Cybersecurity agencies from the Five Eyes alliance, including CISA and the NSA, have urged organizations to strengthen security around Microsoft Active Directory (AD), a prime target for cyberattackers. The alliance’s recent report highlights more than a dozen tactics that threat actors use to exploit AD. Among these common techniques is the exploitation of unconstrained delegation.
What is unconstrained delegation?
Unconstrained delegation enables a service or computer to impersonate a user across the entire domain, once the user authenticates to it (Figure 1). When a user requests access to a service (e.g., a file share through CIFS), a Kerberos Ticket Granting Ticket (TGT) is forwarded and stored in the memory of that service. This ticket is then attached in memory, enabling the service to act on behalf of the user and access other network resources.
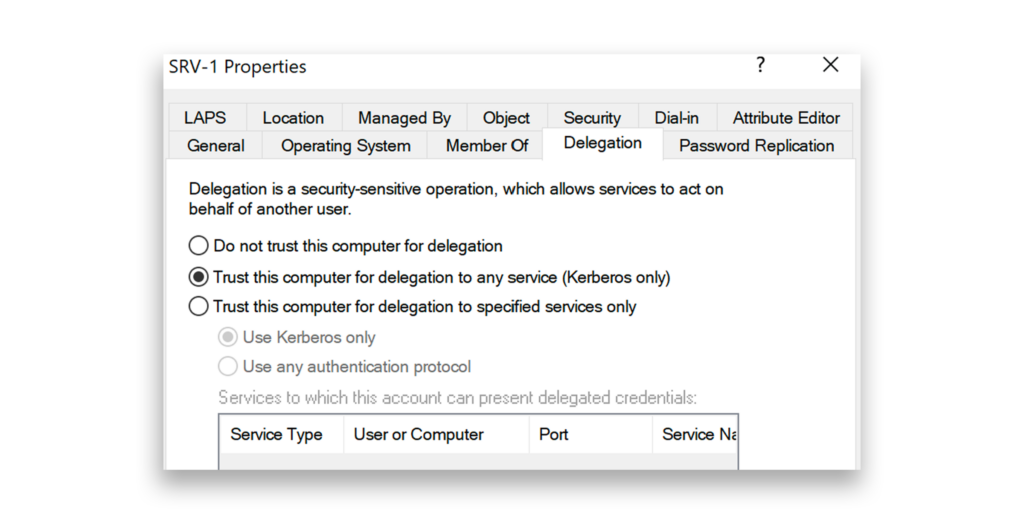
From an attacker’s perspective, the first step is to run an LDAP query to locate servers that have unconstrained delegation enabled (Figure 2). Domain controllers (DCs) can be ignored because delegation is unconstrained by default on DCs. However, regular servers with this setting are also valuable targets. After compromising such servers, the attacker can use them to monitor for incoming TGTs when users request Kerberos Service Tickets (STs), enabling the attacker to impersonate those users and access other resources across the network.

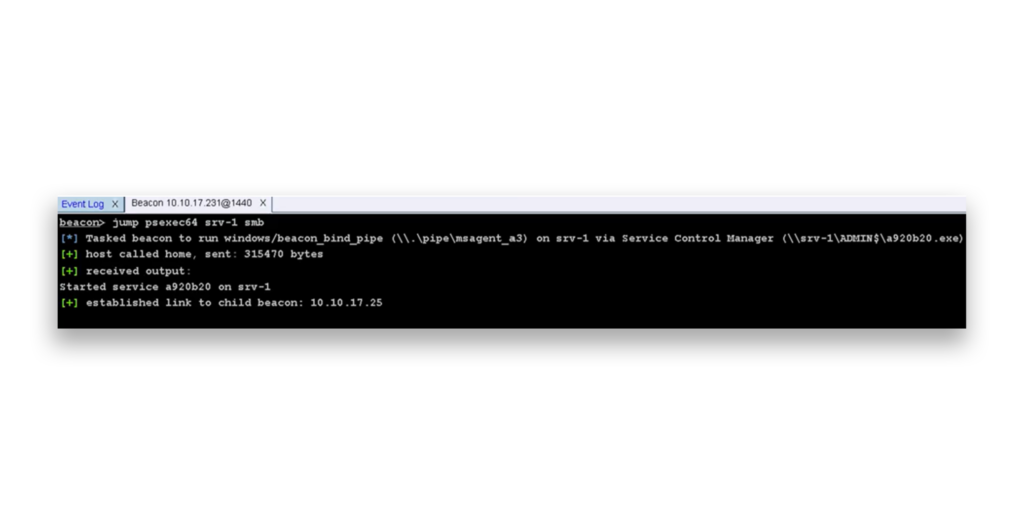
After identifying servers with unconstrained delegation and verifying local admin access, the attacker can use PSExec to move laterally over SMB to those machines (Figure 3).
