapid logon attempts against a single user to detect potential brute force attacks
- Anomalous logons: Uncover anomalous AD logons
- Anomalous resource access: Monitor user activity and any interaction with services that might indicate an attack on AD services
- Service ticket anomalies: Scan for suspicious service ticket requirements that might indicate a Kerberoasting attack on AD
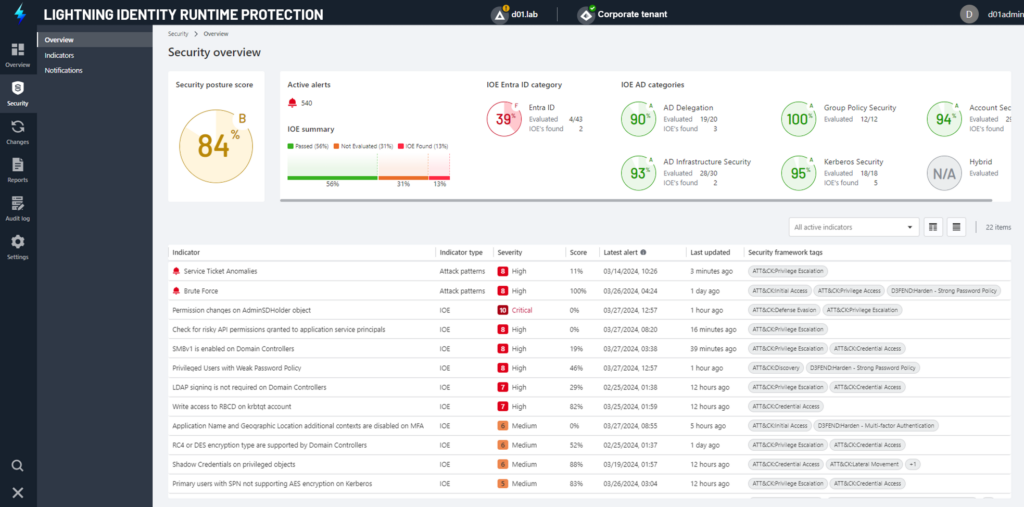
The data Lightning IRP provides can help security teams intercept or prevent a security incident by identifying how a network was breached, the backdoors that were created, and the privileged credentials that were compromised. Along with the notification of a potential attack, Lightning IRP provides the details required to mitigate it and generates a Syslog event so an alert can be sent to a SIEM system.
By helping narrow your focus to the factors that indicate a high-priority threat, Lightning IRP helps you reduce risk and accelerate response time for identity-related incidents.
Expanding identity threat detection and response for Entra ID
In addition to introducing Identity Runtime Protection, we’ve recently expanded our identity threat detection and response capabilities for Entra ID with the latest release of Directory Services Protector, building on our long-established track record for helping organizations protect their hybrid identity systems.
DSP for Entra ID provides specific indicators for Entra ID, a hybrid identities view so you can track changes across the hybrid environment, and some new ways to remediate unwanted changes in Entra ID, including the ability to:
- Create custom rules to address specific Entra ID changes
- Auto-undo or notify users when a specific change is detected
- Filter and search for triggered rules
Because identity systems are the top target for cyberattackers, organizations need solutions that can protect AD and Entra ID before, during, and after attacks. DSP provides unmatched visibility into threats and powerful remediation capabilities across the hybrid AD environment. Now with IRP, organizations can solve another difficult challenge: Uncovering true threats in the blizzard of attack signal noise, reducing the risk of a successful identity system attack.

