Forest Druid is a free cyber attack path discovery tool for hybrid identity environments, such as Active Directory and Entra ID. Unlike traditional tools that map attack paths from the external perimeter inwards, Forest Druid focuses on protecting the most critical assets first.
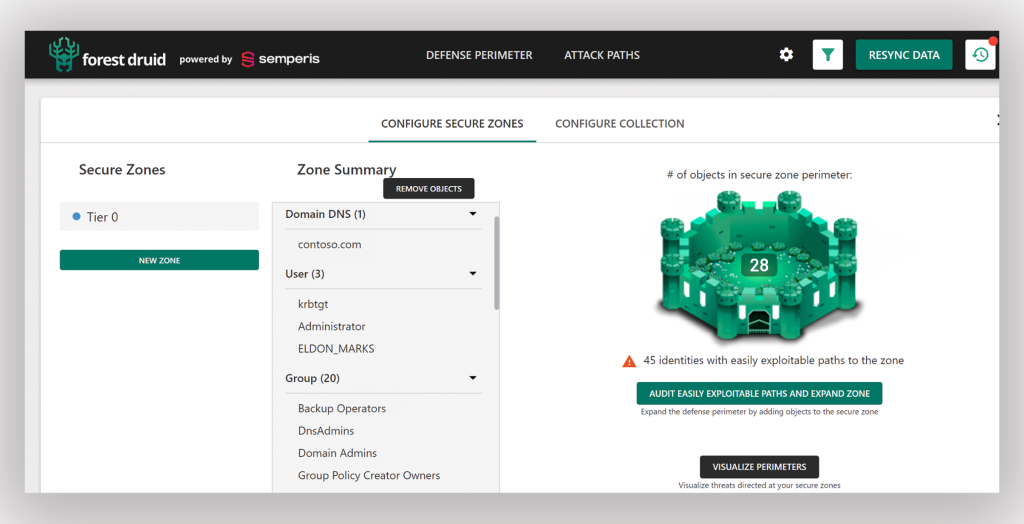
This method prioritizes identifying and securing Tier 0 assets, the most privileged and sensitive parts of the network (Figure 1), from cyber threat. Such assets include administrative accounts and servers with control over identity management systems like Active Directory. By securing these Tier 0 assets, organizations can better protect their overall IT infrastructure.
The challenge of compromised identities
Incident response can be overwhelming, especially when dealing with a difficult security incident such as compromised identities within an Active Directory environment. During an ongoing incident response, such as a ransomware security incident, identifying the risk posed by newly compromised identities and understanding how attackers might escalate privileges to access Tier 0 assets is critical.
Attackers often target these high-privilege accounts to gain control over the network so that they can spread their ransomware. Therefore, it is essential to prioritize securing these assets to mitigate the impact of such an attack.
The visualized view provided by Forest Druid enhances your cyber incident response planning, making it easier to understand the potential impact of a compromised account, offering better insights into the associated risks.
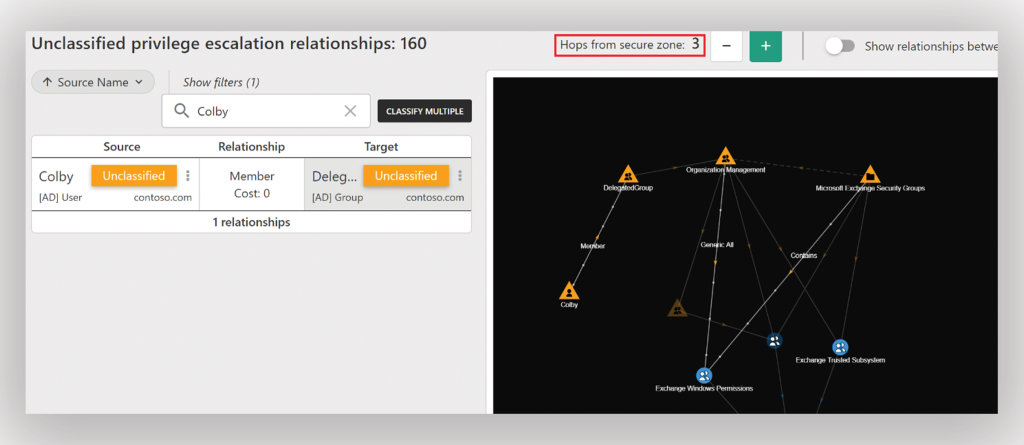
In the following example, you can see that it would take three hops for the specified identity to elevate its privileges to a Tier 0 asset (Figure 2). By identifying the number of hops a compromised identity would need to reach your Tier 0 assets, you can better assess the exposure level of those assets. This helps you prioritize the critical attack paths that need remediation and understand the effort required for an attacker to reach Tier 0.
