Webinar

De la mesa a la realidad: Aumentar la ciberresiliencia mediante simulacros de respuesta a incidentes
- Semperis
- 16 de marzo de 2025
En el panorama actual de amenazas, la rapidez y eficacia de su respuesta a incidentes puede significar la diferencia entre un contratiempo menor y una brecha catastrófica. La cuestión no es si se producirá un ciberataque, sino cuándo, y la preparación sigue siendo su mejor línea de defensa. Los ejercicios de simulación no son sólo una práctica: son...

¿Por qué su AD es un blanco fácil para los piratas informáticos?
- Semperis
- 28 de febrero de 2025
Active Directory (AD) sigue siendo la piedra angular de muchas organizaciones, tanto en sus instalaciones como integrado con Microsoft Entra ID en la nube. Resulta alarmante que el 90% de los ciberataques tengan como objetivo AD, el sistema de identidad central de la mayoría de las empresas. Semperis proporciona una protección completa para AD y Entra ID en las instalaciones, ofreciendo una defensa continua contra las amenazas basadas en la identidad antes,...
Superar las vulnerabilidades con la gestión de la superficie de ataque
- Semperis
- 30 de diciembre de 2024
A medida que se amplía el panorama digital, gestionar y proteger la superficie de ataque de su organización nunca ha sido tan crucial. Únase a nosotros en un webcast sobre temas candentes en el que expertos del sector ofrecerán una previsión exhaustiva de las tendencias de la gestión de la superficie de ataque (ASM) y ofrecerán orientación estratégica para finales de 2024 y principios de 2025.....
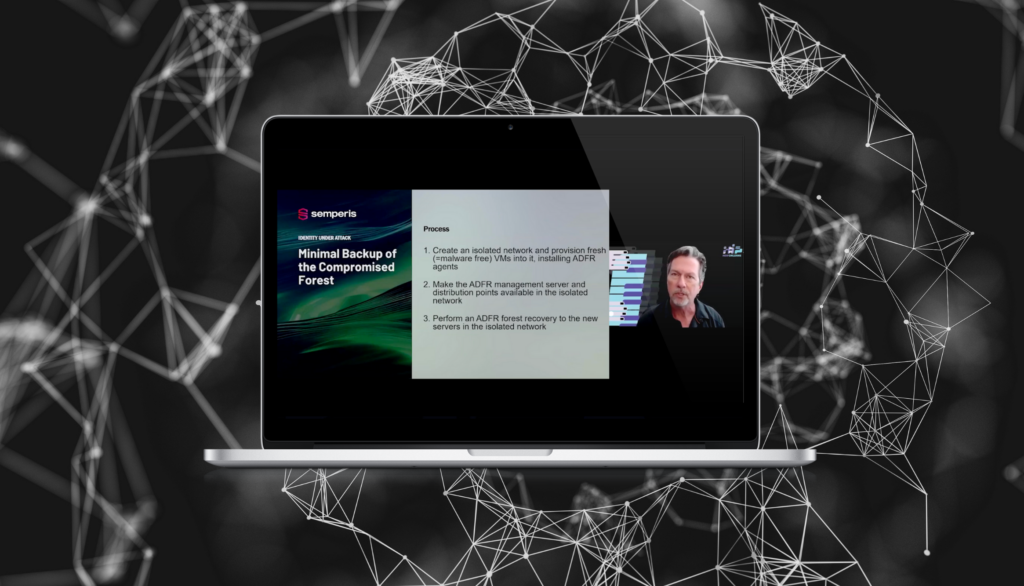
Cómo recuperar Active Directory cuando cada segundo cuenta
- Semperis
- 30 de diciembre de 2024
Microsoft Active Directory (AD) es un objetivo clave para los ciberatacantes. Cuando AD se cae, también lo hacen sus operaciones. Sin embargo, la mayoría de las organizaciones carecen de un plan de recuperación específico para AD o confían en la recuperación manual, que puede llevar días, si no semanas. Auditar la postura de seguridad de AD y mantener un sólido plan de respuesta a incidentes...
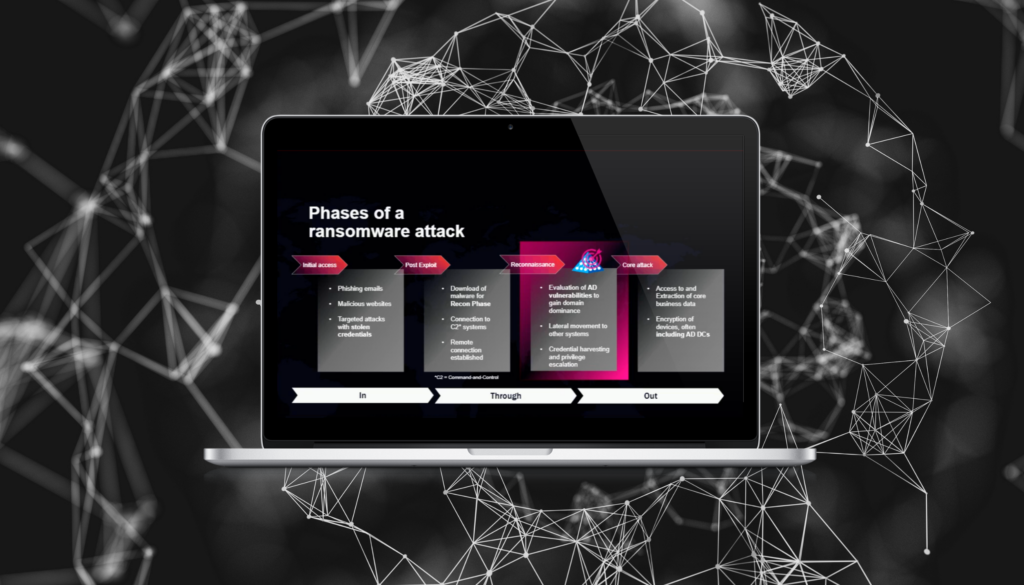
Cuando cada minuto cuenta Recuperación de AD durante un ataque
- Semperis
- 28 de diciembre de 2024
¿Qué hacer cuando se vulneran las protecciones de los puntos finales u otras protecciones iniciales? ¿Qué hace cuando los intrusos ya están en su red y posiblemente han puesto en peligro su bosque de Active Directory (AD)? Esta es la historia real de un ataque de ransomware y cómo se detuvo. Únase a Sean Deuby, de Semperis, 15 veces...
