Victims Hit Multiple Times, 78% Paid Ransom
A global study of 900 IT and security professionals reveals that 74% of organizations targeted by ransomware were attacked multiple times, and 78% of victim organizations paid ransom, pointing to a cycle of breaches that cause escalating damage in revenue losses, operational cost, and—in some cases—human health and safety.
Alarming attack frequency, severity, and consequences
Ransomware, once a sporadic menace, has evolved into an unrelenting adversary.
Criminal groups orchestrate multiple strikes in rapid succession, exploiting vulnerabilities across organizations. Critical systems, including Microsoft Active Directory, are a top attack target.
The 2024 Ransomware Risk Report reveals concerning statistics for business, IT, and security leaders.
Coming to terms with ransomware
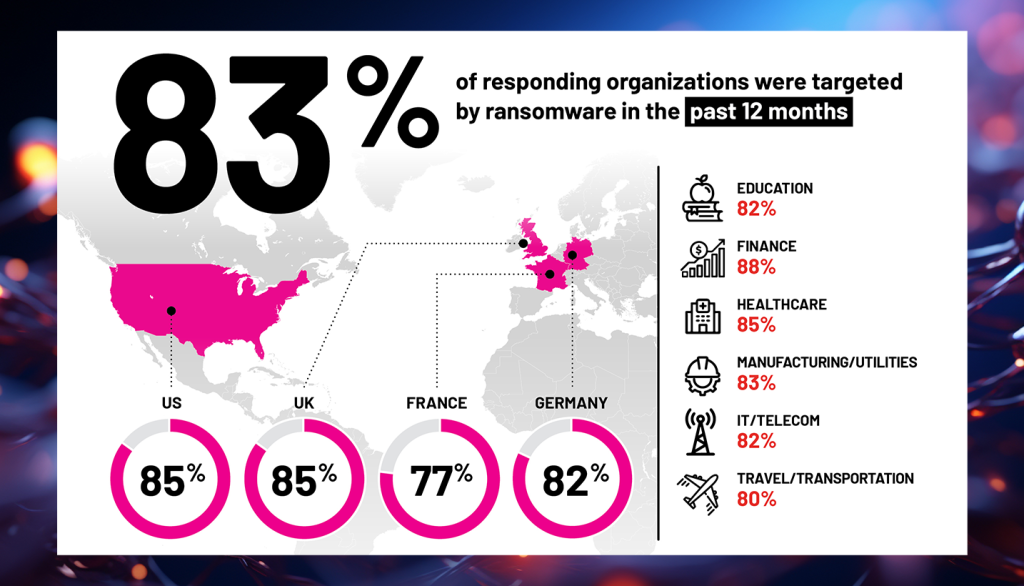
Companies are suffering successful ransomware attacks multiple times within the same year—resulting in closures, layoffs, loss of revenue and customer trust, and cancelation of cyber insurance.
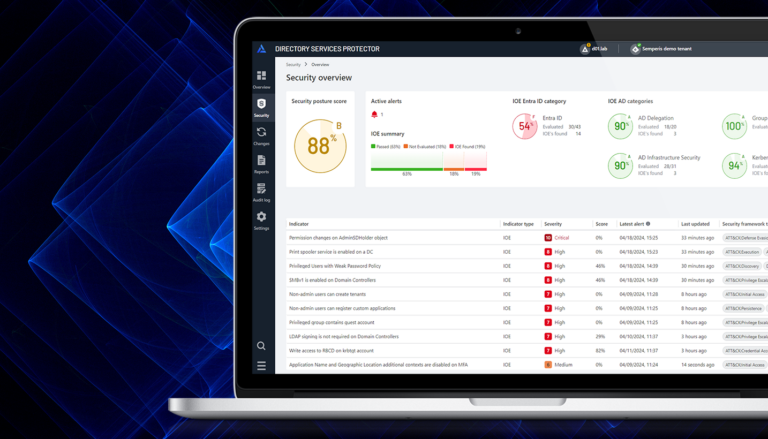
of companies were attacked by ransomware not once, but multiple times—54% on the same day, and most within the span of a week.
of targeted organizations paid the ransom—72% paid multiple times, and 32% paid 4 times or more.