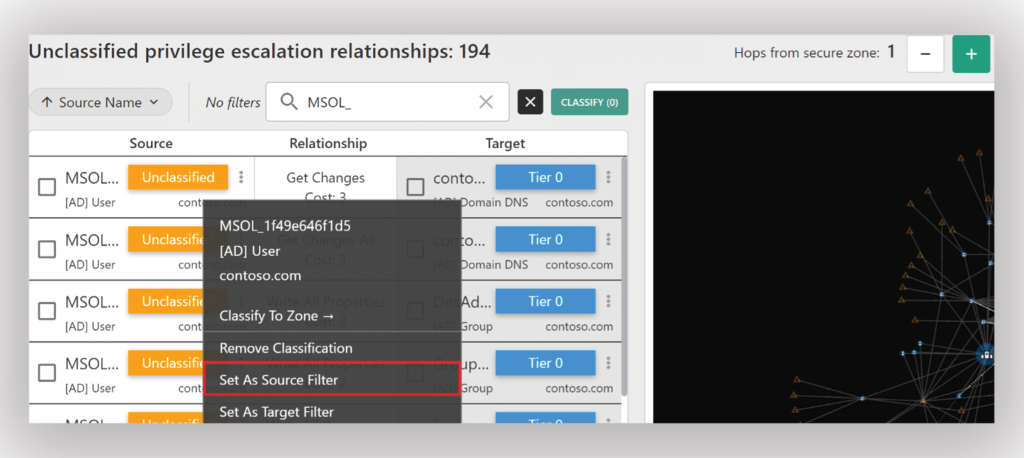
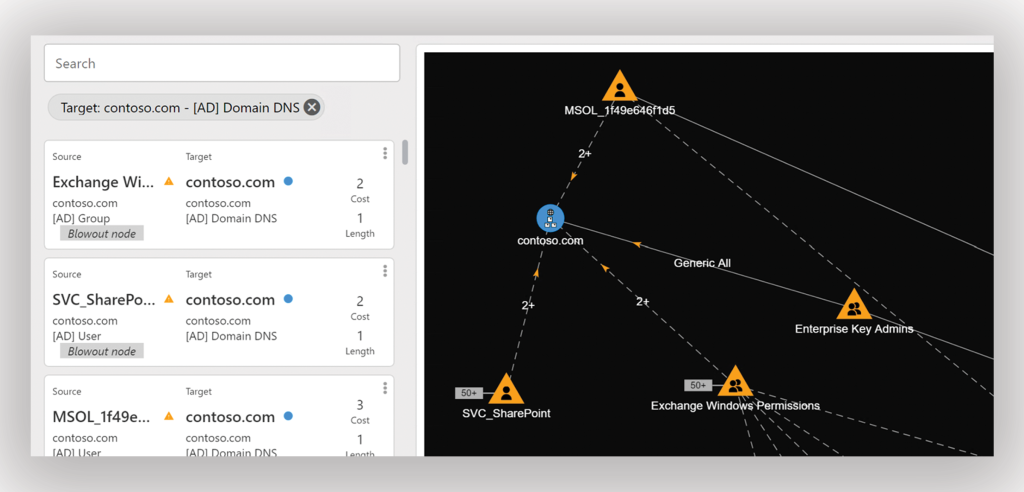
Suppose you observe another compromised identity. You can set this account as the source filter to map out all the direct attack paths it has to Tier 0 (Figure 3).
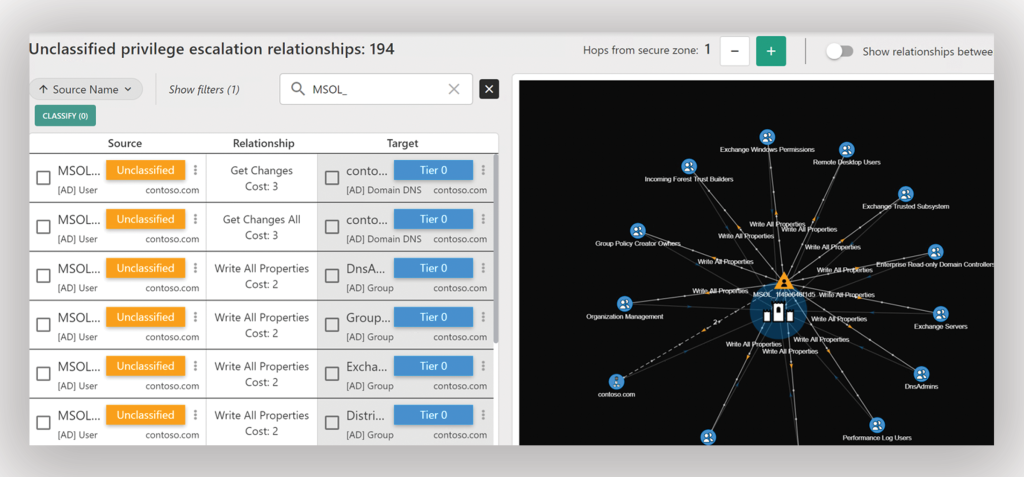
Once you set an account as the source filter, Forest Druid begins visually mapping out all the attack paths that lead from that account to Tier 0 (Figure 4).
