Password spraying detection is a vital ability for all organizations. In a password spraying attack, the attacker attempts to gain unauthorized access by trying a few common or weak passwords across many accounts rather than targeting a single account with many passwords. The idea is to test several passwords, hoping that some users have chosen a weak password.
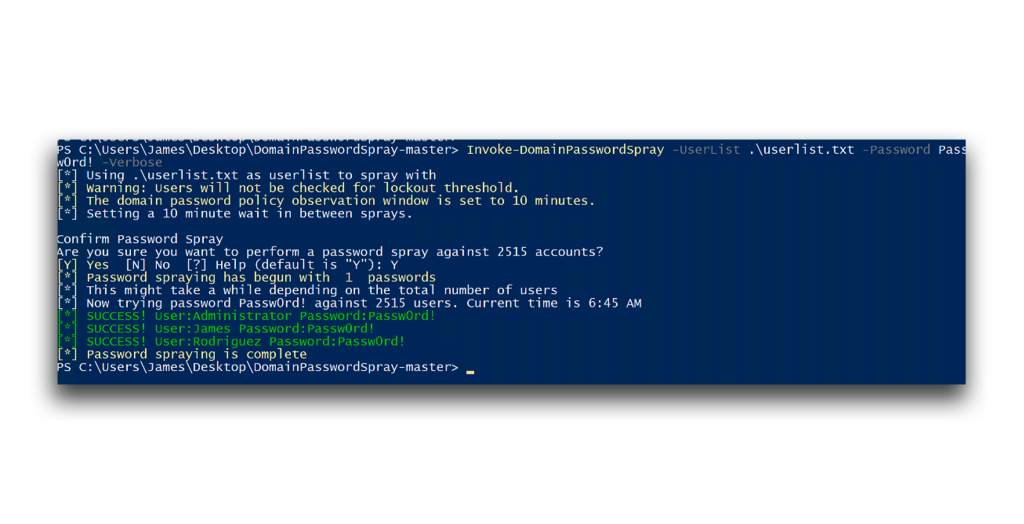
In the context of Active Directory (AD), password spraying attacks are concerning because any authenticated user in an AD environment can use LDAP to query accounts. This enables an attacker with minimal privileges to attempt common or weak passwords across many accounts without triggering account lockout policies (Figure 1).
