Webinar
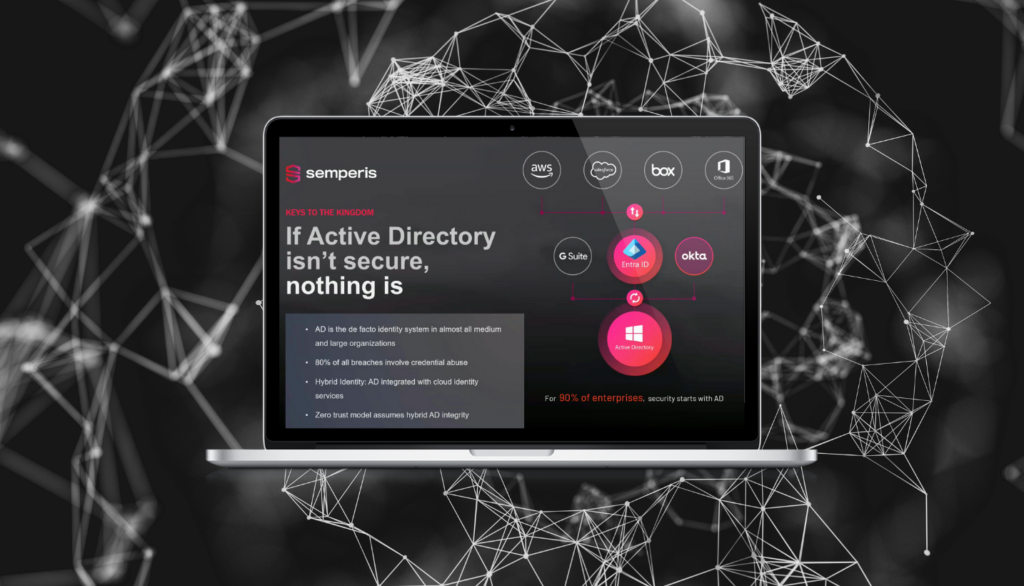
Proteger e recuperar o Active Directory de um ataque cibernético
- Semperis
- 25 de agosto de 2024
Os ciberataques contra agências governamentais estatais e locais, bem como contra infra-estruturas públicas críticas, aumentaram muito nos últimos anos. A sua estratégia de cibersegurança está preparada para os atacantes actuais? Desde encontrar formas de ultrapassar a MFA até se esconderem das soluções SIEM e dos registos de segurança, os agentes de ameaças tornaram-se hábeis a contornar...

Resiliência cibernética 101: Principais dicas para a defesa do Active Directory
- Semperis
- 14 de julho de 2024
Um sistema de identidade seguro é a base da sua arquitetura Zero Trust. É por isso que os atacantes visam regularmente o Microsoft Active Directory (AD) e o Entra ID. A obtenção do controlo destes sistemas de identidade pode dar aos agentes de ameaças o controlo quase total de todos os seus sistemas, o acesso a dados sensíveis e os meios para devastar a sua...

Proteger o AD: a base da sua estratégia de identidade de confiança zero
- 18 de junho de 2024
Os ciberataques são a ameaça mais crítica que as tecnologias da informação modernas enfrentam. A maioria dos ataques começa com o comprometimento da identidade. Durante o último quarto de século, a identidade na empresa tem sido sinónimo de Microsoft Active Directory (AD). Por conseguinte, o AD está quase sempre envolvido num ciberataque, quer como alvo, quer como um caminho para...

Para o inferno e de volta: Recuperação do Active Directory durante um ataque
- Semperis
- 01 de junho de 2024
O que faz quando o seu endpoint ou outras protecções iniciais são violadas? Quando os intrusos já estão na sua rede e até comprometeram a sua floresta do Active Directory (AD)? Esta é a verdadeira história de um ataque de ransomware - e como ele foi interrompido. Junte-se ao tecnólogo principal da Semperis e ex-aluno do MVP, Guido...

