Password spraying is a top cyber threat, named in the recent report from the cybersecurity agencies in the Five Eyes alliance. What is password spraying, how have cyberattackers used it in the past, and how can you detect and defend your hybrid Active Directory environment against password spraying attacks?
What is password spraying?
Password spraying is an attack in which attackers try commonly used or weak passwords on many accounts, targeting systems like VPNs, Citrix gateways, and Entra ID tenants. Unlike brute-force attacks that focus on a single account, password spraying spreads out the attempts to reduce the chance of triggering account lockouts. In a password spraying attack, attackers often target Active Directory accounts in internal networks to gain access and escalate privileges (Figure 1).
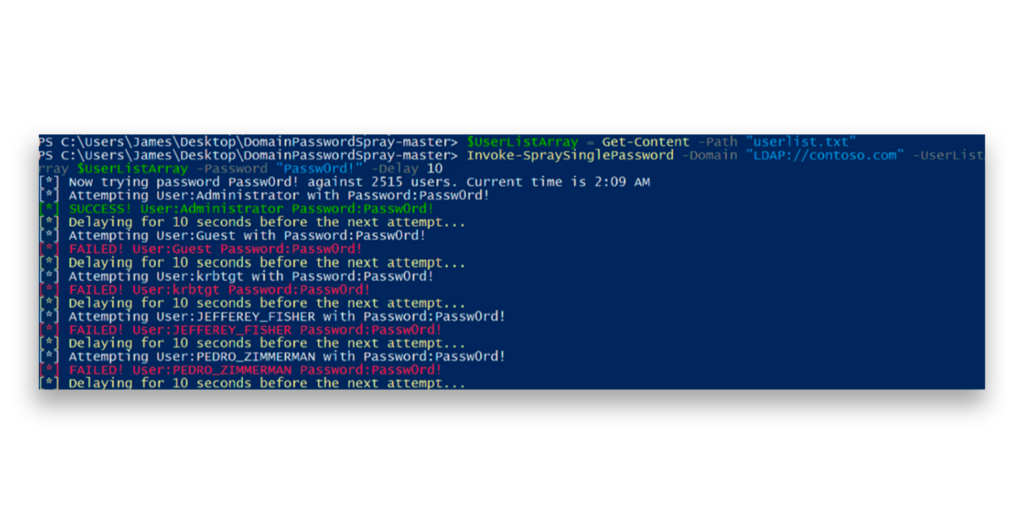
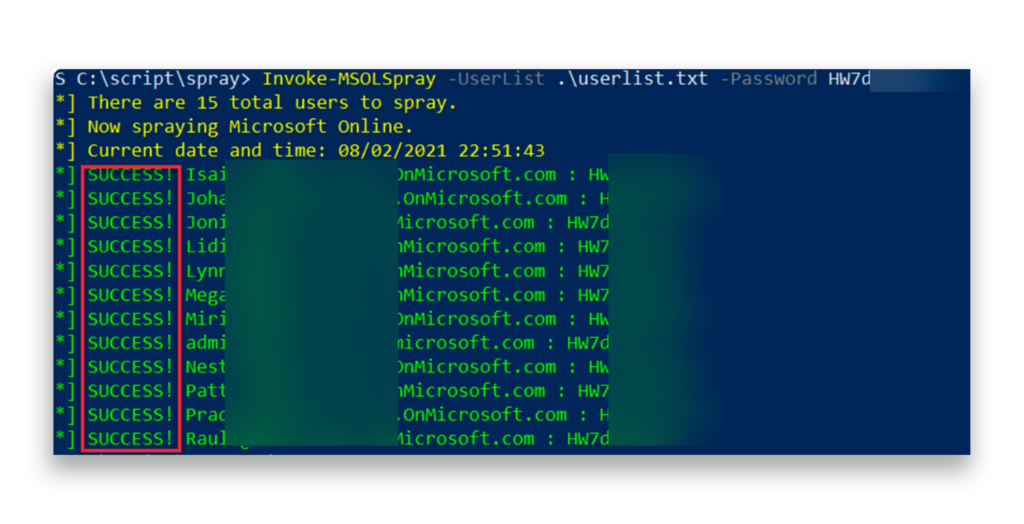
Entra ID is another target. Here’s an example of a password spray attack targeting an Entra ID tenant (Figure 2).