Why is password spraying detection vital?
Microsoft estimates that password spraying attacks are responsible for more than one-third of all account compromises, highlighting the threat that this method poses to organizations.
Password spraying attacks can generate both a significant amount of activity in the Security event logs of a domain controller (DC) and a large volume of network traffic (Figure 2).
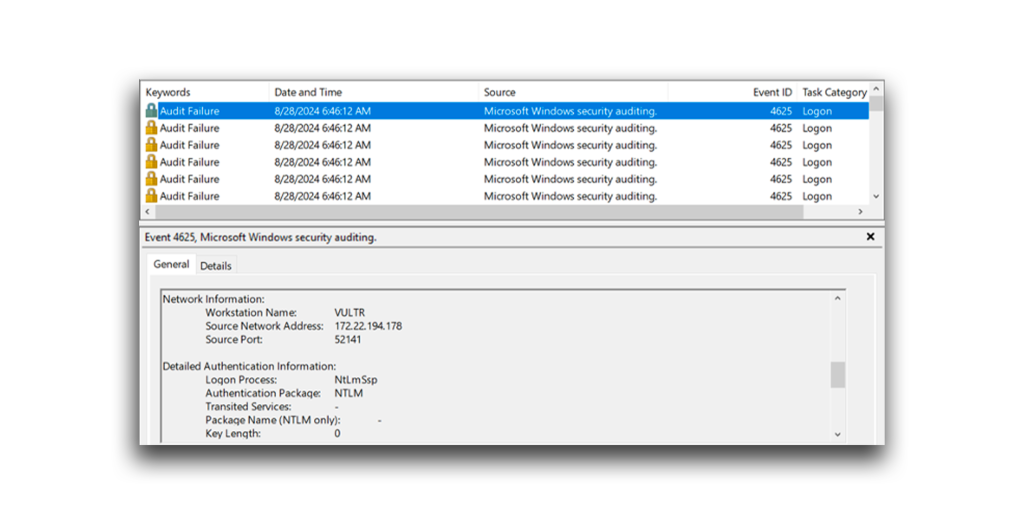
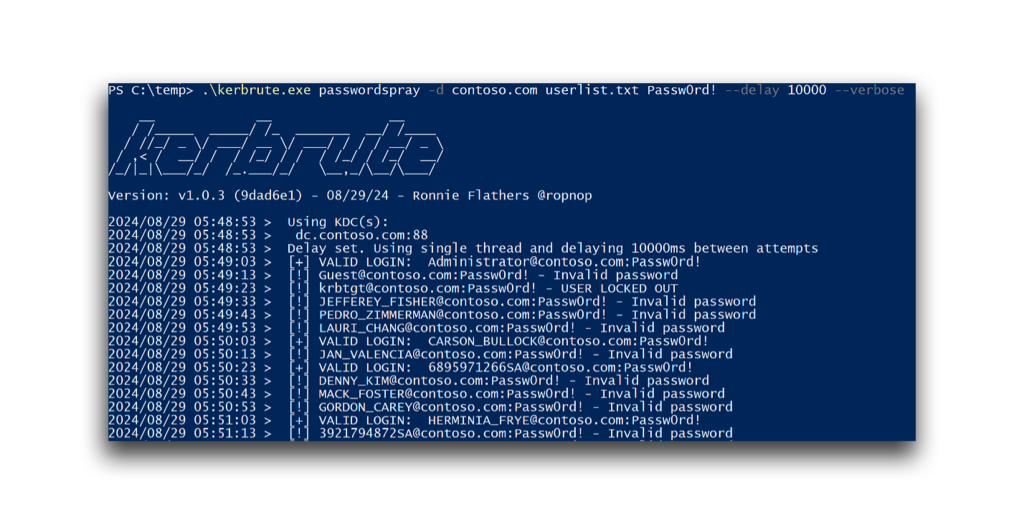
Numerous failed logons can be noisy. Therefore, an attacker might introduce a delay between attempts in a password spraying attack (Figure 3). Because Security event logs on DCs are often generated within seconds, this delay helps the attack blend with normal activity, reducing the chances of detection.