Incident response alongside containment and recovery
With the rise of ransomware attacks, effective incident response roles have expanded to include containment and recovery. This change highlights the need to manage both investigations and containment efforts at the same time. Containment focuses on stopping the spread of an attack, minimizing damage, reducing the attack surface of Tier 0 assets, and hardening critical systems like Active Directory. Recovery involves restoring systems and data to normal operation—especially critical identity systems like Active Directory—and ensuring that they are secure and functional.
Incident responders can use Forest Druid as part of their toolkit. Although not a solution for everything, Forest Druid provides a visualized view of the network and the potential impact of compromised accounts, improving your incident response capability. The tool maps out connections and attack paths, which can help incident responders quickly identify and remediate paths to the most critical assets (e.g., Tier 0) and harden Active Directory (Figure 5). The tool adds value to both containment and recovery efforts for the incident responder.
How to collect data with Forest Druid
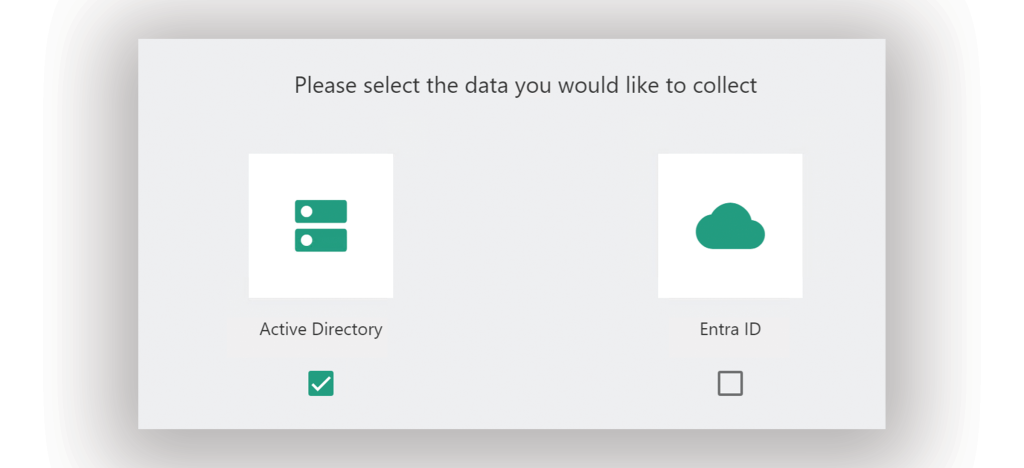
When you run Forest Druid for the first time, the tool prompts you to select the type of data to collect: either from Active Directory or from Entra ID. In this example, I’ve selected Active Directory.
Forest Druid then begins running LDAP queries in the background, gathering all the information within the environment (Figure 6). This point-in-time data collection enables Forest Druid to start visualizing attack paths.
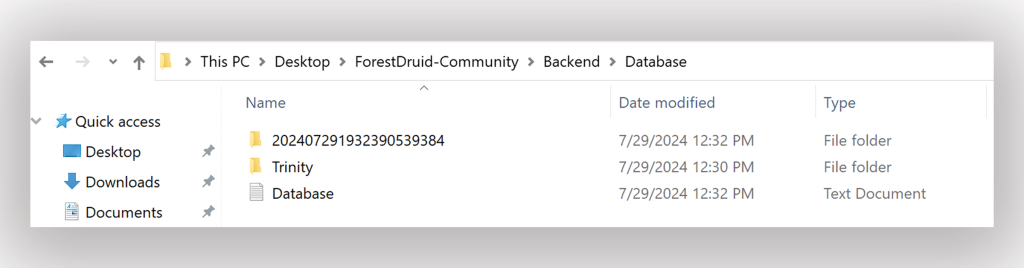
All the collected data is stored in a subfolder called Database within the Backend folder of Forest Druid (Figure 7). The data collected in the Database folder can be compressed into a ZIP file and shared in a secure manner with the incident response team for analysis.
To analyze the data offline, the team needs only to copy the files into its own Database folder within the Forest Druid directory. This action provides the same view of the Active Directory forest as when Forest Druid was initially run.
Download Forest Druid and start mapping attack paths to your Tier 0 assets
More Forest Druid attack path analysis resources
- Watch the Forest Druid demo video
- Read the Forest Druid FAQs
- Watch as Ran Harel demonstrates Forest Druid at Black Hat USA 2022
- Watch video interview about Forest Druid with Ran Harel and David Raviv of NY Information Security Meetup
- Visit Forest Druid