How can you defend against password spraying?
Defending your organization against password spraying is an important step in strengthening your Active Directory security stance. Several actions can help.
- Implement Multifactor Authentication (MFA) for all internet-facing login portals.
- Enforce strong password policies in Active Directory to ensure that users create robust passwords.
- If possible, consider transitioning to passwordless authentication, though doing so might not be feasible for every organization.
- Implement a password protection solution (e.g., Entra ID Password Protection) to block weak or compromised passwords from being used across your systems.
- Decommission any unused non-production Entra ID tenants, which can contain sensitive data.
- Decommission internet-facing systems that are no longer in use to reduce potential attack surfaces.
How can you detect password spraying?
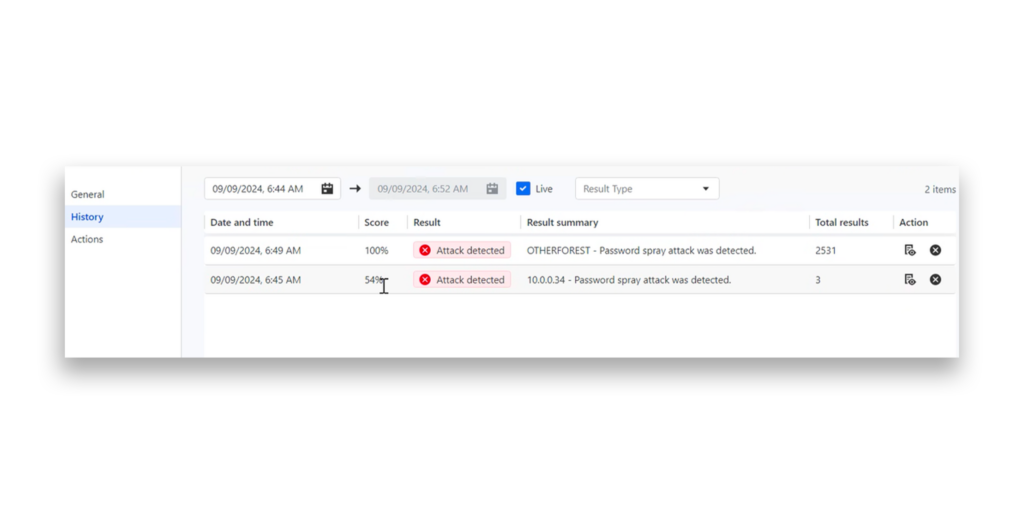
Semperis Directory Services Protector (DSP) can help detect password spraying attacks within Active Directory environments (Figure 3).
Internet-facing systems like Citrix, RDP Gateways, and VPNs are often tied to Active Directory. These systems can be used as entry points to access AD. Centralizing logs for these systems into a SIEM solution is a good idea. Doing so makes it easier to spot suspicious logon attempts, like password spraying, early on. However, be aware that many cyberattacks are adept at getting around SIEM detection.
Threat actor profiles
The following threat actors have been known to use password spraying attacks in the wild.