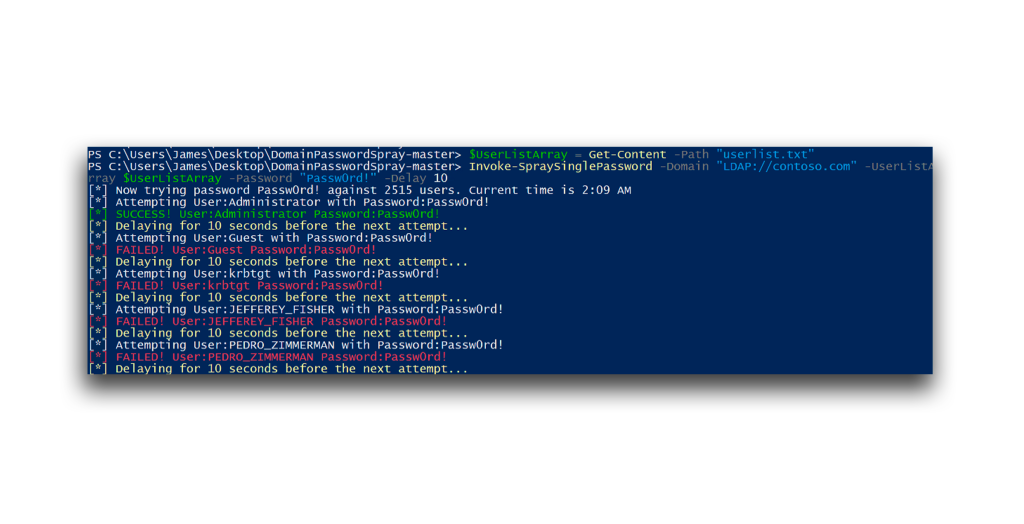
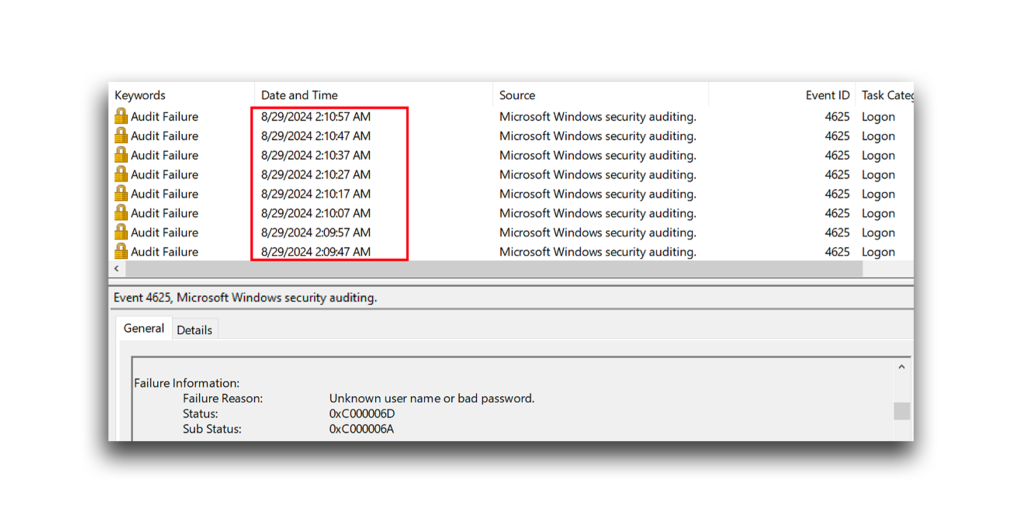
The logs on a DC show that the timestamps of these failed logon attempts occur at consistent intervals, caused by introducing a delay of 10 seconds between each attempt. This spread-out timing makes the activity less suspicious than multiple failed logon attempts that happen simultaneously (Figure 4).
Password spraying using Kerberos pre-authentication
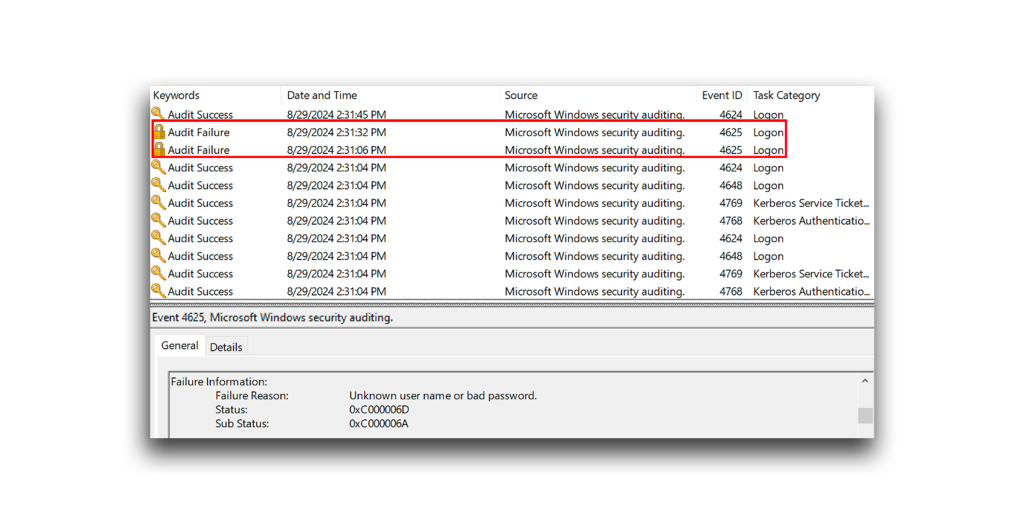
Adding a delay makes a password spraying attack less suspicious. However, the attack will still trigger the An account failed to log on event on the DC.
