Segurança do Active Directory
Categorias
- Backup e recuperação do Active Diretory (63)
- Segurança do Active Diretory (215)
- Segurança AD 101 (17)
- Ferramentas comunitárias (19)
- Modernização de directórios (9)
- Da linha da frente (69)
- Proteção da identidade híbrida (68)
- Catálogo de ataques de identidade (29)
- Deteção e Resposta a Ameaças de Identidade (144)
- A nossa missão: Ser uma força para o bem (14)
- Purple Knight (5)
- Universidade Semperis (2)
- A perspetiva do CISO (16)
- Investigação sobre ameaças (68)

Vigilância de ataques de identidade: AD Security News, maio de 2024
- Equipa de investigação da Semperis
À medida que os ciberataques que visam o Active Directory continuam a aumentar, as equipas de segurança, identidade e TI do AD enfrentam uma pressão crescente para monitorizar o cenário de ameaças em evolução centrado no AD. Para ajudar os profissionais de TI a compreender e prevenir ataques que envolvam o AD, a equipa de investigação da Semperis publica um resumo mensal de ciberataques recentes e fornece informações adicionais...

Novo relatório TEI da Forrester: A Semperis reduz o tempo de inatividade em 90%, poupando milhões aos clientes
- Sean Deuby | Tecnólogo principal
Quanto tempo sua organização poderia ficar sem acesso a aplicativos e serviços por causa de um ataque cibernético relacionado à identidade? Essa é a pergunta que frequentemente fazemos aos líderes de segurança e de operações de TI quando discutimos a importância de proteger o Active Directory e o Entra ID contra agentes de ameaças. A pergunta parece hipotética porque pressupõe...

Como se defender contra a injeção de histórico SID
- Daniel Petri | Gestor de formação sénior
A injeção do Histórico do Identificador de Segurança (SID) é um vetor de ciberataque sofisticado que visa ambientes Windows Active Directory. Este ataque explora o atributo SID History, que se destina a manter os direitos de acesso dos utilizadores durante as migrações de um domínio para outro. Ao injetar valores SID maliciosos neste atributo, um atacante pode escalar...

Identity Attack Watch: AD Security News, abril de 2024
- Equipa de investigação da Semperis
À medida que os ciberataques que visam o Active Directory continuam a aumentar, as equipas de segurança, identidade e TI do AD enfrentam uma pressão crescente para monitorizar o cenário de ameaças em evolução centrado no AD. Para ajudar os profissionais de TI a compreender e prevenir ataques que envolvam o AD, a equipa de investigação da Semperis publica um resumo mensal de ciberataques recentes e fornece informações adicionais...
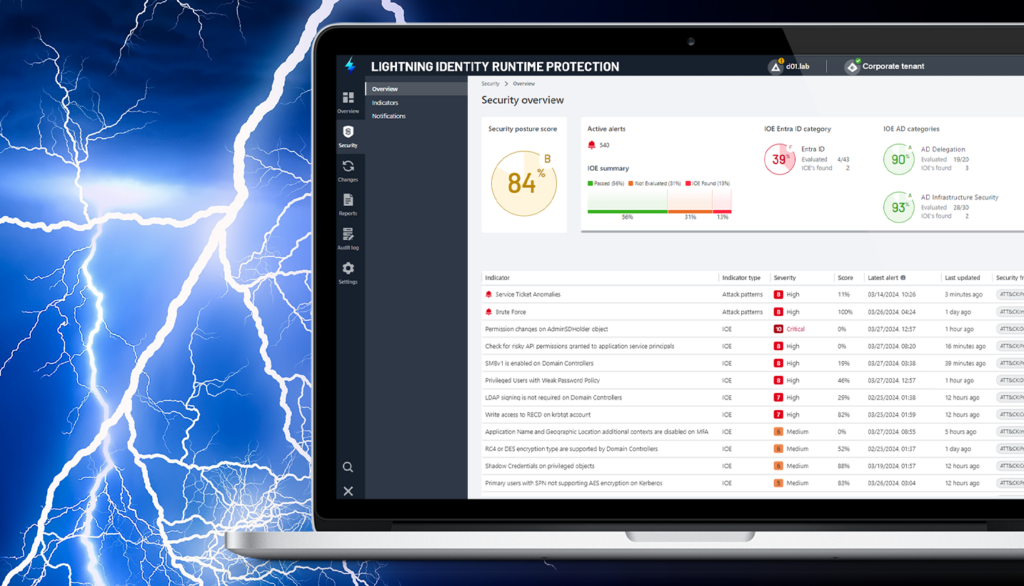
Apresentando o Lightning Identity Runtime Protection: Deteção com tecnologia de IA dos padrões de ataque de identidade mais bem-sucedidos
- Eitan Bloch | Gestor de Produto Semperis
Muitos ciberataques passam despercebidos até que os danos estejam feitos, apesar dos esforços das organizações para os evitar. E muitos ataques de identidade bem sucedidos utilizam as mesmas técnicas testadas e comprovadas que têm funcionado durante anos, como a pulverização de palavras-passe e os ataques de força bruta. A Microsoft estima que os ataques de pulverização de palavras-passe são responsáveis por mais de um terço...

Identity Attack Watch: AD Security News, março de 2024
- Equipa de investigação da Semperis
À medida que os ciberataques que visam o Active Directory continuam a aumentar, as equipas de segurança, identidade e TI do AD enfrentam uma pressão crescente para monitorizar o cenário de ameaças em evolução centrado no AD. Para ajudar os profissionais de TI a compreender e prevenir os ataques que envolvem o AD, a equipa de investigação da Semperis publica um resumo mensal dos ciberataques recentes. Na edição deste mês...

Defesa contra ataques de injeção de LDAP: Segurança do AD 101
- Daniel Petri | Gestor de formação sénior
A injeção de LDAP representa um formidável vetor de ciberataque, visando os mecanismos de autenticação e autorização no seu ambiente Active Directory. Ao explorar uma validação de entrada inadequada, os invasores podem manipular declarações LDAP e, potencialmente, obter acesso não autorizado ao seu serviço de diretório. Os especialistas em segurança cibernética e de identidade da Semperis têm um profundo conhecimento da injeção de LDAP,...

Identity Attack Watch: AD Security News, fevereiro de 2024
- Equipa de investigação da Semperis
À medida que os ciberataques que visam o Active Directory continuam a aumentar, as equipas de segurança, identidade e TI do AD enfrentam uma pressão crescente para monitorizar o cenário de ameaças em evolução centrado no AD. Para ajudar os profissionais de TI a compreender e prevenir os ataques que envolvem o AD, a equipa de investigação da Semperis publica um resumo mensal dos ciberataques recentes. Na edição deste mês...



