Update July 6, 2021: Microsoft has released a patch for CVE 2021-34527, available here.
Another week, another critical vulnerability. The latest critical security flaw is dubbed “PrintNightmare,” a reference to two vulnerabilities in the Windows Print Spooler service—CVE 2021-1675 and CVE 2021-34527, published between June and July 2021.
CVE 2021-1675 is a patched vulnerability that enables remote code execution and privilege escalation on servers and computers running the Print Spooler. CVE 2021-34527 also allows remote code execution and privilege escalation on the same service through somewhat different means. (Update on July 6, 2021: Microsoft released a patch for CVE-2021-34527.) At this moment, the exact relationship is unclear between the two vulnerabilities and whether the patch was incomplete or if another attack method was discovered.
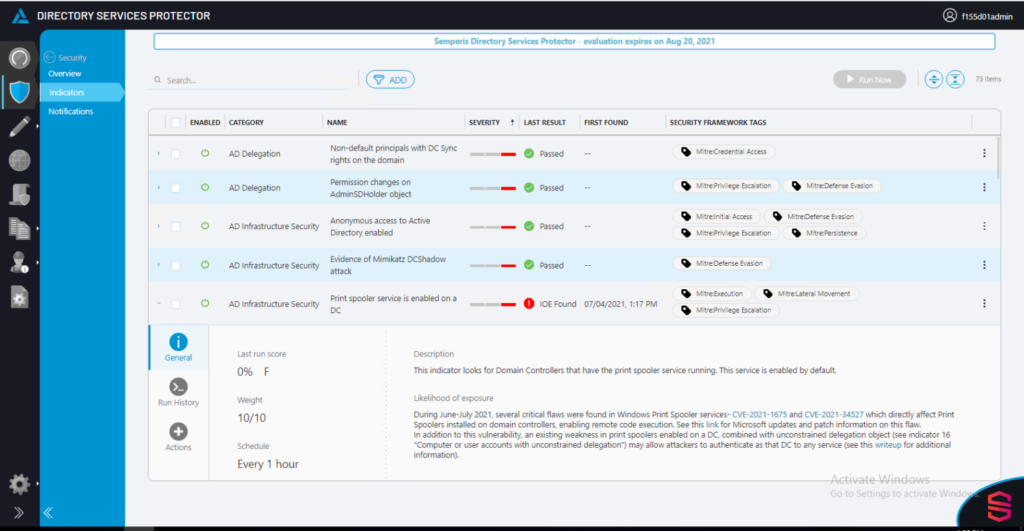
Before I go any further, let’s start with the bottom line—if you haven’t already done so, disable any Windows Print Spooler service running on a domain controller. (Semperis’ Directory Services Protector (DSP) includes indicators that continuously scan for exposures and signs of compromise, including enabled Print Spoolers on domain controllers.)
Print Spooler background
Print Spooler is a Windows service enabled by default in all Windows clients and servers. The service manages print jobs by loading printer drivers, receiving files to be printed, queuing them, scheduling, and so on.
The Print Spooler service is required when a computer is physically connected to a printer that provides printing services to additional computers on the network. It’s possible to use third-party drivers and software (like those offered by the printer manufacturers), but many organizations rely on the default Print Spooler service.
On domain controllers, Print Spoolers are mainly used for printer pruning—removing printers that have been published to Active Directory and that are no longer available on the network. Printer pruning is especially important in larger environments with many printers as it “cleans up” the printer list available to domain users. For this approach to work, though, an appropriate Group Policy must be in place.
From a security perspective, the Windows Print Spooler, and printers in general, have been a juicy target for exploitation by attackers for many years. The 2010 Stuxnet worm used against Iranian nuclear facilities exploited a vulnerability in the service to escalate privileges and propagate malware across the network. The same Print Spooler vulnerability re-surfaced in 2020 when researchers uncovered new ways to exploit it. Combined with the fact that printers are notoriously hackable, maybe it’s time we truly go paperless?
PrintNightmare Zero-Day bug
The June 2021 iteration of the Print Spooler vulnerability began with Microsoft’s June 2021 Patch Tuesday that included a patch for CVE 2021-1675, which Microsoft considered a privilege escalation vulnerability with exploitation “less likely” at the time—ranking a 6.8 (Medium Risk) CVSS score. Microsoft updated this CVE on June 21 to include Remote Code Execution and upgraded the CVSS score to 7.8 (High Risk). A few days later, PoC exploit code appeared on GitHub. The code was quickly taken offline but was already forked several times.
On June 30, it became apparent that the patch was not sufficient, and fully patched systems were still vulnerable to remote code execution and privilege escalation to SYSTEM. The original exploit code was modified, making the patch only somewhat effective.
On July 1, Microsoft created a new vulnerability, CVE 2021-34527. (July 6, 2021 – Microsoft released a patch.)
Print Spooler vulnerability breakdown
The Print Spooler remote code execution vulnerability takes advantage of the RpcAddPrinterDriver function call in the Print Spooler service that allows clients to add arbitrary dll files as printer drivers and load them as SYSTEM (the spooler service context).
The function is designed to allow users to update printers remotely—for example, the IT person remotely installing your brand-new office printer. However, a logical flaw in how this works allows any user to inject their own unsigned dll into the process, bypassing authentication or validation of the file.
Mitigating PrintNightmare
Update July 7, 2021 – Microsoft released a patch for CVE 2021-34527. It is still recommended to disable the Print Spooler where they are not required. You can disable the Print Spooler service across all your DCs (or any machine, for that matter) by using either the Group Policy setting under Computer ConfigurationWindows SettingsSecurity SettingsSystem Services or, better yet, using GP Preferences under Computer ConfigurationPreferencesControl Panel SettingsServices. An additional, unofficial mitigation is to limit access to the driver folder where the service loads from. This would need to be done on every server and has not been fully tested to the best of my knowledge, so use at your own risk.
Protecting domain controllers
Domain controllers should never be used as print servers. The only legitimate reason that I know of to have Print Spooler running on a DC is for printer pruning mentioned above. In addition to the numerous vulnerabilities in Windows Print Spooler, an attack vector against this service known as “the printer bug” enables an attacker who can compromise a resource with Kerberos unconstrained delegation to also compromise the DC with SYSTEM privileges. A good explanation of this attack is here.
Continuously monitor for vulnerabilities like PrintNightmare
We’ve seen vulnerabilities in commonly deployed IT infrastructure on a weekly basis. The short cycle times from disclosure to weaponization necessitates a rapid mitigation approach that includes continuous monitoring of the environment combined with prioritization and actionable remediation information.
Semperis’ Directory Services Protector (DSP) product includes indicators that continuously scan for exposures and signs of compromise in hybrid identity environments (including detecting enabled Print Spoolers on domain controllers) and provides prioritization, metrics, and prescriptive guidance for remediation.
More resources
Want to learn more about how to address PrintNightmare, PetitPotam, and other new attacks that target Active Directory? Tune in to Stepping Up Your Active Directory Defenses: Lessons Learned from Recent Attacks Like PrintNightmare, a free on-demand web seminar hosted by Sean Deuby, Semperis Director of Services.
