
86% of Victims Targeted on Weekend, Holiday
Ransomware attackers tend to strike when defenses are weakest, including periods when staffing is most likely to be reduced.
Striking gap in ransomware defenses
Despite widespread cybersecurity efforts, many organizations are unintentionally opening a door to ransomware by reducing their defenses during weekends and holidays. Attackers clearly expect this behavior and target these periods — as well as other material corporate events that might signal distracted or reduced defenses — to strike.
Organizations that aim to strengthen their cyber defenses can use this information to their advantage. Implementing robust, automated protection and recovery solutions for the identity infrastructure can help to foil ransomware attempts, even during times of corporate upheaval or when human resources are scarce.
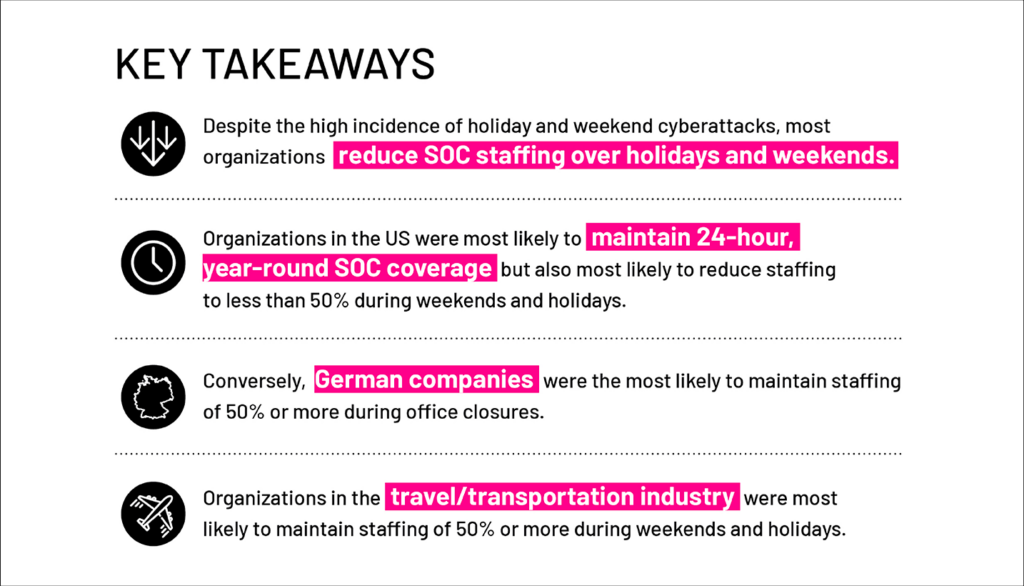
Attackers strike when SOC staffing is reduced
Most of the organizations included in our study (96%) said their SOC operates 24/7/365, through some combination of internal and external resources. Even so, the majority of global companies (85%) scale back on their after-hours SOC staffing levels by up to 50%. And alarmingly, nearly 5% of respondents indicated that their SOC is not staffed at all during holidays or weekends.
of global companies scale back on their after-hours SOC staffing levels by up to 50%
of respondents said their SOC is not staffed at all during holidays or weekends

Attacks occur during times of corporate distraction
Times of corporate upheaval — whether a merger, acquisition, IPO, or reduction in workforce — are also magnets for ransomware attackers. Semperis’ survey data show that a majority (63%) of respondents also experienced a ransomware attack following a material corporate event. Not only do these situations create the distractions that bad actors love to exploit, but attackers can often extract large ransoms from companies desperate to regain access to critical systems or prove operational competence ahead of a major transaction. In addition, such events create inherent identity security challenges.
More resources
Learn more about how to prevent, detect, and respond to identity-based attacks.











