Webinaire

De la table à la réalité : Renforcer la cyber-résilience par des exercices de réponse aux incidents
- Semperis
- 16 mars 2025
Dans le paysage actuel des menaces, la rapidité et l'efficacité de votre réponse aux incidents peuvent faire la différence entre un incident mineur et une violation catastrophique. La question n'est pas de savoir si une cyberattaque se produira, mais quand, et la préparation reste votre meilleure ligne de défense. Les exercices sur table ne sont pas seulement une pratique - ils sont essentiels pour exposer les vulnérabilités,...

Pourquoi votre AD est-il une cible facile pour les pirates informatiques ?
- Semperis
- 28 février 2025
Active Directory (AD) reste une pierre angulaire pour de nombreuses organisations, à la fois sur site et intégré avec Microsoft Entra ID dans le nuage. Il est alarmant de constater que 90 % des cyberattaques ciblent AD, le système d'identité central de la plupart des entreprises. Semperis propose une protection complète pour AD sur site et Entra ID, offrant une défense continue contre les menaces basées sur l'identité avant,...
Surmonter les vulnérabilités grâce à la gestion de la surface d'attaque
- Semperis
- 30 décembre 2024
Alors que le paysage numérique s'étend, la gestion et la sécurisation de la surface d'attaque de votre organisation n'ont jamais été aussi cruciales. Rejoignez-nous pour un webcast sur des sujets brûlants où des experts de l'industrie fourniront une prévision complète des tendances de la gestion de la surface d'attaque (ASM) et offriront des conseils stratégiques pour la fin de 2024 et le début de 2025.....
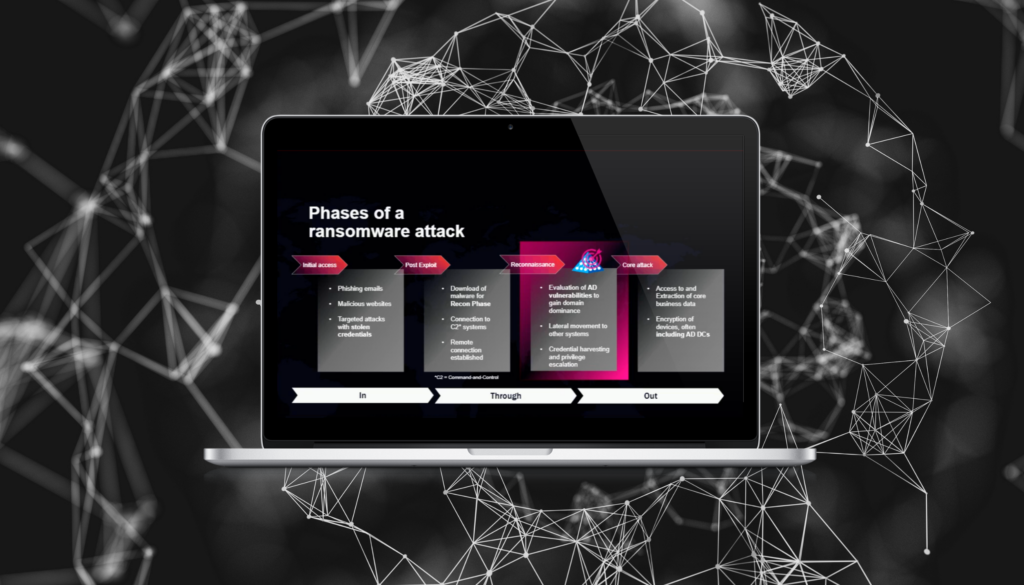
Comment récupérer Active Directory quand chaque seconde compte
- Semperis
- 30 décembre 2024
Microsoft Active Directory (AD) est une cible privilégiée des cyberattaquants. Lorsque l'AD tombe en panne, vos opérations en pâtissent également. Pourtant, la plupart des organisations ne disposent pas d'un plan de reprise spécifique à AD ou s'appuient sur une reprise manuelle, ce qui peut prendre des jours, voire des semaines. L'audit de votre sécurité AD et le maintien d'un plan de réponse aux incidents solide...
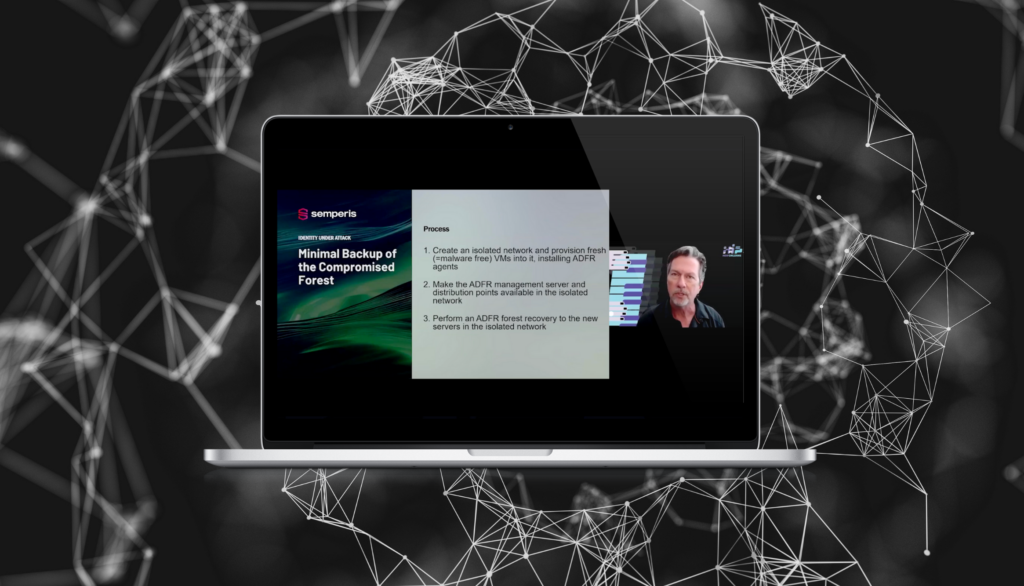
Quand chaque minute compte Récupérer les AD lors d'une attaque
- Semperis
- 28 décembre 2024
Que faites-vous lorsque votre point d'accès ou d'autres protections initiales sont violés ? Que faire lorsque des intrus se trouvent déjà dans votre réseau et ont peut-être compromis votre forêt Active Directory (AD) ? Voici l'histoire vraie d'une attaque de ransomware et de la manière dont elle a été stoppée. Rejoignez Sean Deuby de Semperis, 15 fois...
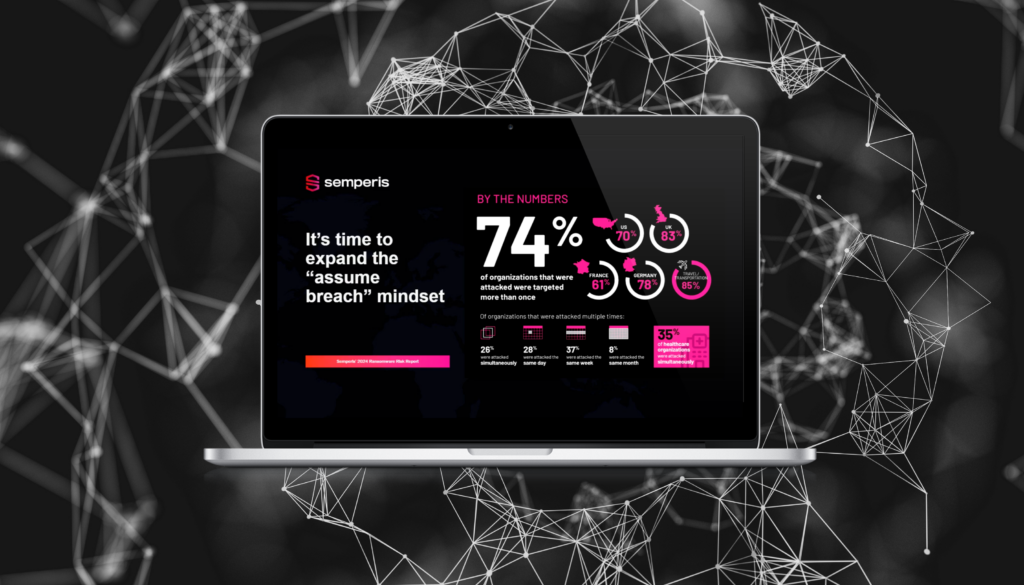