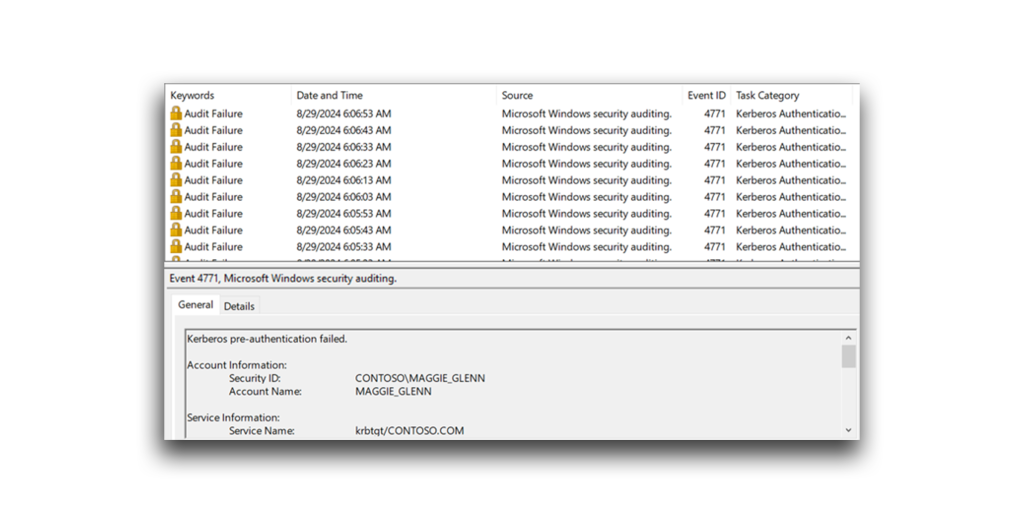
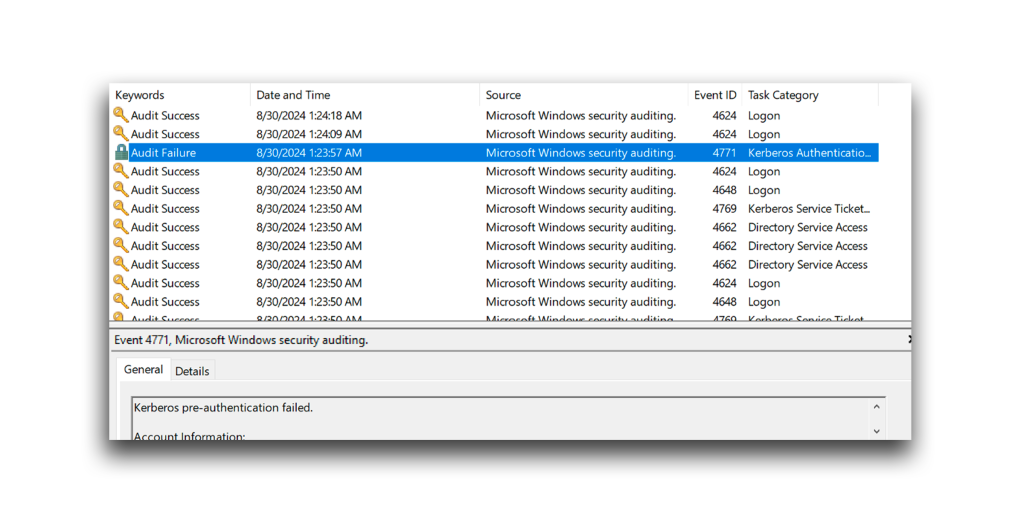
Kerberos pre-authentication can make password spraying detection more difficult. Failed attempts that use such pre-authentication do not generate the standard logon failure events in the Security event logs. In this way, the attacker can guess passwords without triggering the typical alerts associated with failed login attempts (Figure 5).
In this type of attack, instead of seeing the typical An account failed to log on events in the Security event logs, you will observe Kerberos Pre-Authentication failed events. These events include the hex value 0x18, which means that an incorrect password was entered (Figure 6).
Password spraying using randomized delays intervals
Another way to make password spraying detection more difficult is by disrupting the predictable patterns for which security systems often monitor (Figure 7). This randomness makes the attack blend in with normal traffic, making attack detection and response more challenging for systems and security teams.