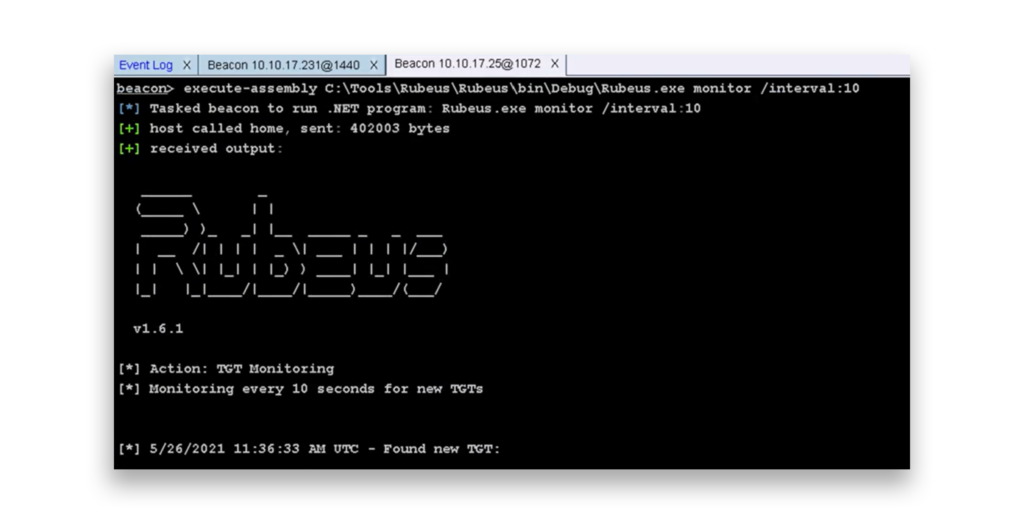
From there, the attacker can begin using Rubeus to monitor for incoming Kerberos TGTs (Figure 4). The attacker can then intercept and potentially exploit these tickets as other users request access to services across the network.
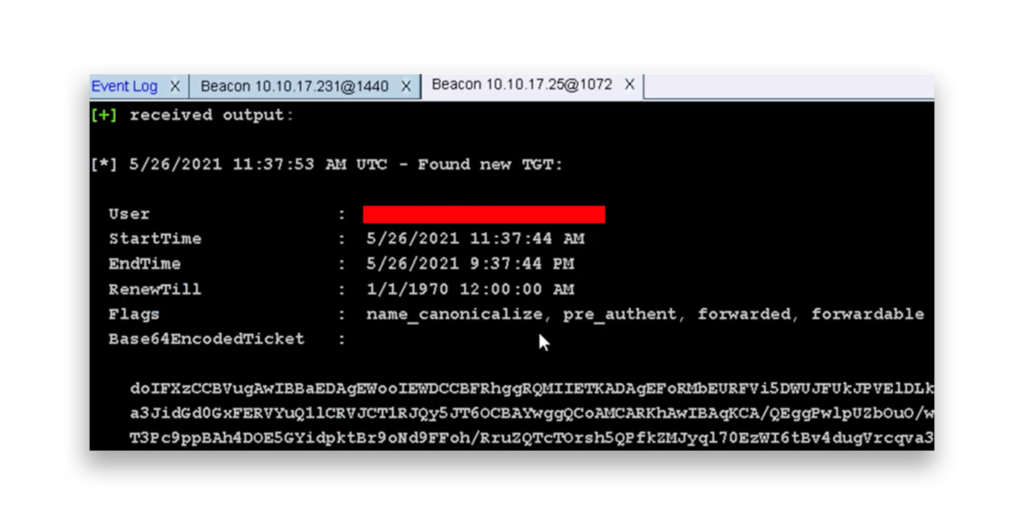
In this example, the attacker was able to capture a Kerberos TGT for a Domain Admin (Figure 5). The admin account requested an ST for the CIFS service on a server with unconstrained delegation enabled, causing the TGT to be stored in the server’s memory.
How can you defend against unconstrained delegation exploitation?
Ideally, you should avoid using unconstrained delegation altogether. If that isn’t an option, the next best approach is to treat any server with unconstrained delegation enabled as a Tier 0 system.
How can you detect unconstrained delegation?
Defenders can use the free Purple Knight tool to identify both user and computer accounts that are configured for unconstrained delegation (Figure 6). A strong countermeasure is to enable the Account is sensitive and cannot be delegated option for your Tier 0 and other highly privileged accounts. Doing so can help to prevent those accounts from being misused through delegation attacks.
