The Five Eyes report on Active Directory compromise lists NTDS.DIT extraction as a top attack tactic. With access to this file, attackers might be able to extract passwords hashes, which they can lead to a complete compromise of Active Directory. Learn more about NTDS.DIT extraction, how to detect it, and how to defend against it.
What is NTDS.DIT?
NTDS.DIT, which stands for the New Technology Directory Services Directory Information Tree, is the database for Active Directory Domain Services (AD DS). This database stores directory data and makes that data available to network users and administrators. This data includes password hashes and user details for all computer and user objects in the domain—powerful information in the wrong hands.
What is NTDS.DIT extraction?
Attackers extract NTDS.DIT by making a copy of the NTDS.DIT file from a domain controller (DC). Access to NTDS.DIT is one reason attackers target DC backups and another reason why maintaining secure, dedicated, AD-specific backups is a best practice.
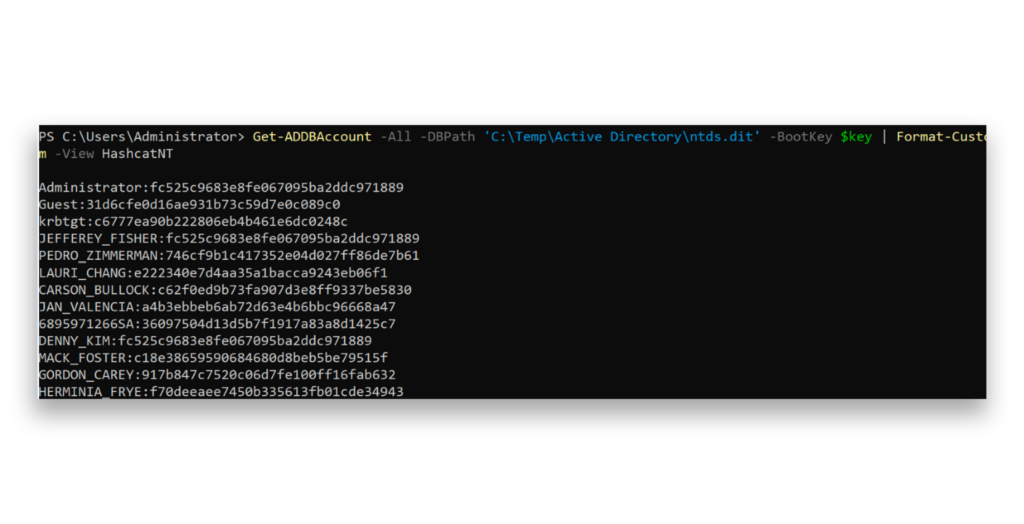
Using the extracted NTDS.DIT file along with an extracted SYSTEM registry hive (which stores encryption keys), attackers can either crack the hashes offline or use them in a Pass the Hash attack, bypassing the need to crack them (Figure 1). Once attackers gain access to the password hashes, they can control all accounts, including Domain Admin accounts, compromising your entire network.
How to defend against NTDS.DIT extraction
To extract the NTDS.DIT file from a DC, attackers require elevated privileges, typically equivalent to Domain Administrator or Enterprise Administrator. Without such access, they can’t retrieve this sensitive data. To mitigate the risk of NTDS.DIT extraction, defenders should:
- Limit membership in Tier 0 groups, like Domain Admins and Enterprise Admins.
- Closely monitor for any user being added to a Tier 0 group.
- Apply administrative tiering for Tier 0 accounts at a minimum.
- Use tools like Purple Knight to address common vulnerabilities and Forest Druid to identify and mitigate attack paths leading to Tier 0 groups.