Defesa do sistema de identidade para o sector da saúde
- Semperis
- 30 de abril de 2024
Os ciberataques têm os sistemas de saúde na mira. Ao violar sistemas de identidade, como o Active Directory e o Entra ID, os atacantes podem comprometer rapidamente a infraestrutura operacional vital e os dados confidenciais em toda a organização de saúde. Proteger a infraestrutura de identidade é um passo fundamental para frustrar os agentes de ameaças. Junte-se a Marty Momdjian, EVP da Semperis de...
Segurança do Active Directory para petiscar: 30 minutos por dia mantêm os maus da fita afastados
- Semperis
"Simplesmente não tenho tempo para lidar com o Active Directory." Quantas vezes é que já ouviu (ou disse) isso? Limpar anos de desvios na configuração do AD e de dívidas tecnológicas pode ser uma tarefa assustadora... mas não tão desagradável como tentar recuperar o sistema de identidade depois de um...
A minha identidade híbrida foi destruída - e agora?
- Semperis
O lema "a TI de hoje é híbrida" é uma norma mais antiga na gestão de TI e nos parceiros da Nuvem. A nova arquitetura de referência de segurança da Microsofts é híbrida e considera a nuvem como "fonte de segurança". No entanto, as ameaças são muito graves, quando a identidade híbrida é comprometida. Isso traz problemas como falhas no Single Sign-On,...
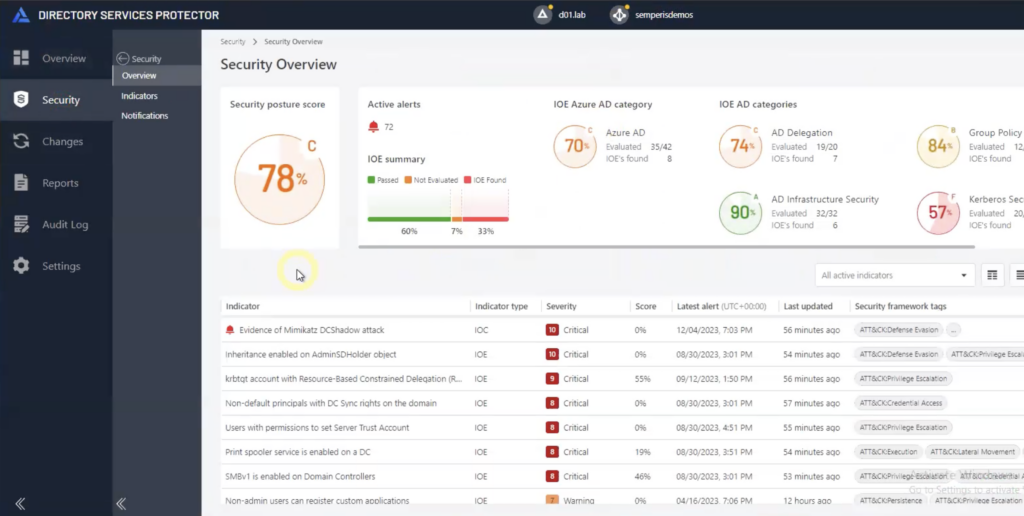
Proteger e recuperar AD e Entra ID - As chaves do reino
- Semperis
Neste webinar a pedido, Rob Ingenthron, Arquiteto de Soluções Sénior da Semperis, irá aprofundar a importância da proteção e recuperação do AD na deteção e resposta a ameaças à identidade (ITDR). Os participantes podem esperar: Descobrir estratégias eficazes para integrar a proteção e a recuperação do AD em uma abordagem abrangente de ITDR. Obter uma compreensão mais profunda...
Está preparado para a verdadeira catástrofe do AD?
Explore o papel vital da identidade no planeamento da recuperação de desastres, centrando-se especificamente no Microsoft Active Directory. Este webinar a pedido aborda os desafios na recuperação de serviços de diretório essenciais e enfatiza a necessidade de um planeamento proactivo. As principais conclusões incluem a reavaliação dos procedimentos de DR, o envolvimento com fornecedores de ITDR e o aprimoramento da segurança de identidade. O webinar...

Fundamentos da segurança do Active Directory em um ambiente híbrido
O Active Directory (AD) é e continua a ser uma solução de gestão, seja no local ou como Azure AD na nuvem. No Web-Seminário da Semperis, Inc., o especialista em AD, Guido Grillenmeier, explica os riscos e as possibilidades do AD. Desde há mais de dois anos que o Microsoft Active Directory (AD) é o método de autenticação de facto que permite às empresas autenticarem-se...