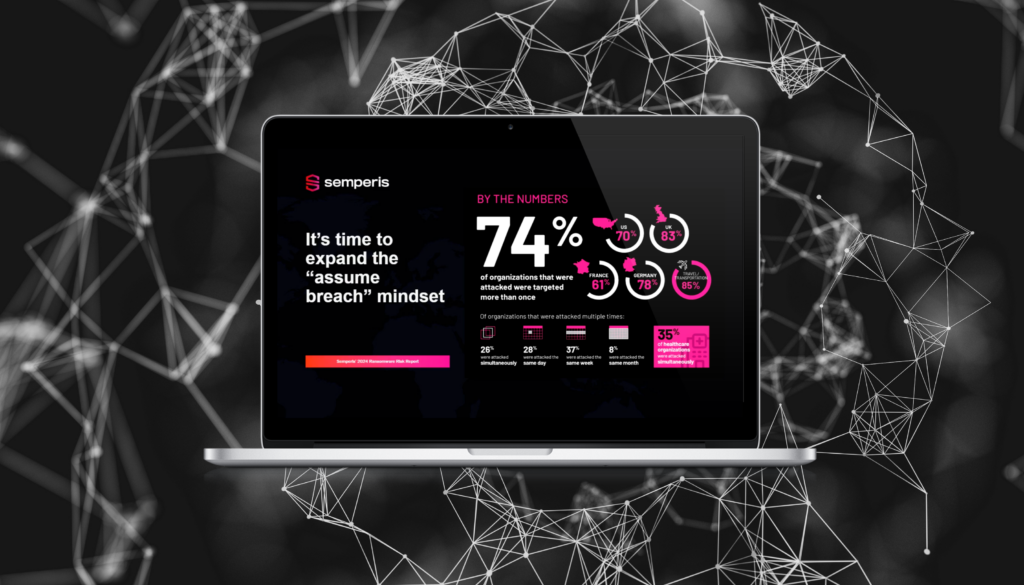
Continuidad de la actividad y recuperación del sistema de identidad
- Semperis
- 26 de noviembre de 2024
¿Su plan de recuperación de desastres está diseñado pensando en la continuidad del negocio? A menos que incluya procedimientos específicos para la recuperación segura de Active Directory (AD) y Entra ID, podría sufrir un duro golpe. La recuperación segura del sistema de identidad es un factor clave para determinar la rapidez con la que su organización puede volver...
Recuperación de las operaciones tras un ciberataque
- Semperis
- 25 de noviembre de 2024
Las organizaciones de infraestructuras críticas que gestionan sistemas de tecnología operativa (OT) o dispositivos del Internet de las Cosas (IoT) se enfrentan a varios retos para lograr una ciberseguridad eficaz, como una tecnología obsoleta, la complejidad de diversos entornos y una mayor superficie de ataque. Rob Ingenthron (arquitecto de soluciones sénior, Semperis) analiza los retos a los que se enfrentan las organizaciones de los sectores sanitario,...
Recuperación de Active Directory: La pieza que falta en su plan de resistencia operativa
- Semperis
- 17 de noviembre de 2024
El ransomware y la ciberdelincuencia se han convertido en amenazas de primer orden para las organizaciones de todos los sectores. Proteger los terminales, contratar un ciberseguro o incluso pagar un rescate: ninguna de estas opciones puede evitar un ataque que acabe con la empresa. Un paso que es clave para la resiliencia operativa y empresarial: Un plan de ciberseguridad dedicado y centrado en la identidad. Expertos del sector de Government Technology y Semperis...

Creación de una defensa de identidad por capas
- Semperis
- 11 de octubre de 2024
Los ciberatacantes son expertos en encontrar formas de atravesar sus defensas y entrar en sistemas de identidad como Active Directory. Desde allí, pueden moverse lateralmente, escalar privilegios, acceder a recursos sensibles e inyectar malware o ransomware. Implantar una defensa en capas que incluya la detección y respuesta ante amenazas de identidad (ITDR) es clave para proteger sus...
¡Que no cunda el pánico! Es sólo un incidente cibernético
- 26 de septiembre de 2024
¿Cómo son las horas inmediatamente posteriores a un supuesto incidente cibernético? En esta grabación, dejamos a un lado la jerga y nos sumergimos en la desordenada y caótica realidad de la respuesta a incidentes. Nuestra conversación 1:1 incluye historias de guerra, lecciones aprendidas y la sabiduría duramente adquirida al liderar organizaciones a través del fuego. Retrocedemos...