Continuité des activités et rétablissement du système d'identité
- Semperis
- 26 novembre 2024
Votre plan de reprise après sinistre a-t-il été conçu dans une optique de continuité des activités ? À moins qu'il ne comprenne des procédures spécifiques pour la récupération sécurisée d'Active Directory (AD) et d'Entra ID, vous risquez de subir un choc désagréable. La récupération sécurisée du système d'identité est un facteur clé pour déterminer la rapidité avec laquelle votre organisation peut se remettre...
Récupération des opérations après une cyberattaque
- Semperis
- 25 novembre 2024
Les organisations d'infrastructures critiques qui gèrent des systèmes de technologie opérationnelle (OT) ou des dispositifs de l'Internet des objets (IoT) sont confrontées à plusieurs défis pour une cybersécurité efficace, notamment une technologie obsolète, la complexité d'environnements diversifiés et une surface d'attaque accrue. Rob Ingenthron (Senior Solutions Architect, Semperis) aborde les défis auxquels sont confrontées les organisations dans les domaines de la santé, de la fabrication, de l'énergie....
Récupération d'Active Directory : La pièce manquante de votre plan de résilience opérationnelle
- Semperis
- 17 novembre 2024
Les ransomwares et la cybercriminalité sont devenus des menaces de premier plan pour les entreprises de tous les secteurs. Sécuriser les terminaux, souscrire une cyberassurance, voire payer une rançon - aucune de ces options ne peut empêcher une attaque mettant fin à l'activité de l'entreprise. Il existe une mesure essentielle à la résilience opérationnelle et commerciale : Un plan de cybersécurité dédié, axé sur l'identité. Les experts de Government Technology et de Semperis...

Mise en place d'une défense par couches de l'identité
- Semperis
- 11 octobre 2024
Les cyberattaquants sont habiles à trouver des moyens de franchir vos défenses et de pénétrer dans les systèmes d'identité tels qu'Active Directory. De là, ils peuvent se déplacer latéralement, élever leurs privilèges, accéder à des ressources sensibles et injecter des logiciels malveillants ou des ransomwares. La mise en œuvre d'une défense à plusieurs niveaux comprenant la détection et la réponse aux menaces liées à l'identité (ITDR) est essentielle pour protéger vos...
Pas de panique ! Ce n'est qu'un cyberincident
- 26 septembre 2024
À quoi ressemblent les heures qui suivent immédiatement un incident cybernétique présumé ? Dans cet enregistrement, nous abandonnons le jargon et nous plongeons dans la réalité désordonnée et chaotique de la réponse aux incidents. Notre conversation en tête-à-tête comprend des récits de guerre, des leçons apprises et la sagesse durement gagnée en menant des organisations à travers le feu. Nous nous retirons...



