From the Front Lines
Categories
- Active Directory Backup & Recovery (62)
- Active Directory Security (213)
- AD Security 101 (17)
- Community Tools (19)
- Directory Modernization (9)
- From the Front Lines (69)
- Hybrid Identity Protection (68)
- Identity Attack Catalog (27)
- Identity Threat Detection & Response (143)
- Our Mission: Be a Force for Good (14)
- Purple Knight (5)
- Semperis University (1)
- The CISO's Perspective (16)
- Threat Research (68)

Hafnium Attack Timeline
- Sean Deuby | Principal Technologist
The attacks on Microsoft Exchange servers around the world by Chinese state-sponsored threat group Hafnium are believed to have affected over 21,000 organizations. The impact of these attacks is growing as the four zero-day vulnerabilities are getting picked up by new threat actors. While the world was introduced to these…

Leading CISOs Discuss Shifting Priorities Amidst Increased Security Threats
- Semperis Team
What keeps CISOs up at night? And where should CISOs focus to bring value to the business? How should priorities shift given the proliferation of cyberattacks that threaten to disrupt businesses worldwide? To help cut through some of the noise, we partnered with Redmond Magazine to convene leading CISOs in a discussion…

CISA’s Ransomware Guidance Is Reminder to Include AD in Recovery Plan
- Semperis Team
Any ransomware recovery plan needs to include regular file backups and encrypted data with offline copies, as the Cybersecurity and Infrastructure Security Agency (CISA) recently reminded as part of the organization’s campaign to drive awareness of its ransomware guidance and resources. The guidance includes best practices and checklists to help…

Hybrid Identity Protection (HIP) Predictions for 2021
- Thomas Leduc
2020 was a hugely disruptive year across the globe. And while cybersecurity may have been background noise to a world tuned to health and financial issues, widespread cyberattacks have left reverberations that will be felt for years to come. We asked expert speakers from the recent Hybrid Identity Protection (HIP) Conference to share a brief look back at what happened in 2020 and what they're focusing on in the year ahead as…

NotPetya Flashback: The Latest Supply-Chain Attack Puts Active Directory at Risk of Compromise
- Chris Roberts
Last week, news broke that a sophisticated adversary penetrated FireEye's network and stole the company's Red Team assessment tools. The attack is reportedly linked to a larger supply-chain assault that struck government, consulting, technology, and telecom organizations throughout North America, Europe, Asia, and the Middle East. To get an idea of what this stolen toolset…
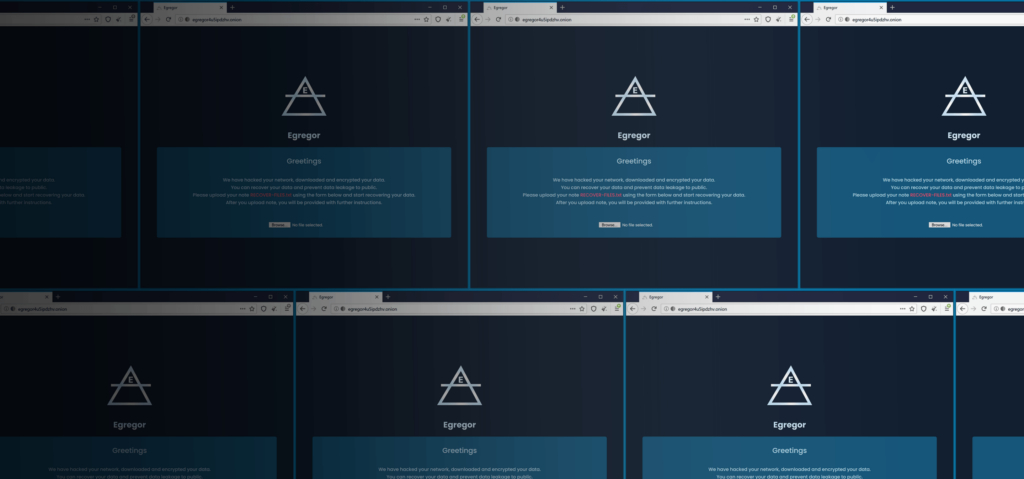
Egregor Ransomware Attack on Kmart is a Reminder that Active Directory Needs to Be Protected and Recoverable
- Darren Mar-Elia | VP of Products
The latest ransomware-as-a-service attack leaves the well-known retailer, Kmart, with service outages and a compromised Active Directory. In the wake of Maze ransomware "retiring" last month, many of its affiliates have moved to the new kid on the ransomware block, Egregor. Named after an occult term meaning the collective energy or force…

The Stakes Are Higher in Healthcare: Fighting Cybercrime During a Pandemic
- Gil Kirkpatrick
In the healthcare industry, cybersecurity issues have consequences that go well beyond the loss of data. Recently, the FBI and other federal agencies warned of a credible threat of "increased and imminent cybercrime" to U.S. hospitals and healthcare providers. Criminal groups target the healthcare sector to carry out "data theft…

From Sandworm to a Safer Tomorrow: Lessons from Hybrid Identity Protection 2020
- Thomas Leduc
Four days, 23 speakers and 1576 attendees later, the third annual Hybrid Identity Protection 2020 (HIP) conference has come to a close. And despite being all virtual for the first time, this year’s event was one of the most powerful to date. Day 1 – Crisis Management Just 24 hours…