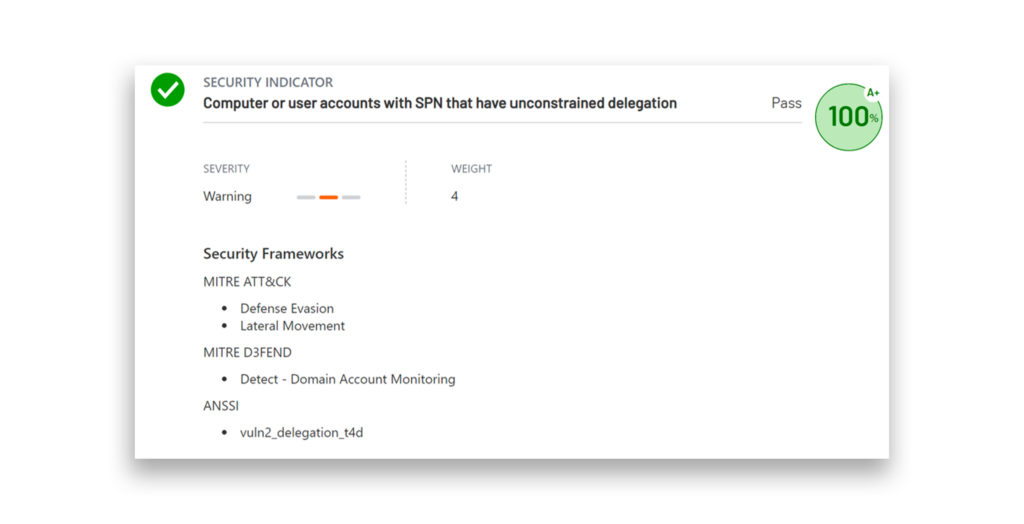
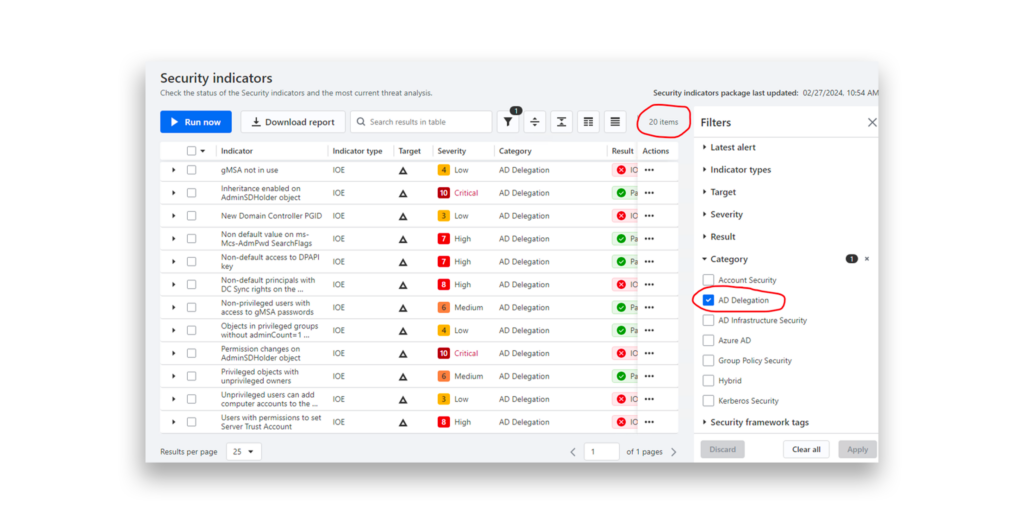
Semperis Directory Services Protector (DSP) includes a dedicated AD Delegation category, which continuously monitors a variety of insecure or risky Active Directory delegation settings (Figure 7). At the time of writing, DSP tracks 20 delegation configurations for potential vulnerabilities.
Unconstrained delegation tools
The GhostPack/Rubeus tool, which is available on github.com, can be used to exploit servers with unconstrained delegation enabled.
Red Team training
Red Teams often exploit unconstrained delegation, which is frequently covered in the following Red Team training courses:
- Outflank’s Defend Against Modern Targeted Attacks
- Zero Point Security’s Red Team Ops
- Altered Security’s Attacking and Defending Active Directory Lab
Semperis snapshot
Unconstrained delegation enables an attacker to impersonate users across an entire domain and can be risky if not managed properly. When a user requests a Kerberos Service Ticket, a Kerberos TGT is stored in the server’s memory and is a prime target if that server is compromised. Attackers can abuse TGTs to impersonate users and access other resources in the network.