How to detect NTDS.DIT extraction
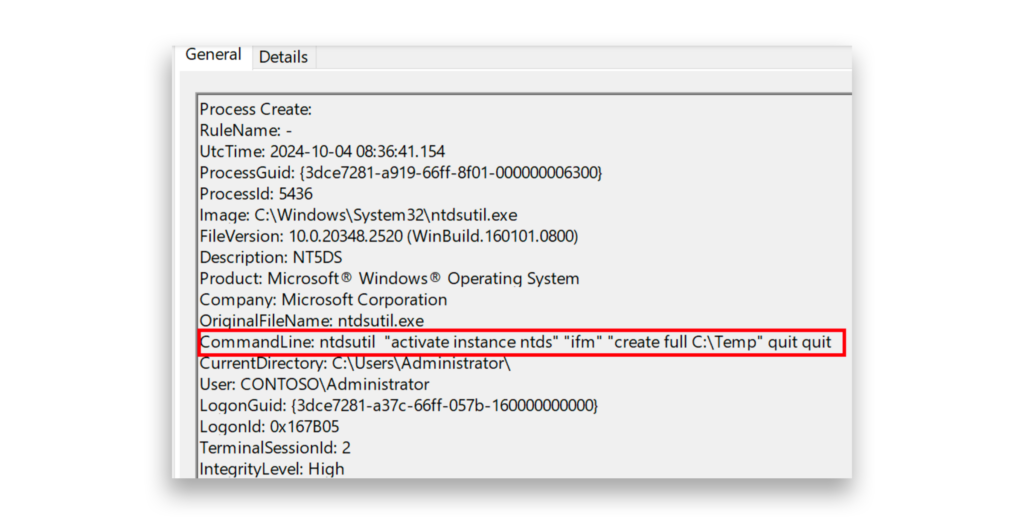
To detect the extraction of NTDS.DIT from a DC, defenders can monitor the use of ntdsutil.exe in the command line, particularly when it contains activate instance ntds, which activates the NTDS instance, and ifm, which creates installation media from Active Directory (Figure 2). This activity is a strong indicator of NTDS.DIT extraction attempts. Most endpoint detection and response (EDR) solutions can log command-line activities, which can help you investigate such attacks.
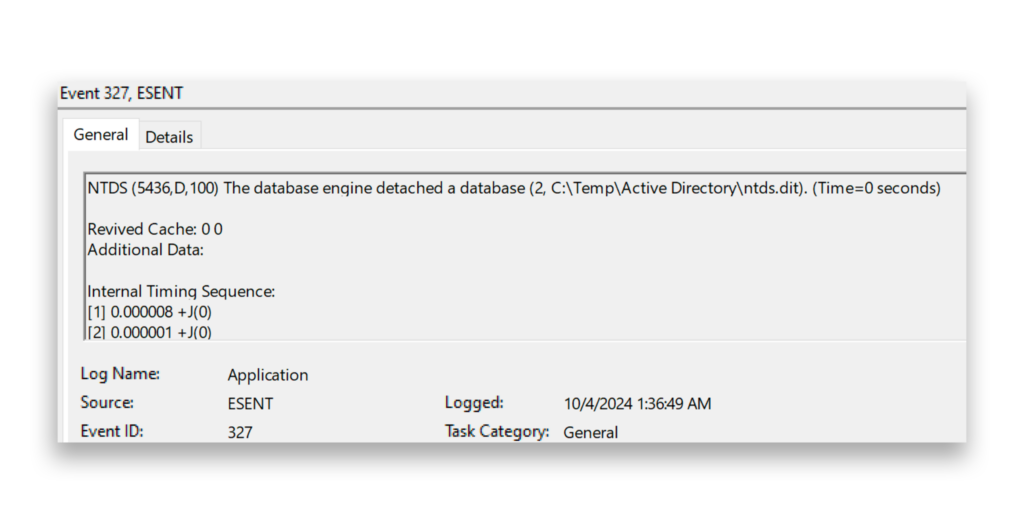
To track NTDS.DIT extraction from a forensic perspective, defenders can review the Application logs on a DC and filter for Event IDs 325 and 327. Both events reveal where the NTDS.DIT file was copied (Figure 3).
Threat actor profiles
The following threat actors have been known to use ntdsutil.exe to extract the NTDS.DIT file.