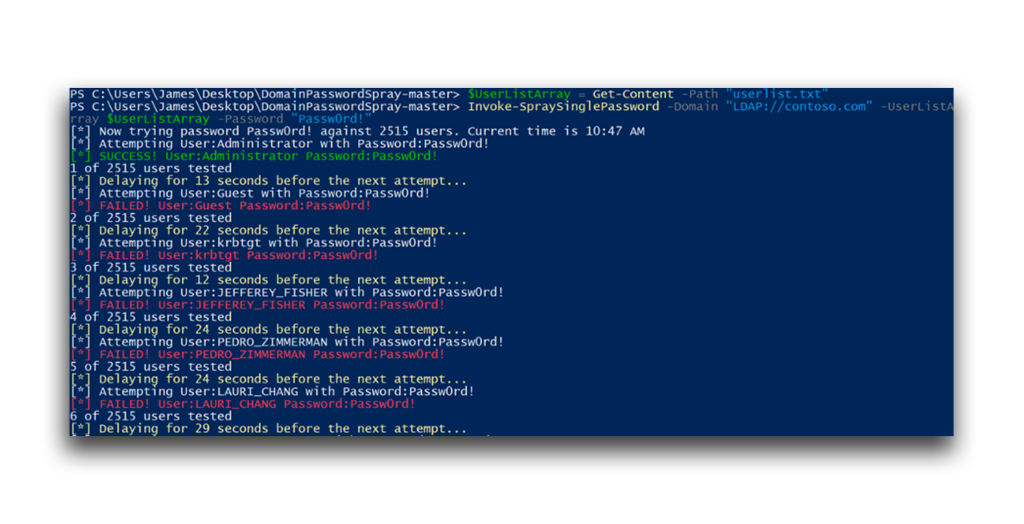
A password spraying attack with randomized delays still generates log events. However, the irregular timing between attempts can make password spraying detection more difficult. Instead of a consistent pattern, the logs show login attempts spread out unpredictably, making the attack less conspicuous (Figure 8).
The same concept can be applied by randomizing delay intervals during a password spraying attack that uses Kerberos pre-authentication. Because 4771 events are not typically closely monitored, introducing randomized delays makes detection even more difficult than previously discussed (Figure 9).
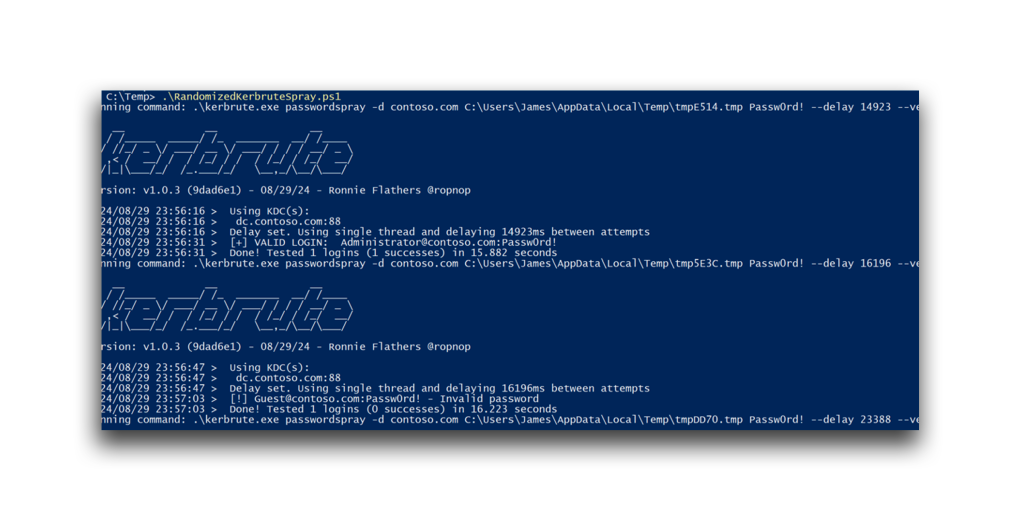
As in the previous example, randomization of the delay intervals between each login attempt can make this activity look like normal behavior in the logs (Figure 10).
Detecting password spraying attacks with Lightning Identity Runtime Protection
Identity Runtime Protection (IRP), a feature of the Semperis Lighting Platform, uses various attack-pattern indicators and anomaly detection to monitor for and detect identity-based attacks. Lightning IRP typically needs 7 to 10 days to learn the patterns of an environment through behavior analysis.
