détection et résolution des menaces liées à l'identité
Catégories
- Sauvegarde et récupération d'Active Directory (63)
- Sécurité Active Directory (214)
- Sécurité AD 101 (17)
- Outils communautaires (19)
- Modernisation de l'annuaire (9)
- En première ligne (69)
- Protection de l'identité hybride (68)
- Catalogue des attaques d'identité (29)
- Détection et réponse aux menaces liées à l'identité (143)
- Notre mission : Être une force pour le bien (14)
- Purple Knight (5)
- Université Semperis (1)
- Le point de vue du RSSI (16)
- Recherche sur les menaces (68)

Renforcer la réponse aux incidents cybernétiques avec Forest Druid
- Huy Kha | Architecte principal de l'identité et de la sécurité
Forest Druid est un outil gratuit de découverte des chemins d'attaque pour les environnements d'identité hybrides, tels qu'Active Directory et Entra ID. Contrairement aux outils traditionnels qui cartographient les chemins d'attaque du périmètre externe vers l'intérieur, Forest Druid se concentre sur la protection des actifs les plus critiques en premier lieu. Cette méthode donne la priorité à l'identification et à la sécurisation...

Les nouvelles statistiques sur les ransomwares révèlent un besoin accru de sécurité et de résilience pour Active Directory
- Mickey Bresman
Nous savons tous qu'il est nécessaire d'adopter un état d'esprit de type "assumez la violation" en ce qui concerne les ransomwares et autres cybermenaces. Pour mieux comprendre la nécessité et les défis de cette approche, nous nous sommes associés à la société internationale d'études de marché Censuswide pour interroger les organisations sur leur expérience en matière d'attaques par ransomware. Ce que nous...

Gestion des listes de contrôle d'accès à Active Directory : L'importance de la délégation à plusieurs niveaux
- Daniel Petri | Gestionnaire principal de la formation
Active Directory (AD) joue un rôle essentiel en tant que principal fournisseur d'identité pour de nombreuses organisations à travers le monde, formant l'épine dorsale des systèmes de contrôle d'accès et d'authentification. Cependant, cela fait également de l'environnement Active Directory une cible de choix pour les cyberattaques. Un acteur menaçant qui prend le contrôle de votre Active Directory peut...

Conformité DORA et ITDR
- Daniel Lattimer | Vice-président de zone - EMEA Ouest
Les organisations du secteur des services financiers de l'Union européenne (UE) ont moins d'un an pour démontrer leur conformité à la loi sur la résilience opérationnelle numérique (Digital Operational Resilience Act, DORA). Qu'est-ce que la loi DORA, s'applique-t-elle à votre organisation et comment la conformité DORA s'articule-t-elle avec l'une des principales préoccupations actuelles en matière de cybersécurité : la détection des menaces liées à l'identité et...

Nouveau rapport TEI de Forrester : Semperis réduit les temps d'arrêt de 90 % et fait économiser des millions à ses clients
- Sean Deuby | Technologue principal
Combien de temps votre organisation pourrait-elle rester sans accès aux applications et aux services à cause d'une cyberattaque liée à l'identité ? C'est la question que nous posons souvent aux responsables de la sécurité et des opérations informatiques lorsque nous discutons de l'importance de protéger Active Directory et Entra ID contre les acteurs menaçants. La question semble hypothétique parce qu'elle suppose...

Comment se défendre contre l'injection de l'historique du SID
- Daniel Petri | Gestionnaire principal de la formation
L'injection de l'historique de l'identifiant de sécurité (SID) est un vecteur de cyberattaque sophistiqué qui cible les environnements Windows Active Directory. Cette attaque exploite l'attribut SID History, qui est destiné à maintenir les droits d'accès des utilisateurs lors des migrations d'un domaine à un autre. En injectant des valeurs SID malveillantes dans cet attribut, un attaquant peut...
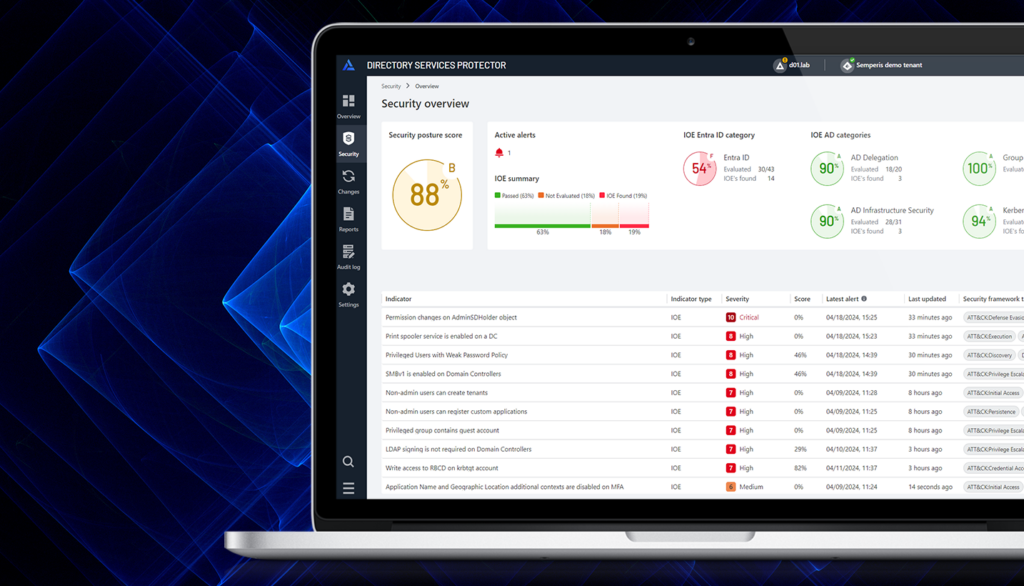
Semperis DSP: Renforcer la protection d'AD et d'Entra ID contre les cyber-menaces
- Eitan Bloch | Chef de produit Semperis
La faille de SolarWinds en décembre 2020 a marqué un changement dans la trajectoire d'attaque des acteurs de la menace. Les cybermenaces ciblent de plus en plus les environnements en nuage des entreprises, généralement Microsoft Entra ID (anciennement Azure AD), puis se déplacent vers Active Directory (AD) sur site - ou vice versa. D'où la question suivante : quel est le niveau de sécurité de votre environnement d'identité hybride ? Quel est le niveau de sécurité de votre environnement d'identité hybride ?

Défense contre les attaques par injection LDAP : Sécurité AD 101
- Daniel Petri | Gestionnaire principal de la formation
L'injection LDAP représente un formidable vecteur de cyberattaque, ciblant les mécanismes d'authentification et d'autorisation au sein de votre environnement Active Directory. En exploitant une mauvaise validation des entrées, les attaquants peuvent manipuler les déclarations LDAP et potentiellement obtenir un accès non autorisé à votre service d'annuaire. Les experts en cybersécurité et en sécurité des identités de Semperis ont une connaissance approfondie de l'injection LDAP,...