- APT41 (MITRE ATT&CK Group G0096)1
- CL-STA-00432
- Lazarus Group (MITRE ATT&CK Group G0032)3
- Mustang Panda (MITRE ATT&CK Group G0129)4
- RA World aka RA Group5
- Rhysida6
- Sandworm Team aka ELECTRUM, Telebots, IRON VIKING, BlackEnergy, Quedagh, Voodoo Bear, IRIDIUM, Seashell Blizzard, FROZENBARENTS, APT44 (MITRE ATT&CK Group G0034)7
- Storm-15678
- Volt Typhoon (MITRE ATT&CK Group G1017)9
NTDS.DIT extraction tools
The following tools can be used to copy the NTDS.DIT database:
- Ntdsutil
- csababarta/ntdsxtract
- zcgonvh/NTDSDumpEx
Threat overview
ATT&CK Tactic: Credential Access
On September 6, 2024, Palo Alto Networks reported that Stately Taurus (aka Mustang Panda), a China-based threat actor, used Vssadmin to create a volume shadow copy on DCs, enabling it to steal the NTDS.DIT file. Afterward, the attacker copied the SYSTEM hive from the registry to retrieve the boot key, which enabled it to decrypt the NTDS.DIT file. This provided the group access to usernames and password hashes from Active Directory accounts.10
On July 22, 2024, Palo Alto Networks reported that the RA World ransomware gang used tools like Impacket to copy the NTDS.DIT file from DCs, giving it access to usernames and password hashes. The gang also dumped the SAM and SYSTEM registry hives to decrypt and crack the hashes offline.11
On May 20, 2024, it was reported that the Akira ransomware gang escalated privileges to exfiltrate the NTDS.DIT file from DCs. The gang did this by shutting down the controller’s virtual machine (VM), copying the VMDK files to another VM, and extracting the NTDS.DIT and SYSTEM hive files. The SYSTEM hive provided the decryption keys for the password hashes in the NTDS.DIT, allowing the attackers to crack the passwords or use Pass the Hash techniques to gain access to additional systems.12
On August 8, 2023, Check Point Research reported that the Rhysida ransomware gang used ntdsutil.exe to create a backup of the NTDS.DIT file during its attacks. This file, which contains sensitive Active Directory data such as usernames and password hashes, was stored in a folder named temp_l0gs.13
On June 14, 2023, Palo Alto Networks revealed that the CL-STA-0043 threat actor copied the NTDS.DIT file from DCs as part of a campaign targeting governments in the Middle East and Africa. The attacker used this file to obtain password hashes and, with the help of the copied SYSTEM registry hive, decrypted the credentials.14
On May 24, 2023, Microsoft reported that Volt Typhoon, a China-based threat actor, used ntdsutil.exe to create installation media from DCs, either locally or remotely. This enabled the attackers to obtain usernames and password hashes stored in the media, which were intended to set up new DCs.15
On October 14, 2022, Microsoft reported that Seashell Blizzard (formerly known as IRIDIUM), a Russian-based threat actor, used ntdsutil.exe to back up Active Directory databases during its ransomware attacks. By creating these backups, the attacker extracted usernames and password hashes from every Active Directory account.16
On September 8, 2022, Cisco Talos reported that the Lazarus Group used the vssadmin tool to create shadow copies of volumes and exfiltrate the NTDS.DIT file containing Active Directory data. By copying the NTDS.DIT file through these backups, Lazarus gained access to critical account credentials.17
On August 18, 2022, Group-IB reported that the APT41 threat group used tools like vssadmin to create shadow copies of volumes to exfiltrate the NTDS.DIT file. This file contains sensitive data, including usernames and password hashes from Active Directory.18
Semperis snapshot
NTDS.DIT extraction is a method attackers use to take control of an entire Active Directory environment. By copying the NTDS.DIT file and the SYSTEM registry hive from a DC, attackers can gain access to all password hashes in the system. These hashes can then be cracked or used in Pass-the-Hash attacks, giving attackers control of critical accounts, including Domain Admin accounts.
Learn more about protecting Active Directory
- Download Purple Knight
- Download Forest Druid
- Semperis Directory Services Protector (DSP)
- AD Security 101: Pass the Hash
Endnotes
- https://attack.mitre.org/groups/G0096/
- https://malpedia.caad.fkie.fraunhofer.de/actor/cl-sta-0043
- https://attack.mitre.org/groups/G0032/
- https://attack.mitre.org/groups/G0129/
- https://www.darkreading.com/ics-ot-security/fast-growing-ra-ransomware-group-goes-global
- https://malpedia.caad.fkie.fraunhofer.de/details/win.rhysida
- https://attack.mitre.org/groups/G0034/
- https://malpedia.caad.fkie.fraunhofer.de/actor/storm-1567
- https://attack.mitre.org/groups/G1017/
- https://unit42.paloaltonetworks.com/stately-taurus-abuses-vscode-southeast-asian-espionage/
- https://unit42.paloaltonetworks.com/ra-world-ransomware-group-updates-tool-set/
- https://gbhackers.com/akira-ransomware-privilege-escalation/#google_vignette
- https://research.checkpoint.com/2023/the-rhysida-ransomware-activity-analysis-and-ties-to-vice-society/
- https://www.paloaltonetworks.com/blog/security-operations/through-the-cortex-xdr-lens-uncovering-a-new-activity-group-targeting-governments-in-the-middle-east-and-africa/
- https://www.microsoft.com/en-us/security/blog/2023/05/24/volt-typhoon-targets-us-critical-infrastructure-with-living-off-the-land-techniques/
- https://www.microsoft.com/en-us/security/blog/2022/10/14/new-prestige-ransomware-impacts-organizations-in-ukraine-and-poland/
- https://blog.talosintelligence.com/lazarus-three-rats/
- https://www.group-ib.com/blog/apt41-world-tour-2021/