- APT28 aka IRON TWILIGHT, SNAKEMACKEREL, Swallowtail, Group 74, Sednit, Sofacy, Pawn Storm, Fancy Bear, STRONTIUM, Tsar Team, Threat Group-4127, TG-4127, Forest Blizzard, FROZENLAKE (MITRE ATT&CK Group G0007)1
- APT29 aka IRON RITUAL, IRON HEMLOCK, NobleBaron, Dark Halo, StellarParticle, NOBELIUM, UNC2452, YTTRIUM, The Dukes, Cozy Bear, CozyDuke, SolarStorm, Blue Kitsune, UNC3524, Midnight Blizzard (MITRE ATT&CK Group G0016)2
- APT33 aka HOLMIUM, Elfin, Peach Sandstorm (MITRE ATT&CK Group G0064)3
- Play (MITRE ATT&CK Group G1040)4
Password spraying tools
The following tools, available on github.com, can be used to perform a password spray attack.
- dafthack/DomainPasswordSpray
- dafthack/MSOLSpray
- iomoath/SharpSpray
Threat overview
ATT&CK Tactic: Credential Access
On January 25, 2024, Microsoft reported that the Midnight Blizzard (aka APT29) group used password spraying to compromise a non-production test tenant without MFA. The attackers evaded detection by using low-frequency password attempts and residential proxy networks. After gaining access, they compromised a legacy test OAuth application with elevated privileges, which had access to Microsoft’s corporate environment. This enabled the attackers to deploy a malicious OAuth app, giving them long-term access to sensitive systems and data.5
On January 24, 2024, Talos Intelligence reported that the Play ransomware group used password spraying with the tool SharpSpray to gain access by trying weak passwords across multiple accounts within Active Directory. Once inside, the attackers escalated privileges and disabled security tools using methods like PsExec, bypassing MFA through social engineering help desks to register new devices. The attackers then deployed ransomware to encrypt targeted systems.6
On September 14, 2023, Microsoft reported that Peach Sandstorm used password spraying to target Entra ID tenants across industries like defense and pharmaceuticals. By attempting weak passwords across multiple accounts, the attackers aimed to gain access to sensitive environments. Once successful, they performed internal reconnaissance using tools like AzureHound and Roadtools to map the network and maintain persistence.7
On September 10, 2020, Microsoft reported that the STRONTIUM threat group used password spraying as a key tactic in its credential harvesting campaigns. The attackers targeted Office 365 accounts across various industries, including those linked to political elections. Using a large pool of IP addresses, including Tor anonymizers, STRONTIUM carried out low-frequency authentication attempts across thousands of accounts to avoid detection and account lockouts.8
In April 2019, Citrix provided an update about a breach in its internal network, where attackers likely accessed and stole business documents over several months. The attack was thought to involve techniques like password spraying. Citrix worked with the FBI and cybersecurity experts to investigate the incident and took steps to improve its security.9
Semperis snapshot
Password spraying attacks are a common method used by cyberattackers to exploit weak passwords without triggering account lockouts. By trying common passwords across multiple accounts, attackers avoid detection and can compromise systems like VPNs, Entra ID tenants, or Active Directory. These attacks can lead to unauthorized access to sensitive environments and data. To defend against password spray attacks, enforce strong password policies, enable MFA, and use effective tools to monitor for unusual login activity or behavior.
Additional resources
- How to Defend Against a Password Spraying Attack
- Password Spraying Detection in Active Directory
- Introducing Lightning Identity Runtime Protection
Endnotes
- https://attack.mitre.org/groups/G0007/
- https://attack.mitre.org/groups/G0016/
- https://attack.mitre.org/groups/G0064/
- https://attack.mitre.org/groups/G1040/
- https://www.microsoft.com/en-us/security/blog/2024/01/25/midnight-blizzard-guidance-for-responders-on-nation-state-attack/
- https://blog.talosintelligence.com/talos-ir-quarterly-report-q4-2023/
- https://www.microsoft.com/en-us/security/blog/2023/09/14/peach-sandstorm-password-spray-campaigns-enable-intelligence-collection-at-high-value-targets/
- https://www.microsoft.com/en-us/security/blog/2020/09/10/strontium-detecting-new-patters-credential-harvesting/
- https://citrixblogs.wpengine.com/2019/04/04/citrix-provides-update-on-unauthorized-internal-network-access/