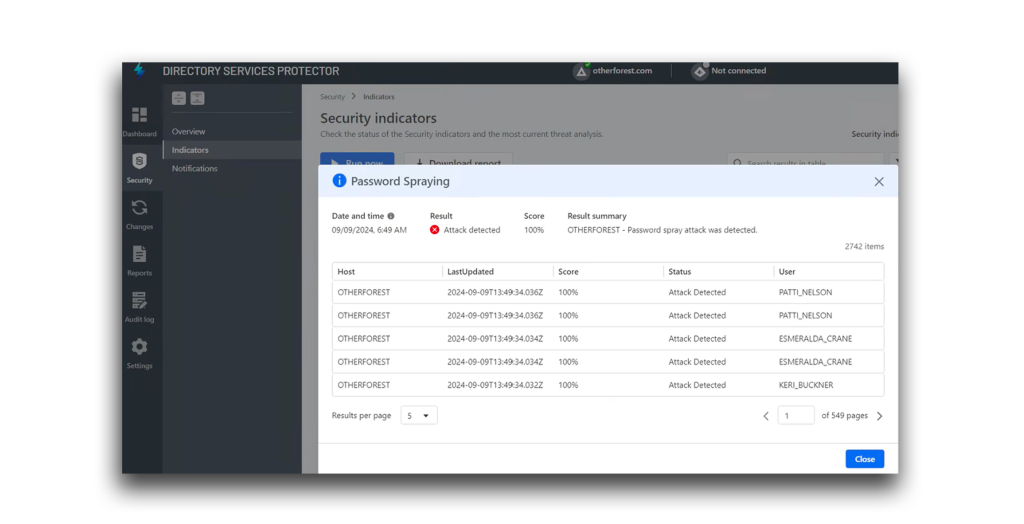
Figure 11 shows Lightning IRP successfully identifying two password spraying attacks. Based on these alerts, you can determine which accounts were targeted and the corresponding detection scores.
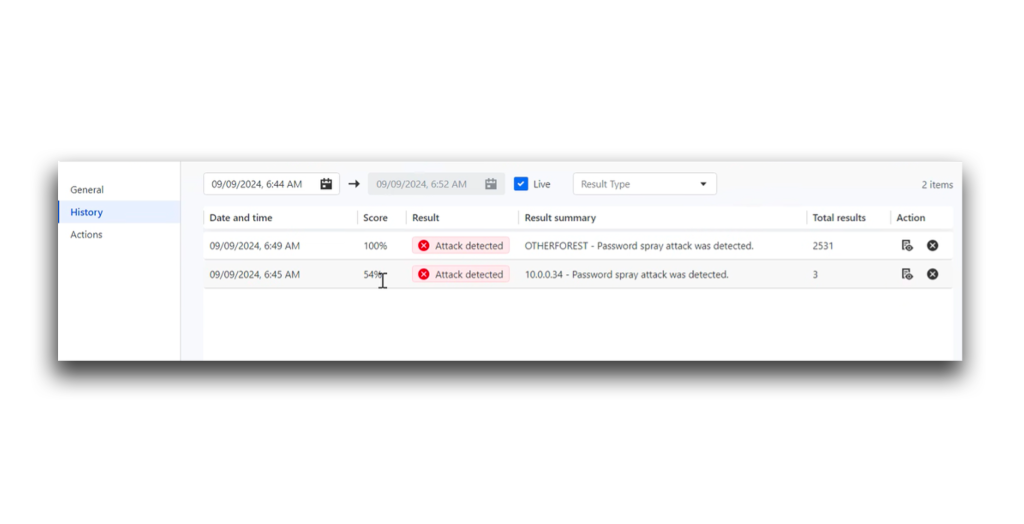
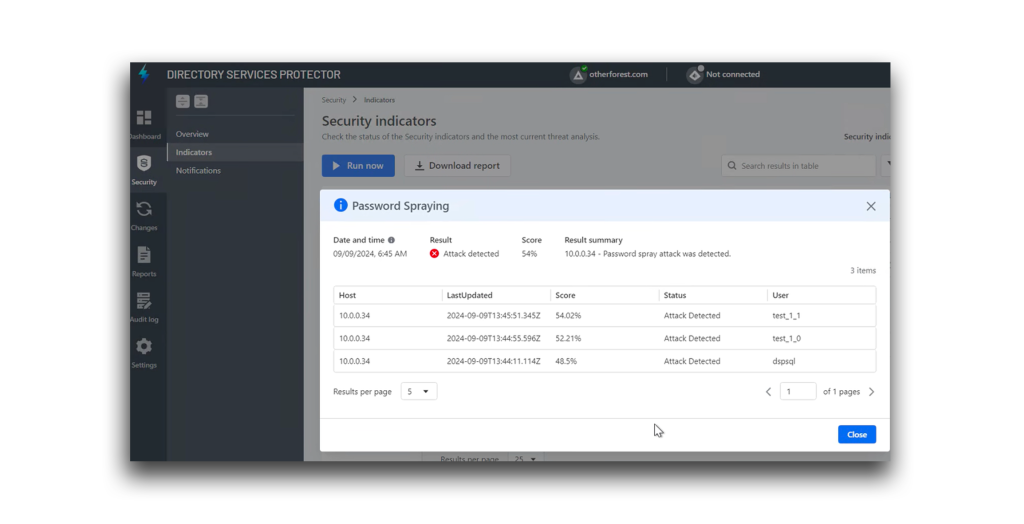
Figure 12 shows Lightning IRP password spraying detection of an attack that randomized the delay intervals for each password spraying attempt via Kerberos pre-authentication. The detection score is low in this case because the attack was designed for greater stealth. However, Lighting IRP was able to detect the behavior even though the traffic was intended to look typical and not raise alarms.
