Proteção de identidade híbrida
Categorias
- Backup e recuperação do Active Diretory (63)
- Segurança do Active Diretory (215)
- Segurança AD 101 (17)
- Ferramentas comunitárias (19)
- Modernização de directórios (9)
- Da linha da frente (69)
- Proteção da identidade híbrida (68)
- Catálogo de ataques de identidade (29)
- Deteção e Resposta a Ameaças de Identidade (144)
- A nossa missão: Ser uma força para o bem (14)
- Purple Knight (5)
- Universidade Semperis (2)
- A perspetiva do CISO (16)
- Investigação sobre ameaças (68)
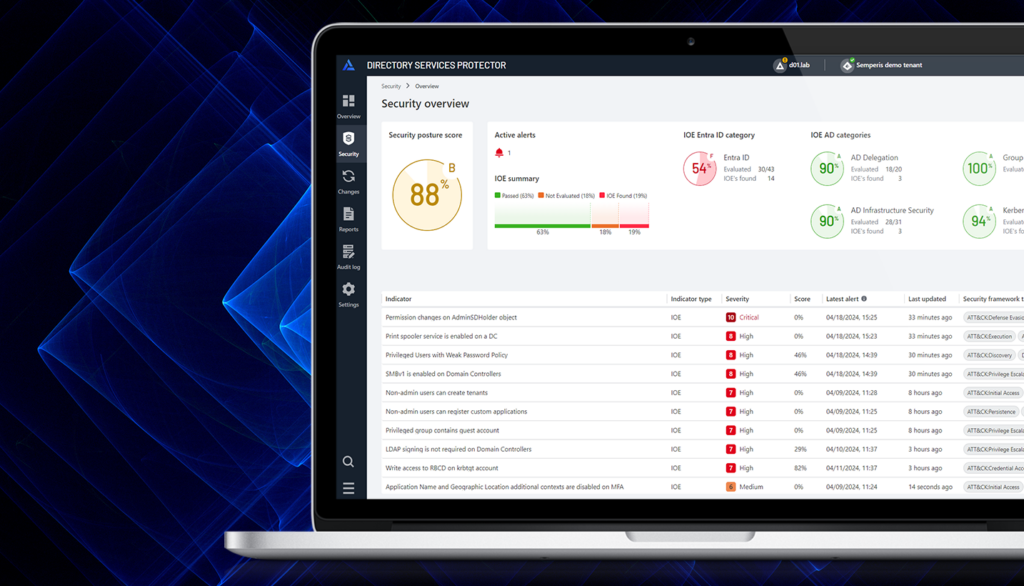
Semperis DSP: Reforçar a proteção do AD e do Entra ID contra ameaças cibernéticas
- Eitan Bloch | Gestor de Produto Semperis
A violação da SolarWinds em dezembro de 2020 significou uma mudança no caminho de ataque para os agentes de ameaças. As ameaças cibernéticas visam cada vez mais os ambientes de nuvem das organizações, normalmente o Microsoft Entra ID (anteriormente Azure AD), e depois passam para o Active Directory (AD) local - ou vice-versa. Isso levanta a questão: Quão seguro é o seu ambiente de identidade híbrida...

Conheça o Silver SAML: Golden SAML na nuvem
- Tomer Nahum e Eric Woodruff
Principais conclusões O Golden SAML, uma técnica de ataque que explora o protocolo de início de sessão único SAML, foi utilizado como uma exploração pós-violação, agravando o devastador ataque da SolarWinds de 2020 - uma das maiores violações do século XXI. O ataque SolarWinds à cadeia de abastecimento afectou milhares de organizações em todo o mundo, incluindo os EUA....
Como se defender contra um ataque do tipo "Overpass the Hash
- Daniel Petri | Gestor de formação sénior
No cenário em constante evolução das ciberameaças, o ataque Overpass the Hash é um vetor potente. Tirando partido do protocolo de autenticação NTLM, este ataque permite aos adversários contornar a necessidade de palavras-passe em texto simples. Em vez disso, um ataque Overpass the Hash utiliza o hash de um utilizador para autenticar e potencialmente aumentar os privilégios. Como...
MFA para o Active Directory: Uma visão geral
- Sean Deuby | Tecnólogo principal
A segurança da informação moderna assenta numa defesa em camadas. Cada camada suporta as outras e apresenta obstáculos adicionais aos agentes de ameaças. Da gestão de patches às firewalls de perímetro, cada camada torna mais difícil para os atacantes comprometerem a sua rede. A autenticação multifator (MFA) é uma dessas camadas. A MFA tem muitas...

Os dez principais erros de segurança cibernética da NSA: Uma perspetiva do Active Directory (Parte 3)
- Daniel Petri | Gestor de formação sénior
Bem-vindo à última parte desta série que discute as dez principais configurações incorrectas de segurança cibernética da CISA e da NSA no contexto de ambientes híbridos do Active Directory. O Active Directory é o sistema de identidade da maioria das organizações: uma parte crítica da sua infraestrutura e um alvo principal para os ciberataques. Esta semana, discutirei os...

Os dez principais erros de segurança cibernética da NSA: Uma perspetiva do Active Directory (Parte 2)
- Daniel Petri | Gestor de formação sénior
Quando se trata de segurança cibernética - especialmente a segurança da infraestrutura de identidade crítica - a expetativa mínima para cada organização deve ser fechar as vulnerabilidades conhecidas e as lacunas de configuração. Bem-vindo à segunda das nossas três partes de discussão sobre como a lista dos dez principais erros de configuração de segurança cibernética da CISA e da NSA se aplica a ambientes híbridos do Active Directory e...
Os dez principais erros de segurança cibernética da NSA: Uma perspetiva do Active Directory
- Daniel Petri | Gestor de formação sénior
No final do ano passado, a Agência de Segurança Nacional dos Estados Unidos (NSA) e a Agência de Segurança Cibernética e de Infra-estruturas (CISA) publicaram uma lista das vulnerabilidades mais comuns nas grandes redes informáticas. Esta lista das dez principais configurações incorrectas de cibersegurança da CISA e da NSA revela fraquezas sistémicas, particularmente no Microsoft Windows (embora não limitado a ele)...

4 razões para aumentar a capacidade de recuperação dos recursos da Entra ID
- Tuna Gezer
Neste momento, é sabido que os ciberataques consideram o Active Directory o seu alvo favorito. O AD - o principal repositório de identidades para 90% das empresas em todo o mundo - foi criado para uma autenticação de utilizador e gestão de acesso eficientes, mas muitos ambientes antigos do AD no local têm configurações erradas e arriscadas que se acumularam ao longo do tempo. Ao explorar as lacunas de segurança do AD, os atacantes...



