Hybrid Identity Protection
Categories
- Active Directory Backup & Recovery (67)
- Active Directory Security (231)
- AD Security 101 (17)
- Community Tools (25)
- Directory Modernization (9)
- From the Front Lines (69)
- Hybrid Identity Protection (76)
- Identity Attack Catalog (32)
- Identity Threat Detection & Response (161)
- Our Mission: Be a Force for Good (14)
- Purple Knight (5)
- Semperis University (5)
- The CISO's Perspective (16)
- Threat Research (77)
- Uncategorized (3)
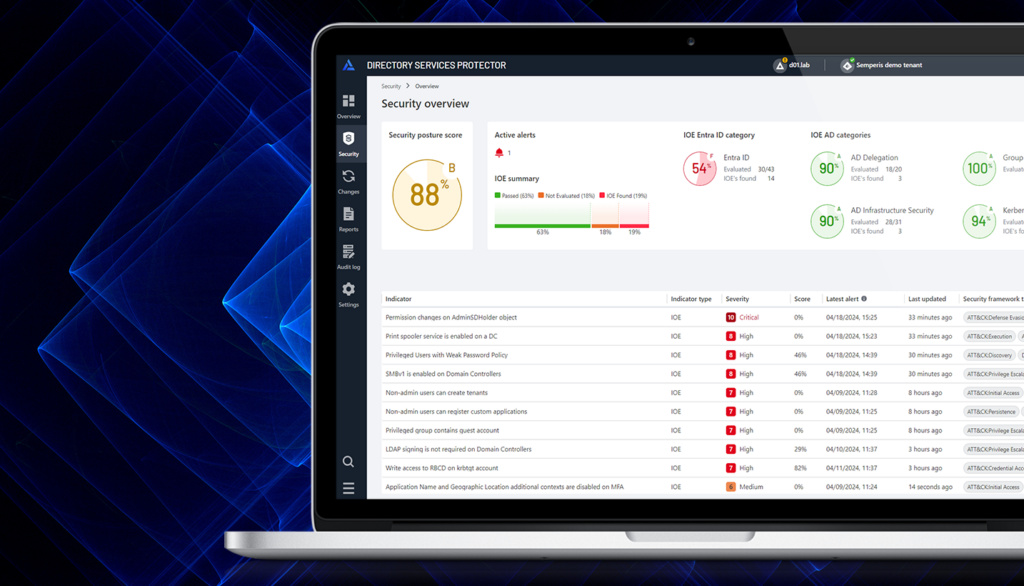
Semperis DSP: Enhance AD and Entra ID Protection from Cyber Threats
- Eitan Bloch | Semperis Product Manager
The SolarWinds breach in December 2020 signified a shift in the attack path for threat actors. Cyber threats increasingly target organizations' cloud environments, typically Microsoft Entra ID (formerly Azure AD), then move to on-premises Active Directory (AD)—or vice versa. This begs the question: How secure is your hybrid identity environment…

Meet Silver SAML: Golden SAML in the Cloud
- Tomer Nahum and Eric Woodruff
Key findings Golden SAML, an attack technique that exploits the SAML single sign-on protocol, was used as a post-breach exploit, compounding the devastating SolarWinds attack of 2020—one of the largest breaches of the 21st century. The supply chain SolarWinds attack affected thousands of organizations around the world, including the U.S.…
How to Defend Against an Overpass the Hash Attack
- Daniel Petri | Senior Training Manager
In the constantly evolving landscape of cyber threats, the Overpass the Hash attack is a potent vector. Leveraging the NTLM authentication protocol, this attack enables adversaries to bypass the need for plaintext passwords. Instead, an Overpass the Hash attack employs a user's hash to authenticate and potentially escalate privileges. As…
MFA for Active Directory: An Overview
- Sean Deuby | Principal Technologist, Americas
Modern information security is built on a layered defense. Each layer supports the others and presents additional obstacles to threat actors. From patch management to perimeter firewalls, each layer makes it more difficult for attackers to compromise your network. Multifactor authentication (MFA) is one of these layers. MFA has many…

NSA Top Ten Cybersecurity Misconfigurations: An Active Directory Perspective (Part 3)
- Daniel Petri | Senior Training Manager
Welcome to the final installment of this series discussing CISA and NSA top ten cybersecurity misconfigurations in the context of hybrid Active Directory environments. Active Directory is the identity system for most organizations: a critical part of your infrastructure, and a prime target for cyberattackers. This week, I’ll discuss the…

NSA Top Ten Cybersecurity Misconfigurations: An Active Directory Perspective (Part 2)
- Daniel Petri | Senior Training Manager
When it comes to cybersecurity—especially the security of critical identity infrastructure—the minimum expectation for every organization should be closing known vulnerabilities and configuration gaps. Welcome to the second of our three-part discussion of how the CISA and NSA top ten cybersecurity misconfigurations list applies to hybrid Active Directory environments and…
NSA Top Ten Cybersecurity Misconfigurations: An Active Directory Perspective
- Daniel Petri | Senior Training Manager
Late last year, the United States National Security Agency's (NSA) and Cybersecurity and Infrastructure Security Agency (CISA) released a list of the most common vulnerabilities in large computer networks. This list of CISA and NSA top ten cybersecurity misconfigurations reveals systemic weaknesses, particularly in (though not limited to) Microsoft Windows…

4 Reasons to Increase Recoverability of Entra ID Resources
- Tuna Gezer
By now it’s well known that cyberattackers consider Active Directory their favorite target. AD—the primary identity store for 90% of businesses worldwide—was built for efficient user authentication and access management, but many legacy on-premises AD environments have risky misconfigurations that have accumulated over time. By exploiting AD security gaps, attackers…