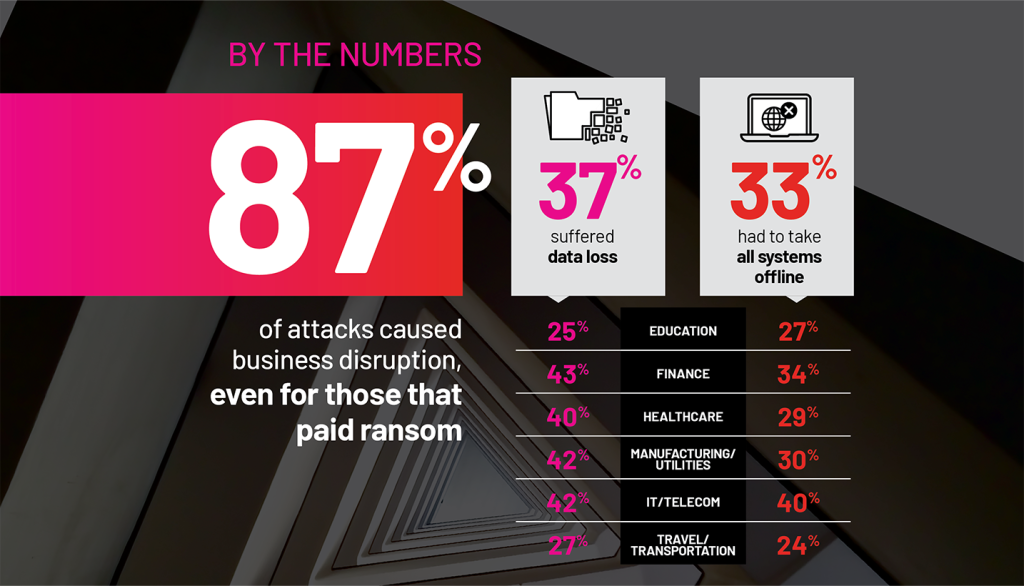
Attacks cause data loss and business outages, even for victims with general backups
Ransomware attacks cause widespread and pervasive disruption, even for organizations that have general backups in place. Attackers are breaching systems through embedded operating systems, outdated technology that hasn’t had regular security updates, and long-forgotten backdoors.
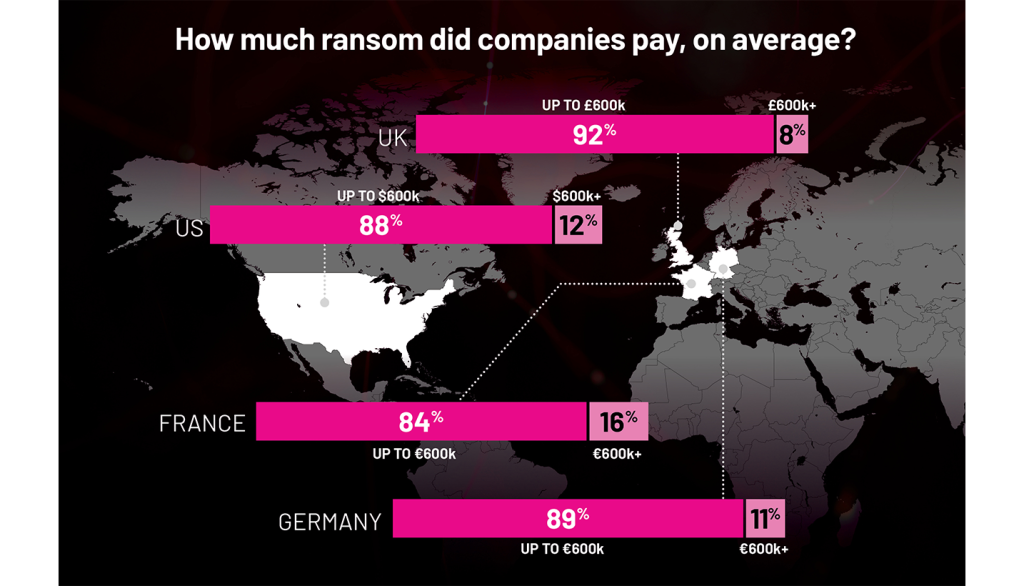
Can companies say “no” to ransomware?
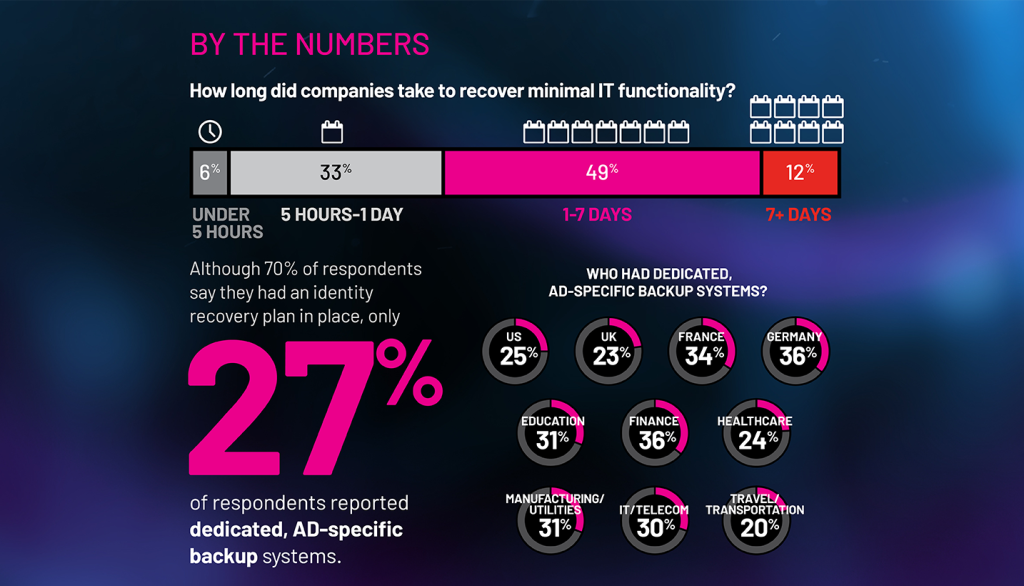
Although 70% of respondents had an identity recovery plan in place, only 27% of respondents had dedicated, AD-specific backup systems. 61% of ransomware victims required more than a day to recover minimal IT functionality, extending business disruptions.
of victims paid ransom multiple times
paid ransom 4 times or more
Why did companies pay ransom?
