Active Directory Security
Categories
- Active Directory Backup & Recovery (62)
- Active Directory Security (213)
- AD Security 101 (17)
- Community Tools (19)
- Directory Modernization (9)
- From the Front Lines (69)
- Hybrid Identity Protection (68)
- Identity Attack Catalog (27)
- Identity Threat Detection & Response (143)
- Our Mission: Be a Force for Good (14)
- Purple Knight (5)
- Semperis University (1)
- The CISO's Perspective (16)
- Threat Research (68)

The Dos and Don’ts of AD Recovery
- Gil Kirkpatrick
Last month I was able to catch up with my long-time friend Guido Grillenmeier, who is currently Chief Technologist at DXC Technology. In 2007-2008, Guido and I worked together, developing and delivering the “Active Directory Masters of Disaster” disaster recovery workshops at the Directory Experts Conference. It was, at the…

Take Back the Keys to Your Kingdom with the Latest Release of Semperis Directory Services Protector
- Darren Mar-Elia | VP of Products
Active Directory is foundational to everything you do and the #1 new target for attackers. Since it wasn’t originally built with today’s threats in mind, Active Directory is riddled with inherent soft spots and risky configurations that attackers are readily taking advantage of. We, here at Semperis, are excited to announce a new release of Directory Services Protector (DS Protector) and the powerful features it includes to detect dangerous vulnerabilities, intercept…
Your Zero Trust Strategy Depends on Active Directory Integrity
- Sean Deuby | Principal Technologist
The exponential increase in remote work caused by the COVID-19 crisis has ricocheted across the IT landscape. Within a matter of days, corporate IT faced an unprecedented 180-degree turn in its client networking model. Organizations that treated remote work as a rare exception suddenly found themselves almost entirely remote. According to JPMorgan, Zoom usage is up more than 300% since before the crises. Microsoft reports a Teams usage increase of 200% since…

Semperis introduces tools to improve security resiliency of Windows Active Directory
- Byron Acohido
Ransomware continues to endure as a highly lucrative criminal enterprise. Ransomware hacking groups extorted at least $144.35 million from U.S. organizations between January 2013 and July 2019. That’s the precise figure recently disclosed by the FBI — the true damage is almost certainly a lot steeper, given only a portion of cyber…

How To Prepare For Cyberwar: It Starts With Identity
- Mickey Bresman
Cyberattacks are rapidly evolving in sophistication and scale. The line between the digital and the physical realm has become more blurred. Foreign cyberattackers have used destructive malware to erase data from hard drives and made moves to infiltrate industrial systems. They could make equally damaging moves in the future, given recent political…
Upgrading to WS2016/2019? Consider a Safety Net for AD
- Sean Deuby | Principal Technologist
A colleague here at Semperis recently looped me into a conversation with the manager of a large Active Directory environment running on Windows Server 2008 R2. With end of support for Windows Server 2008 and 2008 R2 coming up soon (officially January 14, 2020), planning is well underway for upgrade…

Toughen Up Your AD
- Edward Amoroso
Request for Comments (RFC) 1823 from August 1995 introduced the Lightweight Directory Access Protocol (LDAP) Application Programming Interface (API). One could argue that this important work served as the foundation for modern identity management. And yet, surprisingly, the word identity does not appear even once in the entire RFC. (The word directory shows up…
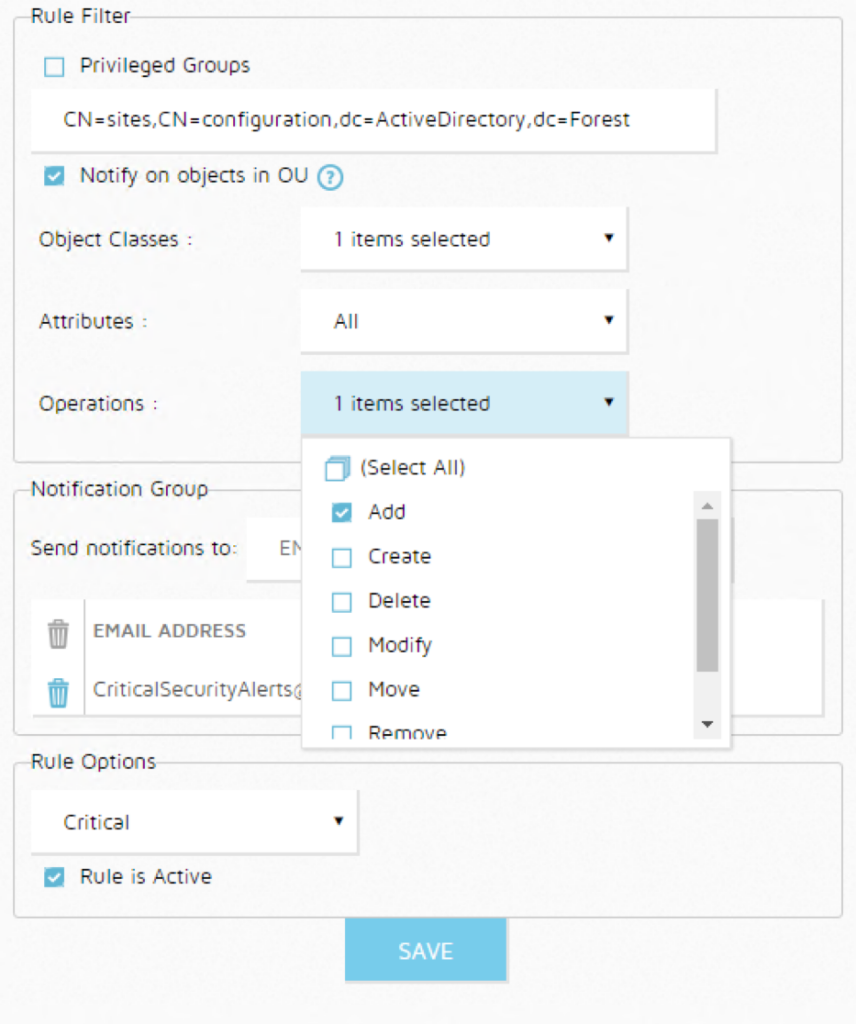
Why Most Organizations Still Can’t Defend Against DCShadow – Part 2
- Darren Mar-Elia | VP of Products
In part 1 of this blog post, I talked about the threat that DCShadow poses to organizations that use Microsoft Active Directory (AD). Here in part 2, I’ll talk about steps you can take to protect your organization. (Quick recap: DCShadow is a feature of the Mimikatz post-exploitation tool that…