Performing a password spraying attack without randomizing delay intervals typically results in a higher detection score, as shown in Figure 13. This method is more likely to be flagged with a higher detection score (100% in this example) because of its predictable and noisy nature, which makes password spraying detection and categorization easier.
Additional recommendations for password spraying detection
To reduce the risk of successful password spraying attacks, it is important to enforce strong password policies, including implementing account lockout mechanisms (either temporary or permanent) after several consecutive failed login attempts. Organizations should ensure that such password policies are enforced through a default domain policy or fine-grained password policies in Active Directory.
Organizations that use Entra ID P1 or that have the appropriate Enterprise Mobility + Security (EMS) or Microsoft 365 licensing can achieve an additional layer of protection by deploying Entra Password Protection or a similar solution for Active Directory. This tool proactively prevents users from creating or using passwords that are easily guessable or that have been compromised in previous breaches. By integrating this solution, organizations can improve the likelihood of successful password spraying detection.
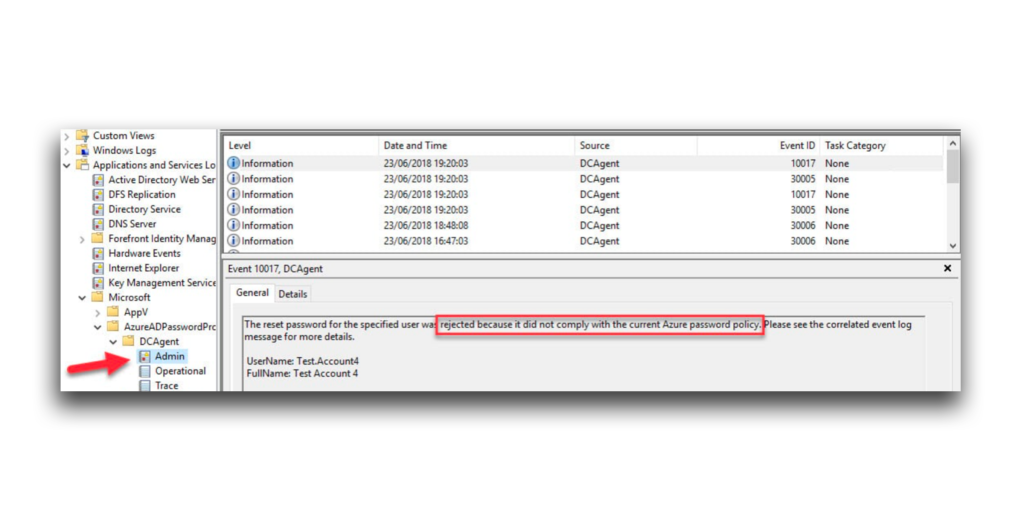
Figure 14 shows is an example in which Entra ID Password Protection has prevented a user from setting a password that does not comply with the organization’s current password policy.
Additional password spraying detection resources
- How to Defend Against Password-Spraying Attacks
- Detect and Prevent Identity-Based Attacks
- Windows Password Policy (Microsoft Learn)
- Microsoft Entra Password Protection for AD Domain Services (Microsoft Learn)
- ropnop/kerbrute: A tool to perform Kerberos pre-auth bruteforcing (github.com)
- dafthack/DomainPasswordSpray: A tool written in PowerShell to perform a password spraying attack against domain users (github.com) Note: By default, this tool automatically generates the userlist from the domain. Be very careful not to lockout accounts!
- Implementing Modern Security Tools (MSEndpointMgr)