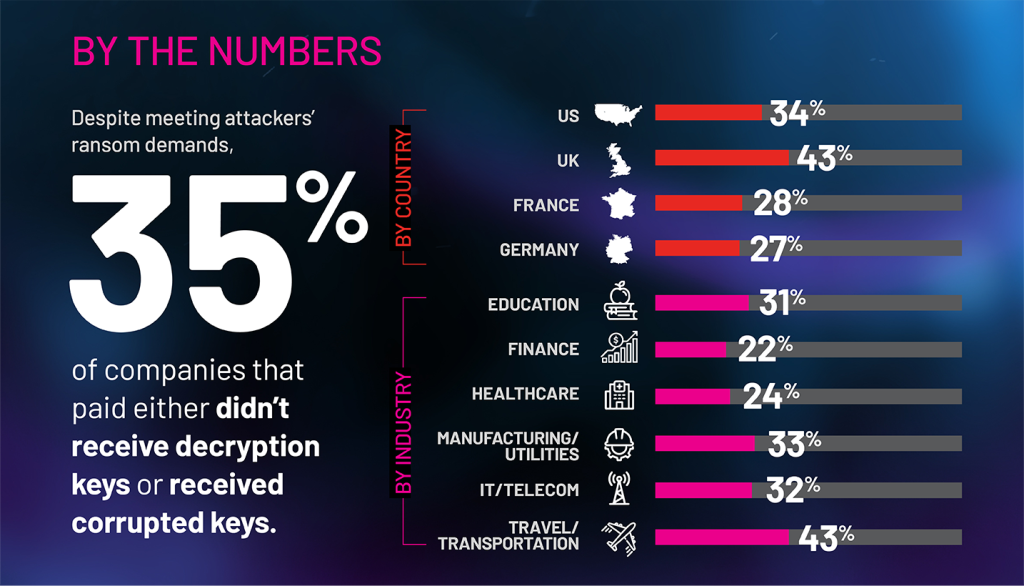
Many respondents noted a desire to return to normal business as quickly as possible as a reason for paying ransom. Others, especially those in the IT/telecom industry, paid because they had cyber insurance to defray the costs. Still others considered the threat to patients, customers, their business, or their reputation to be worth the price of ransom. Unfortunately, ransom payment does not guarantee the receipt of usable decryption keys. Furthermore, attackers often use ransomware to deliver malware that can reinfect systems or cause other damage.
The true cost of ransomware
In any complex organization, security budget, staffing, and resource decisions are a balancing act. However, in the case of ransomware, executive leadership might be making those decisions without a complete understanding of the potential costs after an attack. Ransom payment does not guarantee the receipt of usable decryption keys. Furthermore, attackers often use ransomware to deliver malware that can reinfect systems or cause other damage. A successful attack typically costs much more than a ransom payment.
Ransomware attacks cause collateral damage far beyond the ransom payment
The ransom payment itself is only the beginning of the costs incurred from a ransomware attack.
“The cost of the ransom payment is not the sum total of the actual damage,” says Semperis CEO Mickey Bresman. “Certain attacks aren’t money-driven; rather they are aimed at causing chaos and disruption. In addition, the money that you pay is being used for other criminal activities, like human trafficking, drugs, and weapons.”
Chris Inglis noted that a ransomware attack is not a one-time or limited-time event that you can quickly address and then move on from.
“This is a life-changing event that has enduring, lingering effects. Loss of customer trust, loss of cyber insurance, regulatory prosecution … that scrutiny never goes away.”
Few companies maintain dedicated identity protection
The identity system, particularly Active Directory, is now the security perimeter for enterprise organizations. The digitization of the modern enterprise has eliminated the idea of a defensible perimeter, creating a complex landscape for security professionals—and a broad attack surface for cyber criminals. Without AD-specific, malware-free backups, and a tested cyber-specific recovery plan, recovery will be prolonged, increasing the chance that the organization will decide to pay ransom to restore business operations.
Why aren’t organizations prioritizing ransomware defense?
Organizations face multiple challenges in putting a layered ransomware defense strategy in place. Most respondents reported that their biggest hurdle to resilience was lack of support from the board of directors.
Chris Inglis notes that effective cybersecurity requires a three-pronged approach comprising corporate doctrine, skill building, and technology.
First step: Explain the value of identity-first security in business terms
“Technology can help us analyze and assess what’s happening, moment by moment,” Inglis says. “It can help us respond more quickly and recover more quickly. But the thing that is most wanting now is a collective realization that we all have a part to play. That starts with the board, not with the IT shop. The board is accountable; the SEC has made that clear. Regulations are increasingly making it clear: cybersecurity is a business issue.”
More resources
Learn more about how to prevent, detect, and respond to identity-based attacks.